Threat Remediate

Streamlining Log Management with LogIngest: A Game-Changer for Cybersecurity
Embrace the future: upgrade your siem with vijilan’s cloud integration, unveiling logalert: elevate your security with vijilan’s advanced siem solution, strengthening microsoft 365 security with impossible travel rules.
As more and more businesses are moving towards cloud-based services, Microsoft 365 has become an increasingly popular option for organizations to manage their productivity and collaboration tools. However, with the rise of cloud-based services, new security challenges have also emerged. One such challenge is the risk of unauthorized access to a user’s account, which can be mitigated with the use of Microsoft 365 Impossible Travel Rules.
Microsoft 365 Impossible Travel Rules is a feature that can detect and prevent unauthorized access to user accounts by flagging any login attempts that appear to be impossible. This feature can be a powerful tool for organizations that want to ensure the security of their data and prevent unauthorized access to their accounts.
So, what exactly are the Microsoft 365 impossible travel rules?
In essence, Impossible Travel Rules are a security feature that monitors login attempts to Microsoft 365 accounts and identifies any attempts that are geographically impossible. This means that if a user logs into their account from New York and then attempts to log in from London within a very short period, Impossible Travel Rules will flag this activity as impossible.
This type of activity can indicate that someone is attempting to access the account without the user’s knowledge or permission. The feature can also detect attempts to log in from two different locations that are geographically impossible to travel between in the time frame that the attempts were made. For example, if a user logs in from New York and then attempts to log in from Sydney within a short period, Impossible Travel Rules will flag this activity as impossible.
What are the benefits of using impossible travel rules?
Using impossible travel rules can be a valuable security measure for businesses, as it provides an extra layer of protection against unauthorized access to user accounts. Here are some of the key benefits of using this feature:
- Detecting unauthorized access: Impossible Travel Rules can help detect any attempts to access a user’s account from unauthorized locations, preventing data breaches and unauthorized access.
- Alerting users of suspicious activity: Users can be notified of suspicious activity through email or in-app alerts, providing them with the opportunity to take action and secure their accounts.
- Compliance with regulations: Certain regulations, such as the General Data Protection Regulation (GDPR), require businesses to take appropriate measures to secure user data. Implementing impossible travel rules can help businesses meet these compliance requirements.
- Customizable settings: The feature allows organizations to customize settings, such as the time frame for which logins are flagged as impossible, to suit their specific security needs.
How to enable Impossible Travel Rules?
Enabling Impossible Travel Rules is relatively straightforward. Here are the steps to follow:
- Sign in to the Microsoft 365 admin center.
- Go to the Security and Compliance Center.
- Select ‘Policies’ from the left navigation menu.
- Click on ‘Azure AD Conditional Access.’
- Click on ‘New Policy’ to create a new policy.
- Give your policy a name and description.
- Select ‘Users and groups’ to specify who the policy applies to.
- Select ‘Cloud apps or actions’ and choose ‘Office 365 Exchange Online.’
- Scroll down to ‘Conditions’ and select ‘Sign-in risk.’
- Set ‘Sign-in risk’ to ‘High.’
- Scroll down to ‘Access controls’ and select ‘Grant.’
- Select ‘Block access’ and choose ‘Impossible travel.’
- Save your policy.
As businesses continue to rely on cloud-based services such as Microsoft 365, security risks will continue to be a concern. However, features like Impossible Travel Rules can help mitigate the risk of unauthorized access to user accounts. By enabling this feature, businesses can strengthen their security posture and protect their data from potential breaches. Contact Vijilan Security today to learn more about how we can help your organization stay secure and resilient against cyber threats.

Vijilan Security
- October 20, 2023
Related insights

5 Benefits Of A Cloud Computing Security Solution

7 Types Of Cyber Security Threats

Digital Security Tips and Solutions

Want to contact us?
Contact information.
+1 (954) 334-9988 [email protected] 20803 Biscayne Blvd 302 Aventura, Florida 33180
Become a partner

Become a partner today
Vijilan’s Portal is your gateway to access all the products and services that are available from Vijilan.
- Privacy Overview
- Strictly Necessary Cookies
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.

- Why Daymark
- Testimonials
- Technical Certifications
- Industry Awards
- Daymark Solutions Charitable Trust
- Privacy Policy
- Energy & Utilities
- Financial Services
- Life Sciences
- Cloud Solutions
- CMMC Compliance Readiness
- Data Center Infrastructure
- Data Protection
- Networking & Security
- Virtualization
- Assessment & Health Checks
- Cloud Services
- Contract & Maintenance Management
- Documentation & Knowledge Transfer
- Implementation
- Proof of Concept
- Solution Architecture
- Staging and Integration
- Support Center
- Support Services
- Cloud Partners
- GCC High Roadmap
- Microsoft 365
- Microsoft Azure
- Case Studies
- Data Sheets
- Partner Resources
- News & Events

Information Technology Navigator
Tips, advice & insights from technology pros, understanding office 365 impossible travel.
Posted by Corey Roberts
Tue, Feb 21, 2023

Impossible Travel is a security component of Microsoft Cloud App Security, providing advanced threat detection across the cloud environment. The anomaly detection policies provide immediate detections, targeting numerous behavioral anomalies across users and the machines and devices connected to an organization’s network.
The security alerts generated by Impossible Travel provide detailed information on over 30 different risk indicators, including:
- Risky IP address
- Login failures
- Admin activity
- Inactive accounts
- Impossible travel
- Device and user agent
- Activity rate
This default rule in Office 365 has built-in intelligence through machine learning that also limits the number of false positives over time. For example, at Daymark most of our employees login from our office in Burlington, MA, but our Azure servers are located in Virginia. Office 365 has learned that this is not an anomaly that should trigger an alert, but rather normal behavior for our business.
Given the increased sophistication and frequency of cyberattacks, enterprises must be extremely vigilant. Identifying abnormal usage and gaining enhanced visibility into any and all potential threats is an important tool in the war on cybercrime.
Here are examples of a couple of alerts we’ve had at Daymark in the past (actual names and IP addresses have been partially obscured for privacy).
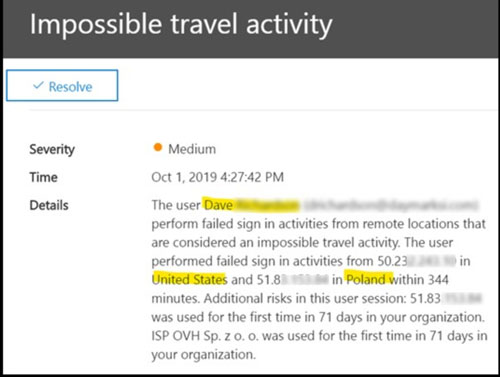
This alert tells us that one of our employees tried to login to our servers from both the U.S. and Poland within 344 minutes. That’s a little under 6 hours. Given that a non-stop flight from New York to Warsaw is 8 hours 20 minutes (without delays which almost never seems to happen these days!) this attempted login would be impossible.
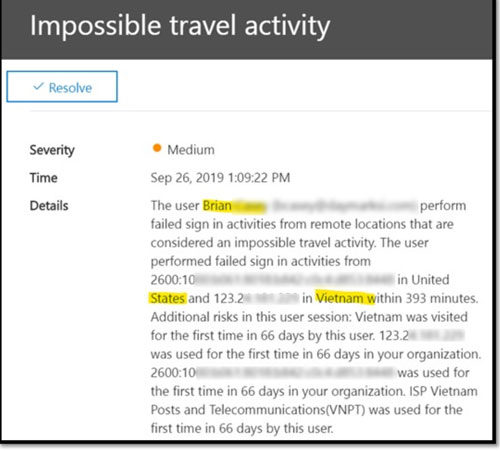
Being able to identify risky authentication attempts enables enterprises with Office 365 another level of protection against phishing and other social engineering attempts. If you want to learn more about a secure Office 365 deployment, contact us . Daymark is a Microsoft Tier 1 Cloud Service Provider with Gold Cloud Platform and Gold Cloud Productivity competencies. Both of these competencies are achieved through multiple business and technical certifications as well as positive customer feedback and solid execution, ensuring our consultants have the expertise to provide a smooth and secure Office 365 migration. In addition, we offer design, deployment and on-going management of Azure to help your team jumpstart the adoption of this cloud platform.
If you are interested in learning more about Microsoft Cloud App Security or need help implementing a comprehensive strategy Daymark can help. Click here to get started and checkout the fun gifts we have when you schedule a 20-minute meeting with us.
Subscribe to the Daymark Blog
Latest posts, browse by tag.
- Security (41)
- Microsoft (35)
- Partners (31)
- Data Protection (28)
- Data Center (26)
- Backup (24)
- Daymark News (23)
- Compliance (18)
- Data Governance (18)
- Veritas (18)
- Virtualization (18)
- Storage (17)
- Cloud Backup (13)
- Managed Services (13)
- Cybersecurity (12)
- Disaster Recovery (12)
- Government Cloud (9)
- Industry Expertise (9)
- Featured Gov (6)
- GCC High (6)
- Networking (6)
- Hybrid Cloud (5)
- NIST SP 800-171 (3)
- Reporting (3)
- Copilot for Microsoft 365 (2)
- Cloud Security (1)
- Reporting-as-a-Service (1)
How Can We Help? hbspt.cta._relativeUrls=true;hbspt.cta.load(30865, '5de282fd-640c-49b2-bf45-603dbee66842', {"useNewLoader":"true","region":"na1"});
Daymark Solutions is an experienced technology integration and solutions provider that helps organizations throughout North America effectively architect, implement, and deploy customized solutions to help their clients grow and scale their IT infrastructure. Specializing in data center infrastructure and cloud solutions, Daymark’s unique combination of in-depth technical knowledge, extensive experience, and proven methodologies enable its clients to successfully address even the most difficult technology challenges.
- Industry Expertise
Corporate Headquarters Daymark Solutions 131 Middlesex Turnpike Burlington, MA 01803
Corporate: +1 781-359-3000
Email: [email protected]

© 2024 Daymark Solutions, Inc. All rights reserved. | Day mark Privacy Policy
- Privacy Policy

Select Page
Step-by-Step guide to manage Impossible travel activity alert using Azure cloud app security
Posted by Dishan M. Francis | Sep 23, 2018 | Azure , Azure Active Directory | 2 |
Last Updated on September 26, 2018 by Dishan M. Francis
Let’s assume one of user in your sales team log in to https://myapps.microsoft.com and launch salesforce app successfully from his office in UK. Few minutes later the same user made successful login from Canada. Unless user is using remote connection, it is not impossible. Still someone can’t travel that fast ?. Azure Active Directory capable of detect this type of impossible sign-in activities. However, detection type for this kind of activities is “ offline ”. Which means reporting latency for these alerts are between 2 to 4 hours .
Azure cloud app security also capable of detecting these types of activities but it is real-time as it detects activities based on sessions. It helps administrators to react faster and protect infrastructure from potential breach. In this demo, I am going to demonstrate how to fine tune built in azure cloud app security policy for Impossible travel activity and prevent breach.
Before we start, first we need to integrate SaaS app with cloud app security. In my previous post I demonstrate how to do that. So please go ahead and read it on https://www.rebeladmin.com/2018/09/step-step-guide-block-data-download-using-azure-cloud-app-security/
In my demo I am using salesforce app.
1. Once integration is done, log in to https://portal.cloudappsecurity.com as global administrator.
2. Then go to Settings | Conditional access app control
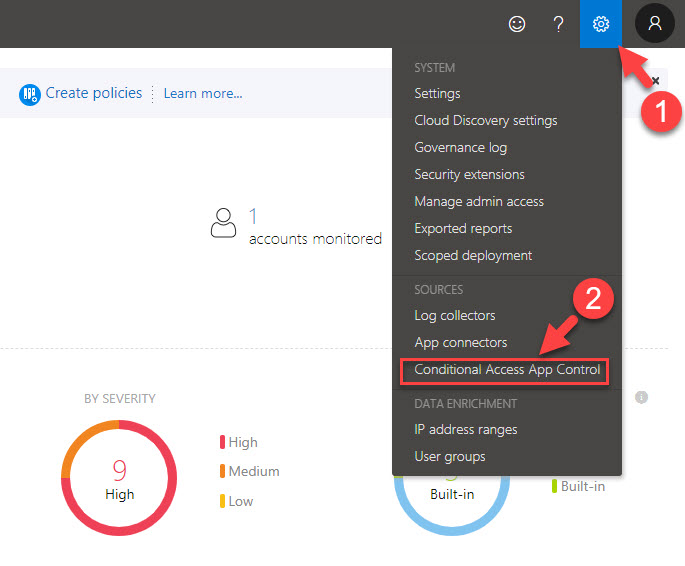
3. There you should be able to see your app under Conditional access app control tab. It should be in healthy connected status.
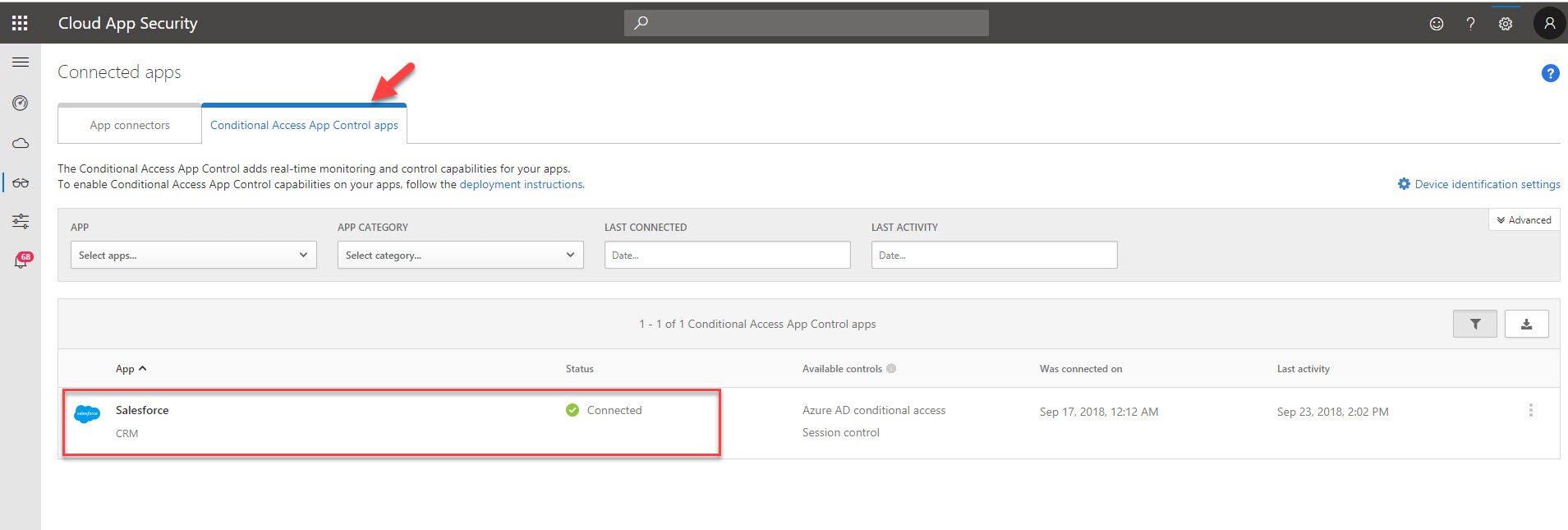
4. Then click on Control | Policies
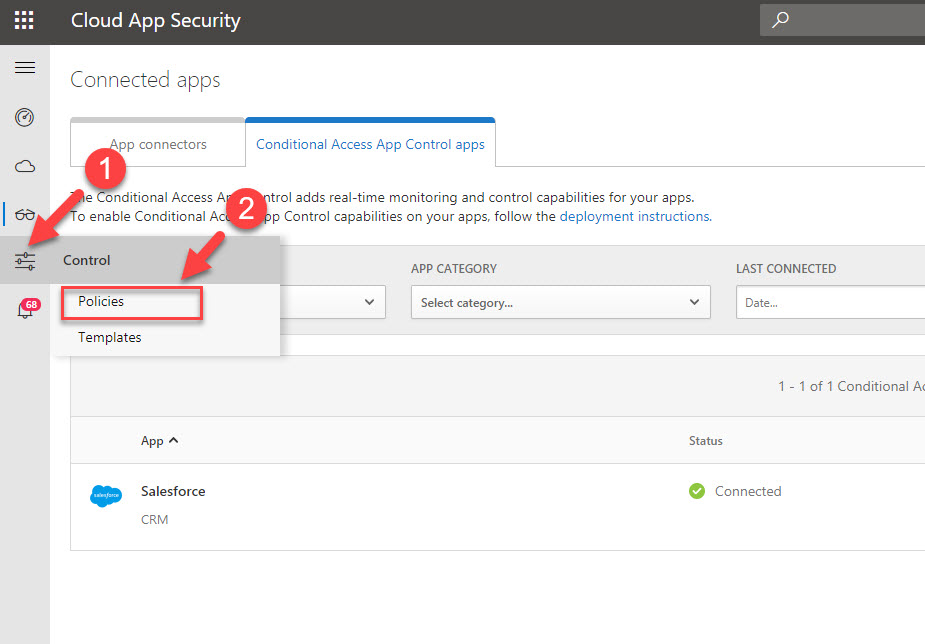
5. Under policies, click on impossible travel policy
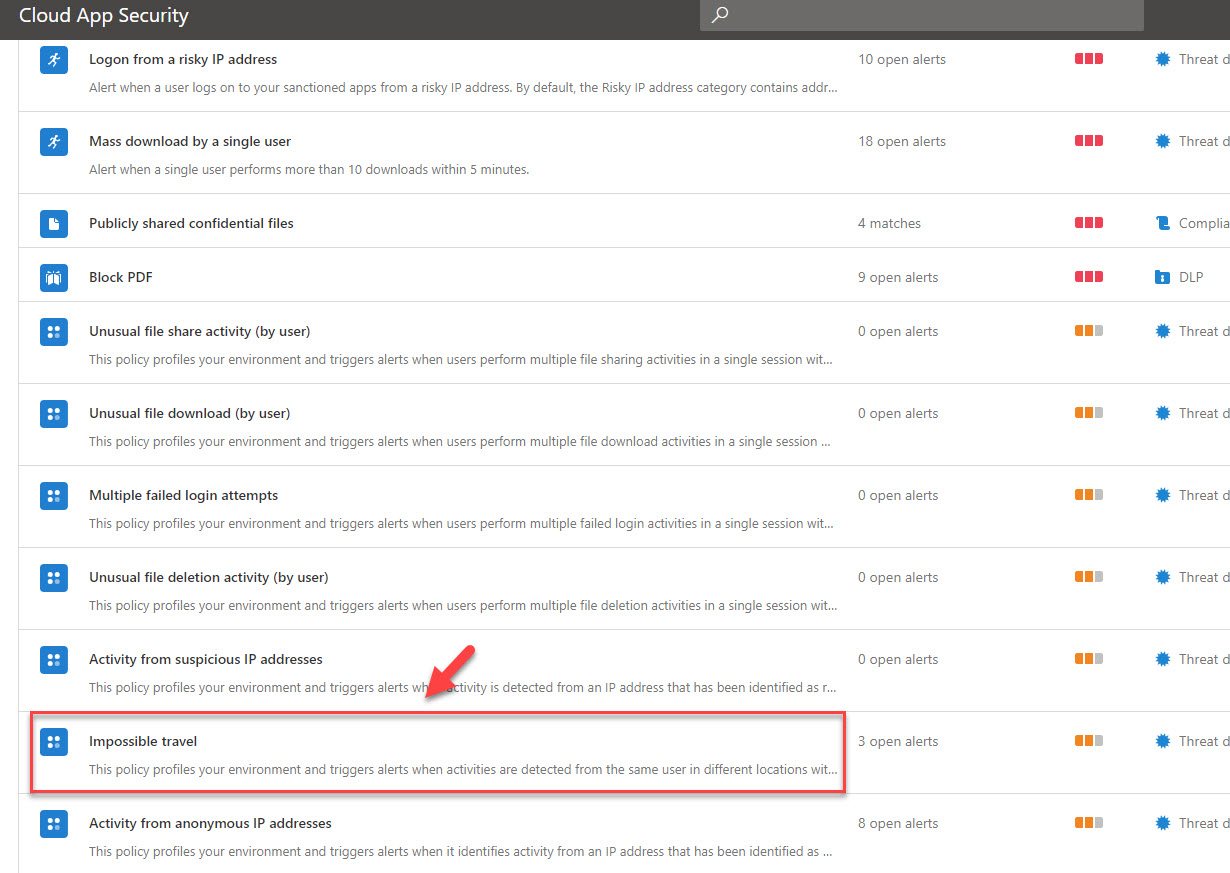
6. This is a built-in policy. as you can see it doesn’t have any actions attached to it. if CAS detect such activity, it will still be reported under CAS dashboards.
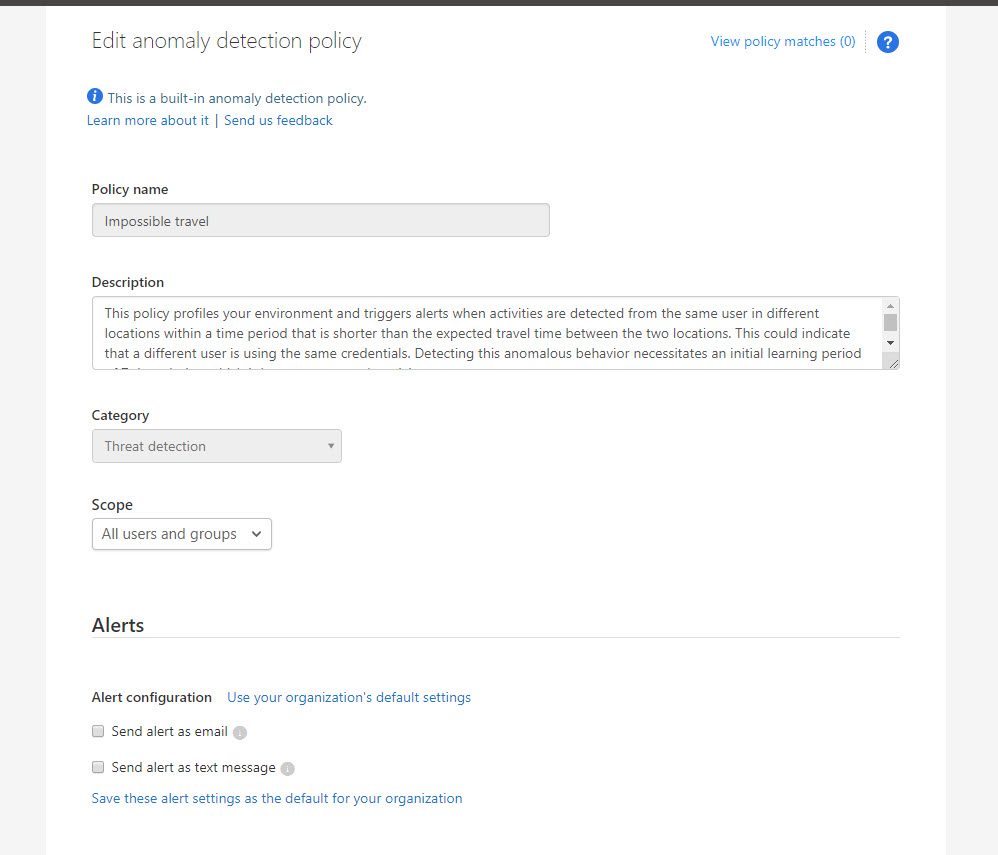
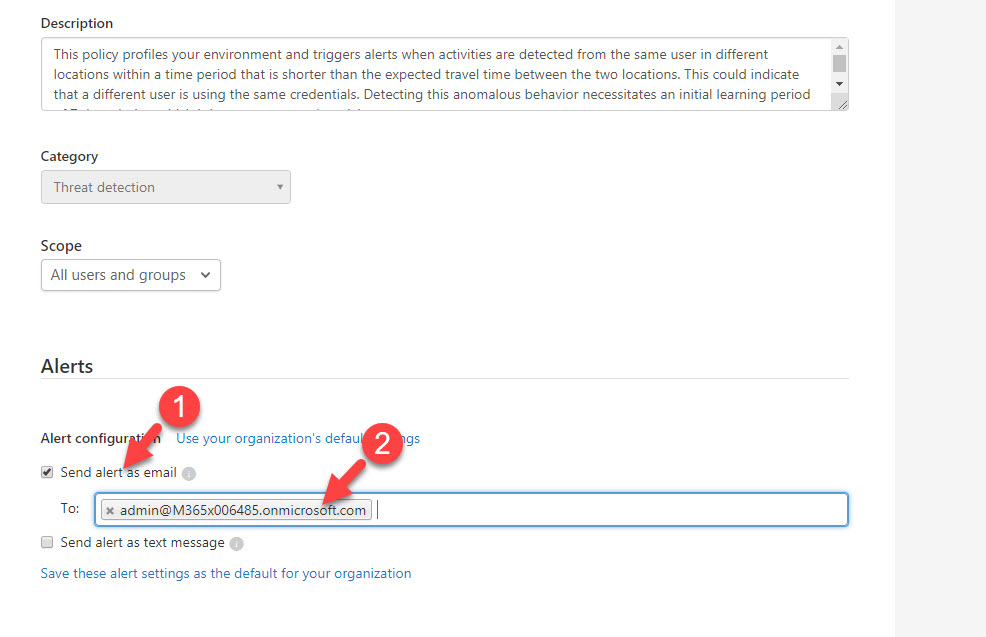
7. In my environment, I like to get an alert if its detect such activity. To do that, click on Send alert as email option under Alerts . Then define email address in text box.
8. I also like to suspend the user account, so it gives my team enough time to review the alert and do the necessary adjustments. To do that, click on All apps under Governance and click on Suspend user check box.
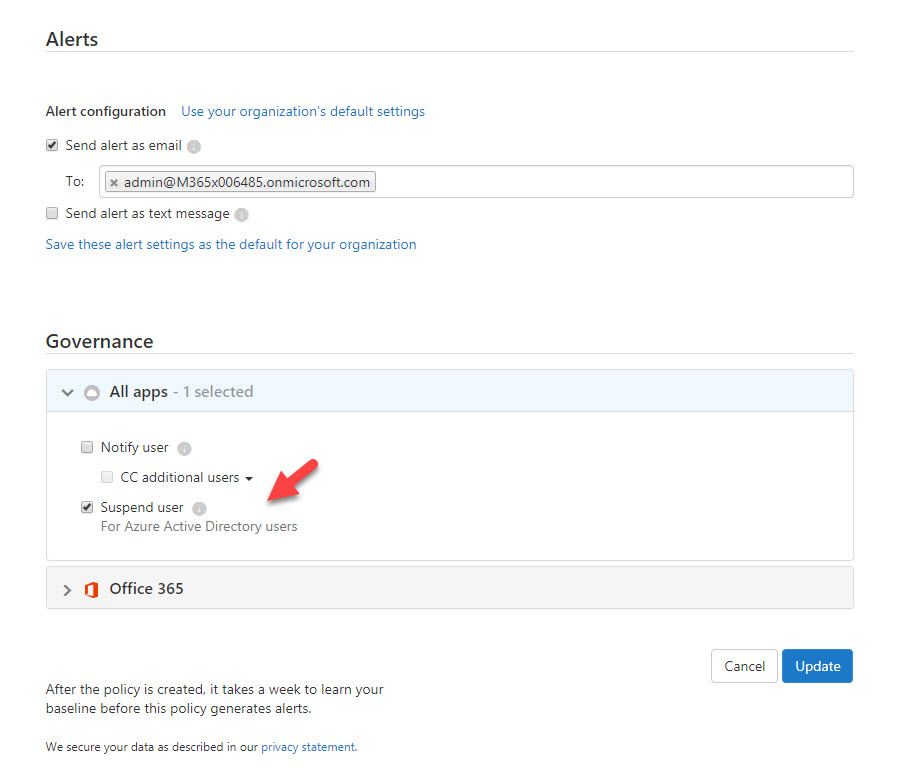
9. To complete the action, click on Update .
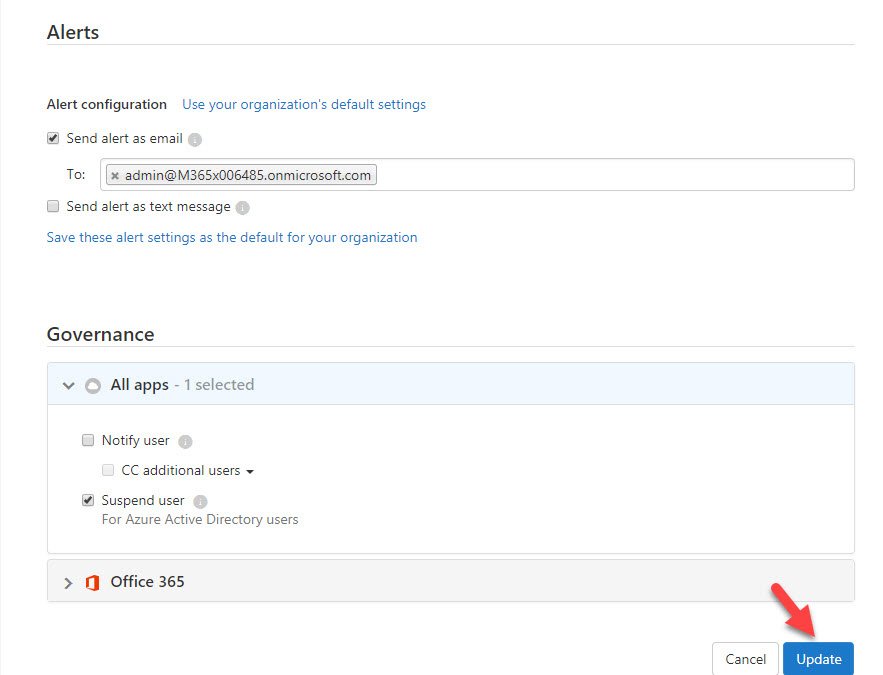
10. Policy is updated now. For testing I am login from two VMs located on two different locations.
11. Once the login is done, I came back to https://portal.cloudappsecurity.com . Then click on Salesforce app.
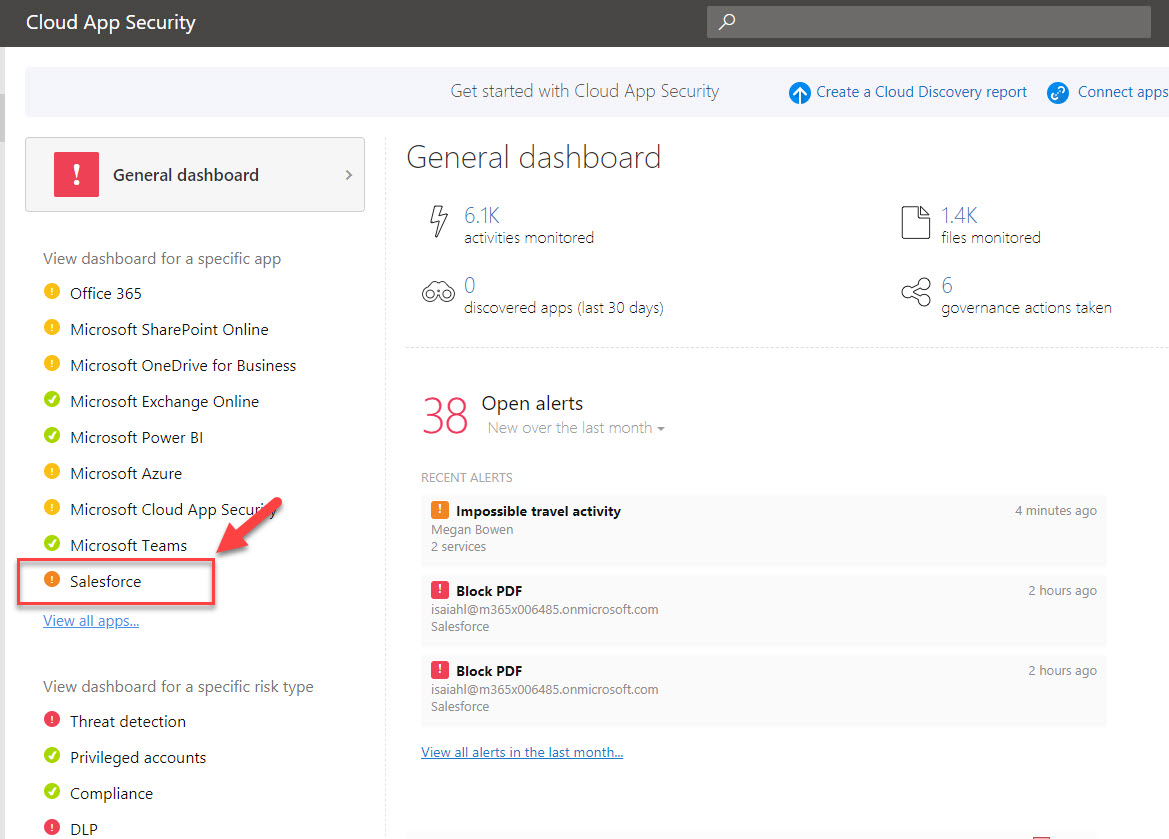
12. Under the alerts I can see it detected impossible travel activity. Click on it to view more details.
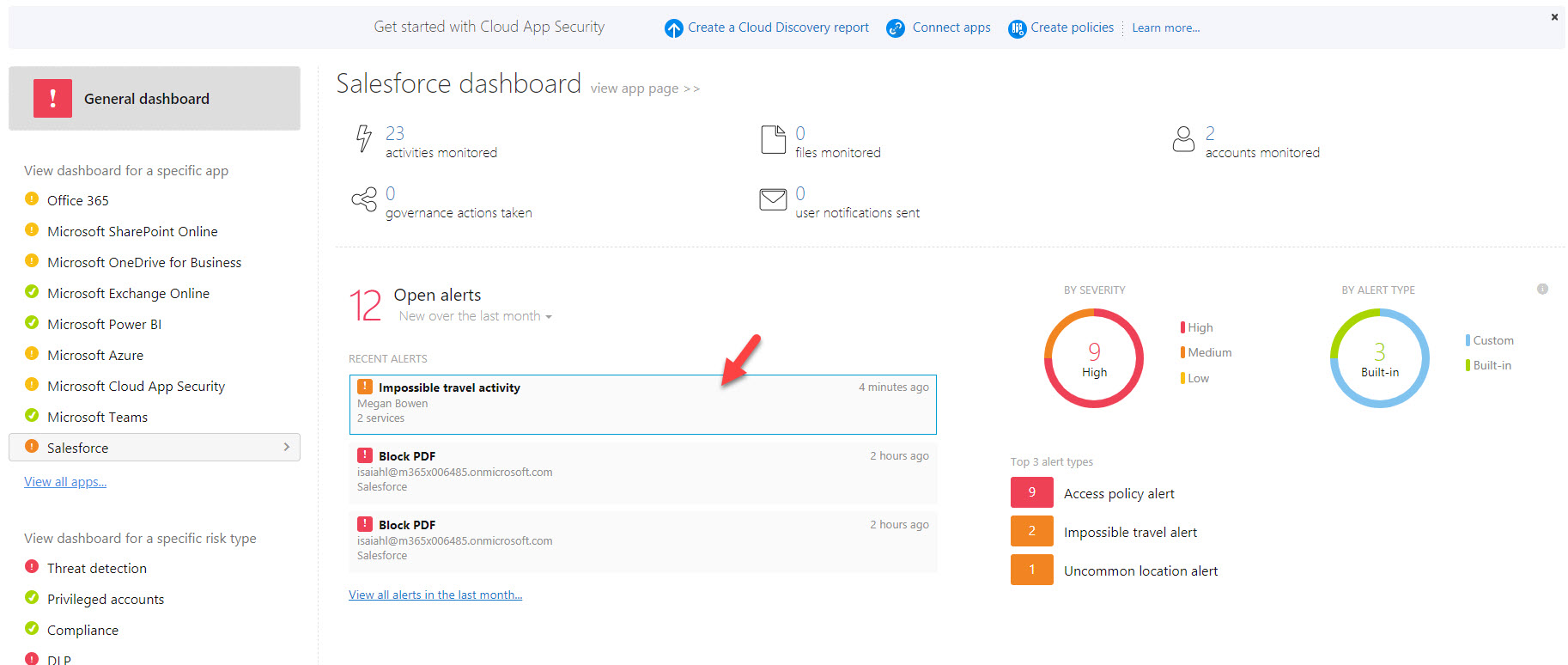
13. In there we can see in-details error description & activity log.
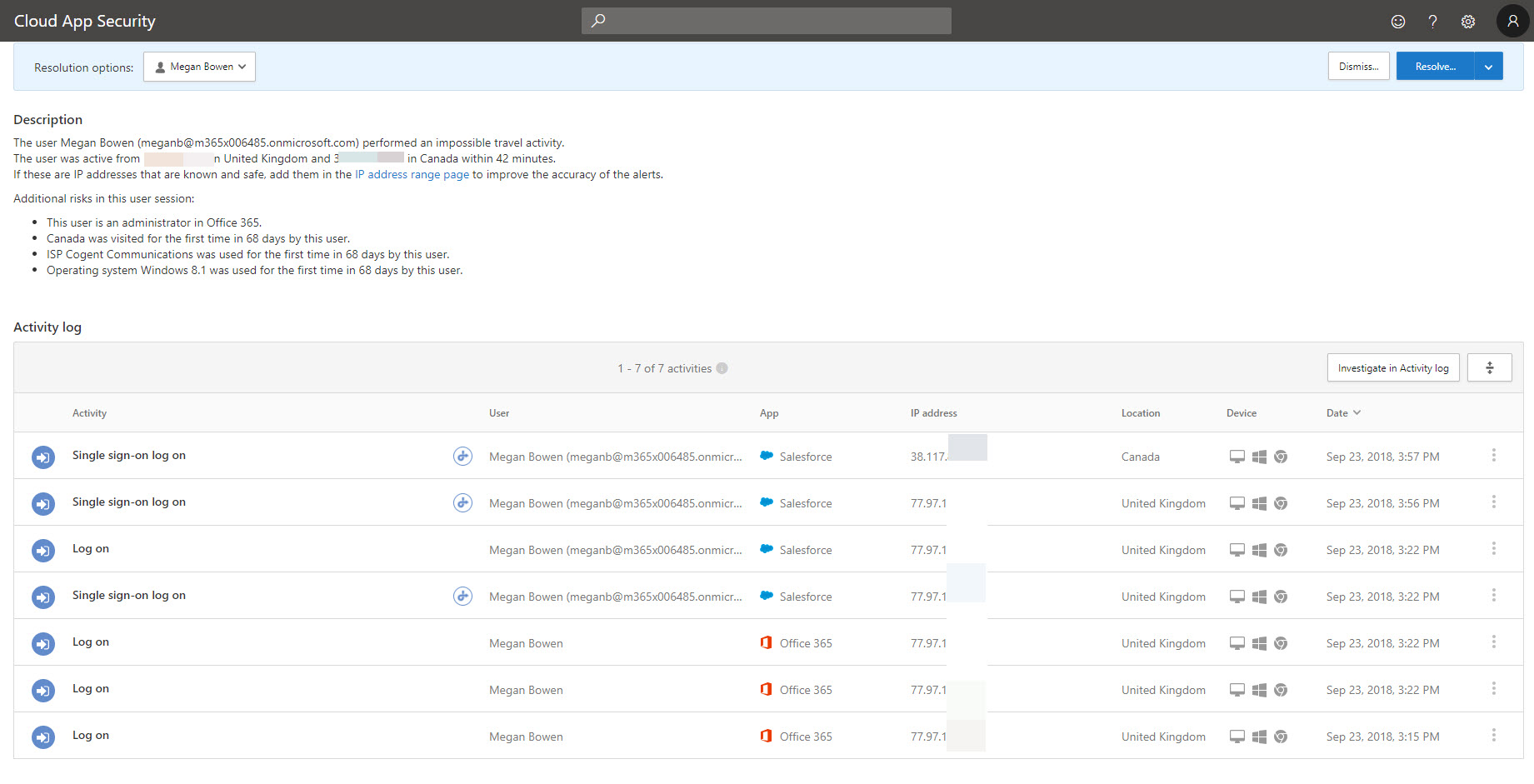
14. According to policy, I also should get email alert. When I log in to email I can see email alert for the activity as expected.

15. According to policy it also should suspend the user account. When I try to login again as the same user I got following account lock out error.
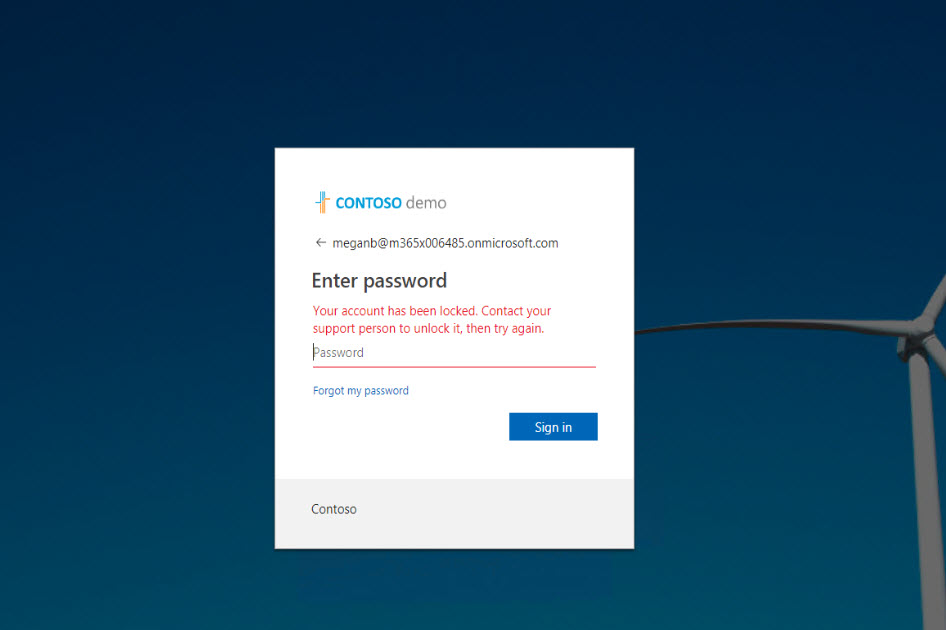
Cool ha? As expected policy detects the activities in real-time and take necessary actions as defined.
This marks the end of this blog post. If you have any further questions feel free to contact me on [email protected] also follow me on twitter @rebeladm to get updates about new blog posts.
Related Posts
Step-by-step guide: how to access azure vms securely using azure bastion.
November 7, 2019
Azure AD Connect Common Issues
July 27, 2019
Step-by-Step guide to configure your own app with Azure AD Password-based single-sign on
September 11, 2018
Step-by-Step Guide to Windows Virtual Desktop (Spring 2020 Release)
July 21, 2020
I am currently using the impossible travel alert for Office 365 logins. However, the alert goes off even if the login from an impossible travel location was unsuccessful.
This has made this alert useless because these unsuccessful logins are happening all the time as bots and bad actors are constantly trying to log in to my users accounts.
Is there a way to set the alert to only kick off if the login was successful?
This is also detecting account login via VPN in different location. How can we exclude that ? also, failed logins are also coming as alert. can we exclude them to reduce number of false positive.
Trackbacks/Pingbacks
- travel cloud login - Login Portal - […] 8. Step-by-Step guide to manage Impossible travel activity … […]
Leave a reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

I am Dishan Francis. I’m a Cyber Security Consultant at Microsoft. I’m a dedicated and enthusiastic information technology expert who enjoys professional recognition and accreditation from several respected institutions. I am maintaining this blog for last 11 years. This includes more than 400 articles already. These are mainly about Microsoft Active Directory Service and Azure Active Directory Service. I also blog about different Azure services. If you need further help on subject matters, feel free to contact me on [email protected]. Also to get latest updates, follow me on twitter @rebeladm
Mastering Active Directory, Third Edition

I am glad to announce the release of my new book “ Mastering Active Directory – 3rd Edition ”. It is available for purchase worldwide now For more info….

American Airlines and Microsoft partnership takes flight to create a smoother travel experience for customers and better technology tools for team members
- Share on Facebook (opens new window)
- Share on LinkedIn (opens new window)
- Share on Twitter (opens new window)

As summer travel season approaches, companies streamline operations and reimagine team member and traveler experiences with the Microsoft Cloud
FORT WORTH, Texas, and REDMOND, Wash. — May 18, 2022 — American Airlines and Microsoft Corp. are partnering to use technology to create better, more connected experiences for customers and American Airlines team members, supporting the robust operations of the world’s largest airline. As part of the partnership, American will use Microsoft Azure as its preferred cloud platform for its airline applications and key workloads, significantly accelerating its digital transformation and making Microsoft one of the airline’s largest technology partners.
With travel and tourism this year expected to surpass pre-pandemic levels , the companies are preparing for a future where consumers expect their travel experience to mimic the rest of their lives — more connected, more personalized and more on demand than ever.

“Reliably operating thousands of flights around the world to take customers to hundreds of destinations is critical to American, which is why the airline has chosen Microsoft’s technology to support our applications,” said American Airlines Chief Information Officer Maya Leibman. “With the power of Microsoft Azure, American can innovate and accelerate its technology transformation, giving our team members augmented tools to provide our customers with an enhanced travel experience.”
“As the airline industry continues to transform, building a digital technology foundation in the cloud will be essential for future resilience,” said Judson Althoff, EVP and chief commercial officer, Microsoft. “Through our partnership, American Airlines is taking a forward-thinking, cloud-first approach to using data, AI and our collaboration platforms to reimagine not only its own operations but the experiences of its employees and customers.”
Already, American and Microsoft are progressing toward innovative and transformational experiences for airline employees and customers.
Using data to streamline operations and reduce travel pain points
When an aircraft lands at American’s largest hub, Dallas Fort Worth International Airport (DFW), reaching the gate quickly is critical to running a smooth operation. American and Microsoft are applying the power of AI, machine learning and data analytics to reduce taxi time, saving thousands of gallons of jet fuel per year and giving connecting customers extra time to make their next flights. Built on Azure, American’s intelligent gating program provides real-time analysis of data points, including routing and runway information, to automatically assign the nearest available gate to arriving aircraft. Previously, gating decisions for American’s 136 gates at DFW required more manual involvement from gate planners. Now, the program can look at multiple data points simultaneously for the hundreds of daily arrivals, saving more than a minute of taxi time per flight. That adds up to 10 hours of reduced taxi time per day, lower fuel usage and decreased CO 2 emissions.
Enhancing frontline collaboration to drive better customer experiences
For a flight to leave on time takes many team members behind the scenes. Every day, maintenance personnel, ground crew, pilots, flight attendants and gate agents work together to ensure that each flight departs on time. Until recently, these team members — who are always on the move and rarely tied to a desk — relied on accessing information via desktop computers or laptops. American and Microsoft created the ConnectMe app, which team members can access from any mobile device via a Microsoft Power Apps-enabled app in Microsoft Teams. With information now at its fingertips, American has accelerated airplane turn times at gates and connected thousands of frontline team members through a single platform.
Creating a cloud platform for the future of airline operations
Running the world’s largest airline is no small feat. Now, through American’s partnership with Microsoft, the airline will migrate and centralize strategic operational workloads — such as its data warehouse and several legacy applications — in one Operations Hub on Azure, becoming one of the first global airlines to embrace a comprehensive cloud strategy for all its business areas. With its Operations Hub on Azure, American plans to save costs, increase efficiency and scalability, and progress toward its ambitious sustainability goals.
In addition to their cloud partnership, the companies are deepening their relationship to support Microsoft employee travel. Through the highly preferred partnership with American, Microsoft employees will receive new, enhanced benefits when they choose American or its alliance partners for their business travel. Furthermore, American and Microsoft may use Microsoft employee feedback to inform future innovations to continue driving a more connected, seamless and personalized travel experience.
About American Airlines Group
To Care for People on Life’s Journey ® . Shares of American Airlines Group Inc. trade on Nasdaq under the ticker symbol AAL, and the company’s stock is included in the S&P 500. Learn more about what’s happening at American by visiting news.aa.com and connect with American on Twitter @AmericanAir and at Facebook.com/AmericanAirlines .
About Microsoft
Microsoft (Nasdaq “MSFT” @microsoft) enables digital transformation for the era of an intelligent cloud and an intelligent edge. Its mission is to empower every person and every organization on the planet to achieve more.
For more information, press only:
Microsoft Media Relations, WE Communications for Microsoft, (425) 638-7777, [email protected]
Andrea Koos, American Airlines, (817) 247-4748, [email protected]
Note to editors: For more information, news and perspectives from Microsoft, please visit the Microsoft News Center at http://news.microsoft.com . Web links, telephone numbers and titles were correct at time of publication but may have changed. For additional assistance, journalists and analysts may contact Microsoft’s Rapid Response Team or other appropriate contacts listed at https://news.microsoft.com/microsoft-public-relations-contacts .
Related Posts
Axel Springer and Microsoft expand partnership across advertising, AI, content and Azure services
The Estée Lauder Companies and Microsoft increase collaboration to power prestige beauty with generative AI
Microsoft earnings press release available on Investor Relations website
Microsoft Cloud strength fuels third quarter results
The Coca-Cola Company and Microsoft announce five-year strategic partnership to accelerate cloud and generative AI initiatives
- Check us out on RSS
Share this page:

This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
What are risk detections?
- 19 contributors
Microsoft Entra ID Protection provides organizations with information to suspicious activity in their tenant and allows them to respond quickly to prevent further risk occurring. Risk detections are a powerful resource that can include any suspicious or anomalous activity related to a user account in the directory. ID Protection risk detections can be linked to an individual user or sign-in event and contribute to the overall user risk score found in the Risky Users report .
User risk detections might flag a legitimate user account as at risk, when a potential threat actor gains access to an account by compromising their credentials or when they detect some type of anomalous user activity. Sign-in risk detections represent the probability that a given authentication request isn't the authorized owner of the account. Having the ability to identify risk at the user and sign-in level is critical for customers to be empowered to secure their tenant.
Risk levels
ID Protection categorizes risk into three tiers: low, medium, and high. Risk levels calculated by our machine learning algorithms and represent how confident Microsoft is that one or more of the user's credentials are known by an unauthorized entity.
- A risk detection with risk level High signifies that Microsoft is highly confident that the account is compromised.
- A risk detection with risk level Low signifies that there are anomalies present in the sign-in or a user’s credential, but we're less confident that these anomalies mean the account is compromised.
Many detections can fire at more than one of our risk levels depending on the number or severity of the anomalies detected. For example, Unfamiliar sign-in properties might fire at high, medium, or low based on the confidence in the signals. Some detections, like Leaked Credentials and Verified Threat Actor IP are always delivered as high risk.
This risk level is important when deciding which detections to prioritize, investigate, and remediate. They also play a key role in configuring risk based Conditional Access policies as each policy can be set to trigger for low, medium, high, or no risk detected. Based on the risk tolerance of your organization, you can create policies that require MFA or password reset when ID Protection detects a certain risk level for one of your users. These policies can guide the user to self-remediate to resolve the risk.
All "low" risk level detections and users will persist in the product for 6 months, after which they will be automatically aged out to provide a cleaner investigation experience. Medium and high risk levels will persist until remediated or dismissed.
Based on the risk tolerance of your organization, you can create policies that require MFA or password reset when ID Protection detects a certain risk level. These policies might guide the user to self-remediate and resolve the risk or block depending on your tolerances.
Real-time and offline detections
ID Protection utilizes techniques to increase the precision of user and sign-in risk detections by calculating some risks in real-time or offline after authentication. Detecting risk in real-time at sign-in gives the advantage of identifying risk early so that customers can quickly investigate the potential compromise. On detections that calculate risk offline, they can provide more insight as to how the threat actor gained access to the account and the impact on the legitimate user. Some detections can be triggered both offline and during sign-in, which increases confidence in being precise on the compromise.
Detections triggered in real-time take 5-10 minutes to surface details in the reports. Offline detections take up to 48 hours to surface in the reports, as it takes time to evaluate properties of the potential risk.
Our system might detect that the risk event that contributed to the risk user risk score was either:
- A false positive
- Completing multifactor authentication
- Secure password change
Our system will dismiss the risk state and a risk detail of AI confirmed sign-in safe will show and no longer contribute to the user’s overall risk.
Risk detections mapped to riskEventType
Premium detections.
The following premium detections are visible only to Microsoft Entra ID P2 customers.
Premium sign-in risk detections
Activity from anonymous ip address.
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps . This detection identifies that users were active from an IP address identified as an anonymous proxy IP address.
Anomalous token
Calculated in real-time or offline. This detection indicates abnormal characteristics in the token, such as an unusual lifetime or a token played from an unfamiliar location. This detection covers Session Tokens and Refresh Tokens.
Anomalous token is tuned to incur more noise than other detections at the same risk level. This tradeoff is chosen to increase the likelihood of detecting replayed tokens that might otherwise go unnoticed. There's a higher than normal chance that some of the sessions flagged by this detection are false positives. We recommend investigating the sessions flagged by this detection in the context of other sign-ins from the user. If the location, application, IP address, User Agent, or other characteristics are unexpected for the user, the administrator should consider this risk as an indicator of potential token replay.
Atypical travel
Calculated offline. This risk detection type identifies two sign-ins originating from geographically distant locations, where at least one of the locations might also be atypical for the user, given past behavior. The algorithm takes into account multiple factors including the time between the two sign-ins and the time it would take for the user to travel from the first location to the second. This risk might indicate that a different user is using the same credentials.
The algorithm ignores obvious "false positives" contributing to the impossible travel conditions, such as VPNs and locations regularly used by other users in the organization. The system has an initial learning period of the earliest of 14 days or 10 logins, during which it learns a new user's sign-in behavior.
Impossible travel
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps . This detection identifies user activities (in a single or multiple sessions) originating from geographically distant locations within a time period shorter than the time it takes to travel from the first location to the second. This risk might indicate that a different user is using the same credentials.
Malicious IP address
Calculated offline. This detection indicates sign-in from a malicious IP address. An IP address is considered malicious based on high failure rates because of invalid credentials received from the IP address or other IP reputation sources.
Mass access to sensitive files
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps . This detection looks at your environment and triggers alerts when users access multiple files from Microsoft SharePoint Online or Microsoft OneDrive. An alert is triggered only if the number of accessed files is uncommon for the user and the files might contain sensitive information.
New country
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps . This detection considers past activity locations to determine new and infrequent locations. The anomaly detection engine stores information about previous locations used by users in the organization.
Password spray
Calculated offline. A password spray attack is where multiple usernames are attacked using common passwords in a unified brute force manner to gain unauthorized access. This risk detection is triggered when a password spray attack is performed. For example, the attacker is successfully authenticated, in the detected instance.
Suspicious browser
Calculated offline. Suspicious browser detection indicates anomalous behavior based on suspicious sign-in activity across multiple tenants from different countries in the same browser.
Suspicious inbox forwarding
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps . This detection looks for suspicious email forwarding rules, for example, if a user created an inbox rule that forwards a copy of all emails to an external address.
Suspicious inbox manipulation rules
Calculated offline. This detection is discovered using information provided by Microsoft Defender for Cloud Apps . This detection looks at your environment and triggers alerts when suspicious rules that delete or move messages or folders are set on a user's inbox. This detection might indicate: a user's account is compromised, messages are being intentionally hidden, and the mailbox is being used to distribute spam or malware in your organization.
Token issuer anomaly
Calculated offline. This risk detection indicates the SAML token issuer for the associated SAML token is potentially compromised. The claims included in the token are unusual or match known attacker patterns.
Unfamiliar sign-in properties
Calculated in real-time. This risk detection type considers past sign-in history to look for anomalous sign-ins. The system stores information about previous sign-ins, and triggers a risk detection when a sign-in occurs with properties that are unfamiliar to the user. These properties can include IP, ASN, location, device, browser, and tenant IP subnet. Newly created users are in a "learning mode" period where the unfamiliar sign-in properties risk detection is turned off while our algorithms learn the user's behavior. The learning mode duration is dynamic and depends on how much time it takes the algorithm to gather enough information about the user's sign-in patterns. The minimum duration is five days. A user can go back into learning mode after a long period of inactivity.
We also run this detection for basic authentication (or legacy protocols). Because these protocols don't have modern properties such as client ID, there's limited data to reduce false positives. We recommend our customers to move to modern authentication.
Unfamiliar sign-in properties can be detected on both interactive and non-interactive sign-ins. When this detection is detected on non-interactive sign-ins, it deserves increased scrutiny due to the risk of token replay attacks.
Selecting an unfamiliar sign-in properties risk allows you to see additional info showing more detail about why this risk triggered.
Verified threat actor IP
Calculated in real-time. This risk detection type indicates sign-in activity that is consistent with known IP addresses associated with nation state actors or cyber crime groups, based on data from the Microsoft Threat Intelligence Center (MSTIC).
Premium user risk detections
Anomalous user activity.
Calculated offline. This risk detection baselines normal administrative user behavior in Microsoft Entra ID, and spots anomalous patterns of behavior like suspicious changes to the directory. The detection is triggered against the administrator making the change or the object that was changed.
Attacker in the Middle
Calculated offline. Also known as Adversary in the Middle, this high precision detection is triggered when an authentication session is linked to a malicious reverse proxy. In this kind of attack, the adversary can intercept the user's credentials, including tokens issued to the user. The Microsoft Security Research team leverages Microsoft 365 Defender to capture the identified risk and raises the user to High risk. We recommend administrators manually investigate the user when this detection is triggered to ensure the risk is cleared. Clearing this risk might require secure password reset or revocation of existing sessions.
Possible attempt to access Primary Refresh Token (PRT)
Calculated offline. This risk detection type is discovered using information provided by Microsoft Defender for Endpoint (MDE). A Primary Refresh Token (PRT) is a key artifact of Microsoft Entra authentication on Windows 10, Windows Server 2016, and later versions, iOS, and Android devices. A PRT is a JSON Web Token (JWT) issued to Microsoft first-party token brokers to enable single sign-on (SSO) across the applications used on those devices. Attackers can attempt to access this resource to move laterally into an organization or perform credential theft. This detection moves users to high risk and only fires in organizations that deploy MDE. This detection is high risk and we recommend prompt remediation of these users. It appears infrequently in most organizations due to its low volume.
Suspicious API traffic
Calculated offline. This risk detection is reported when abnormal GraphAPI traffic or directory enumeration is observed. Suspicious API traffic might suggest that a user is compromised and conducting reconnaissance in the environment.
Suspicious sending patterns
Calculated offline. This risk detection type is discovered using information provided by Microsoft Defender for Office 365 (MDO) . This alert is generated when someone in your organization sent suspicious email and is either at risk of being or is restricted from sending email. This detection moves users to medium risk and only fires in organizations that deploy MDO. This detection is low-volume and is seen infrequently in most organizations.
User reported suspicious activity
Calculated offline. This risk detection is reported when a user denies a multifactor authentication (MFA) prompt and reports it as suspicious activity. An MFA prompt not initiated by a user might mean their credentials are compromised.
Nonpremium detections
Customers without Microsoft Entra ID P2 licenses receive detections titled Additional risk detected without the detailed information regarding the detection that customers with P2 licenses do. For more information, see the license requirements .
Nonpremium sign-in risk detections
Additional risk detected (sign-in).
Calculated in real-time or offline. This detection indicates that one of the premium detections was detected. Since the premium detections are visible only to Microsoft Entra ID P2 customers, they're titled Additional risk detected for customers without Microsoft Entra ID P2 licenses.
Admin confirmed user compromised
Calculated offline. This detection indicates an administrator selected Confirm user compromised in the risky users UI or using riskyUsers API. To see which administrator confirmed this user compromised, check the user's risk history (via UI or API).
Anonymous IP address
Calculated in real-time. This risk detection type indicates sign-ins from an anonymous IP address (for example, Tor browser or anonymous VPN). These IP addresses are typically used by actors who want to hide their sign-in information (IP address, location, device, and so on) for potentially malicious intent.
Microsoft Entra threat intelligence (sign-in)
Calculated in real-time or offline. This risk detection type indicates user activity that is unusual for the user or consistent with known attack patterns. This detection is based on Microsoft's internal and external threat intelligence sources.

Nonpremium user risk detections
Additional risk detected (user), leaked credentials.
Calculated offline. This risk detection type indicates that the user's valid credentials leaked. When cybercriminals compromise valid passwords of legitimate users, they often share these gathered credentials. This sharing is typically done by posting publicly on the dark web, paste sites, or by trading and selling the credentials on the black market. When the Microsoft leaked credentials service acquires user credentials from the dark web, paste sites, or other sources, they're checked against Microsoft Entra users' current valid credentials to find valid matches. For more information about leaked credentials, see common questions .
Microsoft Entra threat intelligence (user)
Calculated offline. This risk detection type indicates user activity that is unusual for the user or consistent with known attack patterns. This detection is based on Microsoft's internal and external threat intelligence sources.
Common questions
What if incorrect credentials were used to attempt to sign-in.
ID Protection generates risk detections only when the correct credentials are used. If incorrect credentials are used on a sign-in, it doesn't represent risk of credential compromise.
Is password hash synchronization required?
Risk detections like leaked credentials require the presence of password hashes for detection to occur. For more information about password hash synchronization, see the article, Implement password hash synchronization with Microsoft Entra Connect Sync .
Why are risk detections generated for disabled accounts?
User accounts in a disabled state can be re-enabled. If the credentials of a disabled account are compromised, and the account gets re-enabled, bad actors might use those credentials to gain access. ID Protection generates risk detections for suspicious activities against these disabled accounts to alert customers about potential account compromise. If an account is no longer in use and wont be re-enabled, customers should consider deleting it to prevent compromise. No risk detections are generated for deleted accounts.
Common leaked credentials questions
Where does microsoft find leaked credentials.
Microsoft finds leaked credentials in various places, including:
- Public paste sites where bad actors typically post such material.
- Law enforcement agencies.
- Other groups at Microsoft doing dark web research.
Why am I not seeing any leaked credentials?
Leaked credentials are processed anytime Microsoft finds a new, publicly available batch. Because of the sensitive nature, the leaked credentials are deleted shortly after processing. Only new leaked credentials found after you enable password hash synchronization (PHS) are processed against your tenant. Verifying against previously found credential pairs isn't done.
I don't see any leaked credential risk events
If you don't see any leaked credential risk events, it is because of the following reasons:
- You don't have PHS enabled for your tenant.
- Microsoft didn't find any leaked credential pairs that match your users.
How often does Microsoft process new credentials?
Credentials are processed immediately after they're found, normally in multiple batches per day.
Location in risk detections is determined using IP address lookup. Sign-ins from trusted named locations improve the accuracy of Microsoft Entra ID Protection's risk calculation, lowering a user's sign-in risk when they authenticate from a location marked as trusted.
Related content
- Learn about risk-based access policies
- Learn how to investigate risk
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

How to set up Microsoft Azure AD Identity Protection to spot risky users
Whichever license of azure active directory you own, you have options to set up alerts and automate actions to risky user behavior..

Do your users perform actions that put your organization at risk? If you have an Azure Active Directory (AD) Premium 2 (P2) license, you can set up risk alert rules that tell you when their actions are putting your firm at risk. You can also instruct it to take additional actions based on the activities seen by Azure AD Identity Protection at the sign-in process.
If you have a Premium 1 (P1) license, you will receive a “Sign-in with additional risk detected” notice. The risk level and risk detail fields are hidden, but this might be enough to alert you to actions that put your firm at risk. There are different features included in Azure AD P1 versus Azure AD P2 , and how each reports on risky user activities is just one of them.
Azure monitors how a user logs in and takes action if it sees unusual activity based on policies you set up. This setting is similar to the Microsoft 365 user login monitoring but focuses on the user login for Azure AD. You can purchase a single P2 license to add this level of protection for your global administrator accounts and leave the rest of your users with a P1 license or even at the basic Azure AD level. You may find conflicting information on the web, but you can mix and match Azure licenses to put together the best protection for your accounts. This is just one of many best practices that you can do for Azure AD as noted on this best practices checklist .
The risk event types Azure AD detects include:
- Users with leaked credentials: This is done by comparing the credentials, monitoring public and dark web websites, and working with researchers, law enforcement, and security teams at Microsoft and other trusted sources.
- Sign-ins from anonymous IP addresses: The service checks sign-ins in real time from an anonymous IP address (for example, Tor browser , anonymizer VPNs). These IP addresses are typically used by attackers who want to hide their login telemetry (IP address, location, device, etc.) for potentially malicious intent.
- Impossible travel to atypical locations: This is done with a service that identifies two sign-ins originating from geographically distant locations, where at least one of the locations may also be atypical for the user, given past behavior. The service actually calculates the time it takes to travel between the two locations and how it would be impossible to be in those two locations. The service ignores obvious “false positives” contributing to the impossible travel conditions, such as VPNs and locations regularly used by other users in the organization. It takes two weeks for the system to learn the user’s behavior.
- Sign-ins from unfamiliar locations and from IP addresses with suspicious activity: This is done in real time and is best when used with modern authentication and where basic authentication is disabled.
- Sign-ins from infected devices: These are monitored and blocked.
Setting up Azure AD Identity Protection
To get started with Azure AD Identity Protection, you’ll need to add Azure AD Identity Protection through the Azure Marketplace under Security + Identity.
Look in the Azure AD Identity marketplace
Then log into the dashboard and review if you have users already at risk. In my sample account, it’s already flagged my user account as not having multi-factor authentication (MFA).
Azure AD Identity Protection page
Go to the Azure AD Identity Protection page and set up the sign-in risk policy. To set up the policy, click on “Azure AD Identity Protection – Sign-in risk policy”. Set the policy to either all users or selected users. Choose sign-in risk as high and click “Done”. Now it’s time to assign a control. Choose “Select a control” such as blocking the user or demanding that the user change their password. Save the policy.
You might think that choosing low risk will give you the best experience when setting up a new policy. However, it’s exactly opposite. The “high” value refers to how likely the event indicates a compromised identity and not the high risk of activities. It’s about high confidence that a high severity risk event indicates that any user accounts impacted should be remediated immediately.
If you choose low risk, it means more chance of a false positive. That is a low confidence and low severity risk event. This event may not require an immediate action, but when combined with other risk events, might provide a strong indication that the identity is compromised.
Azure AD risk reporting levels vary
Depending on the license of Azure AD you have, you may have different reporting levels. For example, if you have the Azure AD Free and Basic editions, you get a list of users flagged for risk. If you have Azure AD P1 edition you can dig deeper into the underlying risk events that have been flagged in the risk report. Finally if you have the Azure AD P2 version, you get the most detailed level of information. You can even set up security policies that respond to the triggered risks events flagged. You can mix and match different licenses and assign a P2 license just for your more risky users such as global admins.
Microsoft is in the process of expanding the risky user report with a more expanded version at the updated risky user report . While you review the risk report, take the time to review the identity secure score report.
Don’t forget to sign up for the IDG Tech Talk channel where you can see more videos of my Windows security tips.
Related content
Kinsing crypto mining campaign targets 75 cloud-native applications, how to future-proof windows networks: take action now on planned phaseouts and changes, hunters announces full adoption of ocsf and introduces ocsf-native search, administrator of ransomware operation lockbit named, charged, has assets frozen, from our editors straight to your inbox.

Susan Bradley has been patching since before the Code Red/Nimda days and remembers exactly where she was when SQL slammer hit (trying to buy something on eBay and wondering why the Internet was so slow). She writes the Patch Watch column for Askwoody.com, is a moderator on the PatchManagement.org listserve, and writes a column of Windows security tips for CSOonline.com. In real life, she’s the IT wrangler at her firm, Tamiyasu, Smith, Horn and Braun, where she manages a fleet of Windows servers, Microsoft 365 deployments, Azure instances, desktops, a few Macs, several iPads, a few Surface devices, several iPhones and tries to keep patches up to date on all of them. In addition, she provides forensic computer investigations for the litigation consulting arm of the firm. She blogs at https://www.askwoody.com/tag/patch-lady-posts/ and is on twitter at @sbsdiva. She lurks on Twitter and Facebook, so if you are on Facebook with her, she really did read what you posted. She has a SANS/GSEC certification in security and prefers Heavy Duty Reynolds wrap for her tinfoil hat.
More from this author
3 windows vulnerabilities that may not be worth patching, looking outside: how to protect against non-windows network vulnerabilities, us federal agencies get first crack at expanded microsoft 365 logging capabilities, most popular authors.

Show me more
Us doing all it can to manage global cybersecurity threats, secretary of state tells rsac.

Change Healthcare went without cyber insurance before debilitating ransomware attack

Citrix quietly fixes a new critical vulnerability similar to Citrix Bleed

CSO Executive Sessions: The personality of cybersecurity leaders

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

CSO Executive Sessions: 2024 International Women's Day special

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.
Inside Track Blog
How Microsoft does IT
Taking the sting out of traveling for Microsoft employees with a bot
Jan 16, 2019 | Inside Track – retired stories

This content has been archived, and while it was correct at time of publication, it may no longer be accurate or reflect the current situation at Microsoft.
When Microsoft employees fly around the world for work, they do so to create a human connection.
Now those valuable face-to-face meetings are a bit easier, thanks to a non-human source—a bot.
The Microsoft Business Travel Letter Tool is a recently launched internal bot that makes the tedious process of filling out travel forms much easier for company employees, says Jay Clem, general manager of Human Resources IT for Microsoft Digital.
“Our use case for our international travelers turned out to be an ideal scenario to show how our Microsoft Bot Framework can be used to quickly build a bot with a lot of value,” Clem says. “Since they started using our travel letter bot, our employees are spending 80 percent less time filling out travel forms. They’re also much happier—we’ve seen a 90 percent uptick in customer satisfaction.”
It used to be that company employees would laboriously fill out the same set of lengthy forms each time they wanted to travel internationally. For frequent travelers, this was particularly vexing.
“Now all you have to do is fill out the online form one time,” says Joseph Jassey, the Microsoft Digital senior program manager who maintains and continues to develop the new bot. “Following that, the bot can generate most of the information on its own, with little manual input, which cuts down the number of mundane tasks our employees need to do.”
And employee users are liking the bot—a lot.
“Within the first few days, we had 40 out of 43 employees surveyed returning positive feedback about the experience,” says Carine Biesemeier, senior program manager in Microsoft Digital. “Our biggest hope for the automation was that it would feel natural and be a personable experience—just as if you are speaking with a person.”
When to build a bot
The new digital assistant, which is embedded in the company’s Human Resources portal, does not include first time international travelers, and this exclusion was a crucial part of the bot’s design.
It comes down to being careful about how much you tackle with an individual bot. Employees planning their first trip abroad have many different concerns to address, including general questions about travel and conduct in a new location, says Shiran Sathananthan, a Microsoft Digital principal program manager whose team led the engineering and deployment of the travel letter bot.
Sathananthan says it’s easy to create a bot that has so many user scenarios that it becomes ineffective.
“Given the myriad of ways there are to communicate the exact same ideas and questions, it can be challenging to translate the end user’s intent so that a bot can assist effectively,” he says.
To get ahead of this, limiting scope is critical.
“It’s important to not try to boil the ocean,” he says. “A bot is most effective when it answers fewer questions and has a specific scenario.”
Bots work best for manual, repetitive, predictable tasks—they are best at doing things like answering questions and resolving simple tasks. They are not as good when you need a large engineering effort or to build a complex scenario with lots of variables. “This ability to take on simple tasks is one of the reasons why Gartner identified bots as one of the ten most strategic trends of 2017,” Sathananthan says.
However, deciding when to build a bot is tricky.
You’re supposed to keep the number of things an individual bot does small, but that can lead to creating too many bots, which could lead to bloat. Conversely, creating fewer bots that have too broad of a scope or that try to handle too many scenarios can frustrate users.
The travel bot is one of many digital assistants that Microsoft Digital is using to better serve employees, says Brent Schnabel, a Microsoft Digital user experience (UX) designer who helped put together a Chatbot Toolkit that is being used guide how employees can build better bots. Each is built on the Microsoft Bot Framework, which is what the company uses to guide teams who want to build their own bots.
Beneficial for Human Resources too
The Human Resources employees who manage the Microsoft travel program are also getting a lot of value out of the new travel letter bot, Jassey says.
“The bot has dramatically reduced the number of tickets our HR practitioners have to deal with,” Jassey says.
Instead of having to help employees file loads of paperwork, the HR team is now using its time to make the traveling experience better.
Biesemeier pointed to automation as an example. “One of the challenges in creating a great employee experience is repetitive tasks, so we were looking at opportunities to automate processes,” she says.
It’s also helping with security—the travel letter bot also helps protect personal data.
“The bot can pull metadata about employees as well as their travel data, but we carefully designed it to not retrieve or store passport numbers,” Biesemeier says. Her role on the travel letter bot team was to gather requirements, identify scenarios, and define scope. She also led testing of the bot on HRWeb.
Backing out one step, the larger Microsoft Bot Framework that the team used to build the travel letter bot also makes the whole operation more efficient.
“The bot framework itself improves the self-service capabilities by doing the heavy lifting of answering bulk FAQs and reducing the shared service costs,” Biesemeier says. “We are utilizing virtual assistance to reduce cost of shared services by reducing FAQ traffic, and improving the overall employee experience.”
The travel letter bot also is one of the first in the company to meet the company’s strict accessibility standards, she said.
“We’re very proud that our bot is helping to set an internal standard for accessibility for employees with special needs,” Biesemeier says.
Advancing automation progress
The travel bot is built into HRWeb, the internal Human Resources web site that drives traffic to the bot and that socializes it.
Sathananthan would love to see the focus on bots like this one continue to strengthen and become more centralized.
“Frankly, employees are comfortable communicating with the bots, and as long as the automation returns correct information, this trust and comfort is maintained,” he says. “Whether or not the bot fulfills this is dependent on how the bot is designed, which circles back to what we discussed about scope.”
Trust is needed, and to be trusted means having consistent, accurate results. To be accurate, the bot must be able to pull the intent or key words from client input.
“For example, if someone writes, ‘I need to travel to India on the 15th of December,’ that is a rich piece of information to make use of,” Sathananthan says. “If the bot only registers ‘India,’ it is missing the other details being given.”
All the employees who worked on the project all say they are excited to see where the company can go with the travel letter bot and others like it. They believe their hopes for progress are well timed as big changes are happening at Microsoft and within Microsoft Digital to advance automation and productivity.
“We wanted to make sure we get this right from the beginning,” Schnabel says. “We worked really hard to get the design right on the travel letter bot because it’s laying the ground work for what’s to come.”
It’s all about getting user experience right.
“Well-crafted UX starts with a deep understanding of the audience and the process involved,” Schnabel says. “To get this business travel letter bot right, we researched employees who travel for work—their pain points, requirements, and the process they needed to follow. Then we implemented the foundations of Conversational User Interface (CUI) design.”
As for the travel bot itself—the team is most proud of its work to make the bot seem human.
“It paid off too, and it’s this kind of innovation that will drive us forward as a company,” Biesemeier says. “Our leadership team saw the original opportunity for automation, and once we all got together, we were able to make it happen.”
Learn more about automation and the company’s bot framework. To keep up with the changes being driven out of Microsoft Digital, follow our content on InsideTrack .
Related Stories

Creating a modern data governance strategy to accelerate digital transformation at Microsoft
This content has been archived, and while it was correct at time of publication, it may no longer be accurate or reflect the current situation at Microsoft. Data is the new currency of digital transformation. Whether it’s providing new insights, improving decision making, or driving better business outcomes, enthusiasm for unlocking the power of data... Read more

How Microsoft used change management best practices to launch a new business intelligence platform
This content has been archived, and while it was correct at time of publication, it may no longer be accurate or reflect the current situation at Microsoft. It was time for a fresh approach to data analysis at Microsoft, one that would make it easier to track sales and operations activities across regions and roles.... Read more

Bringing Microsoft’s commerce platform to Microsoft Azure
This content has been archived, and while it was correct at time of publication, it may no longer be accurate or reflect the current situation at Microsoft. For almost 20 years, our Microsoft’s Commerce Transaction Platform (CTP) processed online payments through an on-premises environment, verifying that all transactions had been processed, sales had been finalized,... Read more
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Atypical vs impossible travel #47487
BakkerJan commented Feb 5, 2020
MarileeTurscak-MSFT commented Feb 5, 2020
Sorry, something went wrong.
MarileeTurscak-MSFT commented Feb 6, 2020
MicrosoftGuyJFlo commented Feb 7, 2020
No branches or pull requests
Microsoft AI Upgrades: How They Help Tourists, Event Planners, and Business Travelers
Justin Dawes , Skift
September 21st, 2023 at 5:46 PM EDT
Few of these features seem to have been designed with travel front-of-mind, except for the corporate booking tool — that's getting close to what travelers are asking for.
Justin Dawes
Microsoft’s announcement Thursday of new tools powered by generative AI included several examples relevant to travelers.
The company said it is integrating the Copilot generative AI chatbot assistant across its suite of products. The meeting was held in person Thursday morning and streamed online later in the day.
Microsoft will begin to roll out updates to Windows 11 starting September 26, and the other products will see updates later this fall.
Microsoft was an early investor in OpenAI, so Microsoft has exclusive access to the company whose tech powers ChatGPT.
Windows 11: Make Travel Plans
Copilot in Windows 11 will take the form of a chatbot window on the right side of the computer screen, according to the announcement video, and acts as a sort of overlay meant to better connect programs across different devices and make certain processes more efficient.
Carmen Zlateff, vice president of Microsoft Windows, shared the travel-related details.
“Our Journey with AI and Windows has only just begun,” Zlateff said.
- A user planning a trip could copy a list of places to potentially visit, paste them into the Copilot window, and ask for an easily digestible summary of each place and the walking distance or time from a specific location.
- A Windows 11 user could ask the Copilot assistant to check text messages from a connected smartphone for information about upcoming flights. It would then respond with a summary that includes important flight info. The chatbot then follows up with questions, such as if the user needs help getting to the airport or navigating the destination city.
- The chatbot can answer a request for dates and times of upcoming events in a destination, such as Broadway shows in New York City with available tickets. The user can then ask Copilot to send that information via text message to a smartphone contact.
(See details about travel-related Windows 11 features starting at 16:55 in this video .)
Bing: Find Events
Microsoft relaunched Bing in February with integrations from Open AI.
The search engine has hosted more than 1 billion chats since then, according to Divya Kumar, general manager of search and AI.
With advancements in the tech since then, Bing is getting an update meant to improve personalized search results.
If the user asks about events this weekend, the search considers past searches to infer which types of events the user may be interested in and delivers results based on that information. The example of the video did not show that Bing provides relevant links in that situation.
“With just a single prompt, Bing brings me personalized results from across the web that matches my interests,” Kumar said.
(See details about travel-related Bing features starting at 26:15 in this video .)
Microsoft 365: Plan Meetings and Corporate Travel
All of the apps in Microsoft 365 — Word, Excel, PowerPoint, Outlook, and Teams — are getting upgraded versions of the Copilot chatbots that were introduced in March. It will be available to enterprise customers in November for $30 per month.
“Thanks to rapid advances over the past few months, today, we’re taking it to a whole new level,” said Colette Stallbaumer, general manager of Microsoft 365, during the event.
Microsoft 365 Chat can connect to data from all those applications to answer questions and complete tasks, the company said.
The company showed an example of how the Copilot chatbot could be useful for meetings and events planners.
A Word user can prompt Copilot to draft an event schedule based on venue and event details saved in other Microsoft documents. Copilot then presents a draft of the schedule, which the user can either copy or open in Word to edit. If the user is sharing that document with others, Copilot can write a professional intro and create a header image.
Copilot can create images from scratch or around uploaded photos through a connection with Designer, powered by the latest Dalle 3 imaging software. The Designer app, which was introduced in October 2022, includes some new AI features that can help create graphics for events marketing.
When it’s time to travel for a business event, the company showed Microsoft 365 Chat can help plan and complete bookings.
The tool can connect with a company’s travel booking system — in this case, it was the Cytric Easy platform owned by Amadeus.
Through that connection, the user can ask the chatbot to find a flight that matches certain requirements. It responds with flight options, and the user can complete the booking within the same Microsoft 365 Chat platform. If a coworker had already shared an itinerary via email, the user can also ask the chatbot to find a flight that matches that itinerary.
(See an example of the business travel capability starting at 37:38 in this video .)
Have a confidential tip for Skift? Get in touch
Tags: artificial intelligence , business travel , chatgpt , corporate travel , event planners , generative ai , meeting planners , meetings and events , microsoft , online travel , online travel newsletter , OpenAi , tourism , trip planning
Photo credit: Microsoft is integrating the Copilot AI assistant across all of its products. efes / Wikimedia Commons

Mirosoft candidate travel policy
Please submit your expenses within 30 days of your interview date. The below outlines the expense categories and limitations that are eligible for reimbursement, and expenses that cannot be reimbursed. Microsoft assumes no obligation to reimburse candidates for expenses that are not in compliance with this policy. All expense information that you submit will be used for the sole purpose of processing your reimbursement only. If you have questions, please contact your Interview Scheduler.
Emergency and en-route changes
Candidates may use the 1-669-210-80-41 (prompt #2) travel phone number for changes Monday – Friday from 7 am to 6 pm PST only. For candidates located in India, please use the toll free 1-860-419-12-73 travel phone number for changes Monday – Friday from 9 am to 8 pm IST only. This number also appears on your itinerary. Air, hotel, or car reservation emergency change requests requiring additional charges must have authorization from the Microsoft Travel Team.
Expense categories
Any expenses outside of air, hotel, ground transportation and meals must be pre-approved by your recruiter.
Upgrades are permitted at the candidate's personal expense and are not reimbursable. Microsoft will not reimburse candidates for personal items lost while traveling for interviews. The ultimate responsibility for retrieving and compensating for lost baggage lies with the airlines.
Candidates are required to present a valid credit card upon check-in at hotels to cover non-reimbursable incidentals (refer to non-reimbursable items below).
Telephone and internet
Microsoft will reimburse up to $30 USD or equivalent currency per day for either long distance calls or internet access charges (receipts required).
Ground transportation
Transportation expenses include fees at airport facilities, taxi fares or ride share costs (Uber, Lyft, etc.) specifically for rides home to/from airport, airport to hotel, airport to Microsoft campus or hotel to Microsoft campus. Personal mileage is reimbursed at the current US IRS standard mileage going rate per mile. If you rent a car, Microsoft encourages you to refuel the vehicle prior to returning and expensing the fuel cost.
Candidates will be reimbursed for personal meal expenses according to actual and reasonable costs, using the guidelines below and not to exceed daily amount of $75 USD or equivalent currency. Do not expense meals that have been billed to your hotel invoice, which will be paid by Microsoft.
Do not group single day meal expenses - please itemize.
- Breakfast $15 USD or equivalent currency per day (including beverages, tax and gratuity)
- Lunch $20 USD or equivalent currency per day (including beverages, tax and gratuity)
- Dinner $40 USD or equivalent currency per day (including beverages, tax and gratuity)
Non-reimbursable items
Include, but are not limited to:.
Airline upgrade certificates
- Alcohol or mini-bar charges
- Baby-sitting and childcare
- Barber, hair stylist, manicurist, and other grooming costs
- Briefcases and luggage
- Family / partner accompanying traveler
- Frequent flyer award tickets
- Free flight, hotel or car rental coupons
- Gambling losses
- Hotel upgrades
- Laundry or dry-cleaning charges
- Massage and other spa charges
- Magazines or newspapers
- Personal aircraft or non-approved aircraft charter expenses
- Personal credit charge card fees and interest charges
- Movie, videos or DVD rentals in hotel room
- Movie theatre tickets
- Earphones in flight
- Pet-boarding expenses
- Sports and Social Club (golf, country, tennis clubs) dues and memberships
- CDW (Collision Damage Waiver)
- LDW (Loss Damage Waiver)
- PAI (Personal Accident Insurance)
- PEC (Personal Effects Coverage)
- LIS (Liability Insurance Coverage)
- Traffic, speeding and parking tickets
- Travel expenses for other individuals
- Trip or flight insurance
Receipt requirements
Please submit original itemized receipts for all expenses. If the supplier cannot provide an itemized receipt, indicate such in the additional comments.
Please submit original itemized receipts for all transactions, except for taxi expenses less than 20 AZN.
Please submit original itemized receipts for expenses over CAD $30 when travelling domestically and over CAD $75 when travelling internationally.
Must submit original itemized receipts for all transactions less than 100 EUR. For expenses exceeding 100 EUR a fiscal invoice is required.
Indonesia, Myanmar, Philippines
Please submit original itemized receipts for all expenses except for local taxi fares.
Please submit original itemized receipts for all transactions less than 400 RON. For expenses exceeding 400 RON a fiscal invoice is required.
Must submit original itemized receipts for all transactions. Fiscal invoice is required for expenses paid by cash exceeding 1,000 EUR and for expenses paid by card exceeding 1,600 EUR.
Government official policy
As a government official, you should have completed the Interview and Travel Assurance form as part of your application at Microsoft. You should have also been contacted by your Interview Scheduler to arrange the travel logistics for your interview. Following your interview and per the Microsoft candidate travel policy, you will need to submit your reimbursable expenses through the expense reimbursement form in your Action Center.
Rental car accident
If you are involved in an automobile accident while interviewing with Microsoft that causes damage to another vehicle; damage to your rental car; bodily injury to yourself or your passenger(s), a pedestrian, or the occupants of another vehicle; or if your rental car and/or its contents are stolen, you should:
- Do not admit liability.
- Notify the local police and obtain a copy of the police report if one is written.
- If there is no police report, note the following things: name, badge number and department of the investigating police officer; time and location of the accident; estimated speed of the vehicle(s); visibility; traffic, road and weather conditions; other driver's name, address, phone number, driver's and car license numbers, registration and insurance information; the names addresses and phone numbers of any witnesses; description of damage to car and other property; extent of injuries, if any.
- Call the car rental agency even if the damage does not appear visible.
- Obtain the names, addresses and vehicle information from other drivers and vehicles involved; note the time and location of the accident; and record the names, telephone numbers and vehicle licenses of any witnesses.
- Fill out a rental car accident form even if the damage does not appear visible (usually located in the glove box of the rental car). Failure to fully complete the rental company accident form voids the loss damage waiver and other protections.
The request is blocked.
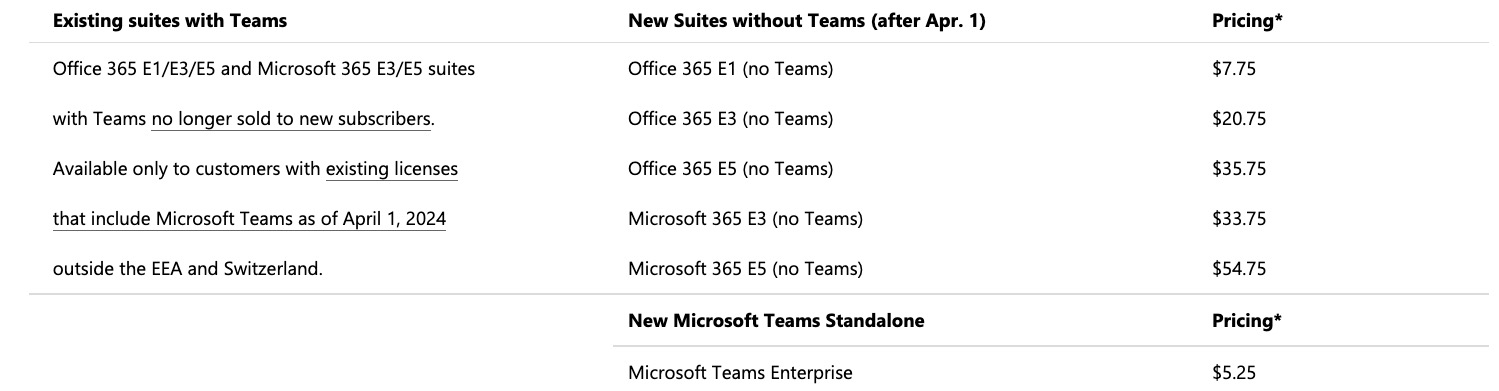
Microsoft unbundles Office and Teams globally following years-long criticism

Microsoft has introduced new versions of Microsoft 365 and Office 365 subscription services that exclude its business collaboration chat offering Teams following scrutiny from the European Union regulator and complaints from rival Slack.
The move — which some analysts say is unlikely to change the commercial growth trajectory of Office 365 — follows Microsoft agreeing to sell Office 365 suite sans Microsoft Teams offering in the EU and Switzerland last year. At the time, the software giant said it was making the changes to address the concerns raised by the European Commission.
“Globally consistent licensing helps ensure clarity for customers and streamline decision making and negotiations,” the company wrote in a blog post Monday. The company introduced Teams as a complementary offering to the Office 365 suite in 2016. It has amassed over 320 million users.
Microsoft said it is also introducing a new standalone Teams offering for enterprise customers outside the EU and Switzerland.
Though Microsoft has long allowed businesses to pay separately for Teams, it has also offered the service bundled in the widely popular Office 365 suite. The latter has upset some competitors with some asserting that the tech giant was leveraging its position in an unjust manner to gain a competitive edge.
Slack, owned by Salesforce , has termed Microsoft’s actions “illegal” in the past, alleging that the Windows-maker forced installation of Teams to customers through its market-dominant productivity suite and hid the true cost of the chat and video service .
Microsoft didn’t address these concerns in its blog, but said as part of the change, it is offering flexibility to its existing customers, allowing them to maintain their current bundled package that includes Teams, Office and other products. These customers can choose to renew their current deal, update it or select a new offer that better suits their needs.
For new customers, Microsoft has introduced standalone pricing for Teams at $5.25 per user per month. Additionally, Office packages without Teams will be available at prices ranging from $7.75 to $54.75, depending on the specific package and features included.
The new Microsoft suite offering with Teams (Image: Microsoft)

Microsoft is also introducing a new variant of Microsoft 365 Business that excludes Teams. Image Credits: Microsoft
In a note seen by TechCrunch, Morgan Stanley analysts estimated that Microsoft’s Monday decision is “unlikely to change the O365 commercial growth trajectory, as more consolidation (not less) seems to be the direction of travel for CIO’s due to macro pressures and technological progress like GenAI driving stronger gains for the broader suites and deeper data sets.”
“Further, providing more choice for purchasing Teams clearly illustrates its compelling value, at just $5.25 per user per month for New Microsoft Teams Enterprise (standalone), which compares to Slack Pro at $7.25/mo and Slack Business+ at $12.50/mo. The price reduction in the Enterprise Suites without Teams is only $2.25, yet the Standalone cost is $5.25. For new customers, this equates to a pricing increase. Using Teams in F1 SKU’s costs only $0.50 per user per month and using Teams in Business SKU’s cost only $1.25-$2.25 per user per month,” wrote the analysts.

Image credits: Morgan Stanley
The story was updated with details from Microsoft’s official blog and Morgan Stanley’s comment.

IMAGES
VIDEO
COMMENTS
Overview. "Impossible travel" is one of the most basic anomaly detections used to indicate that a user is compromised. The logic behind impossible travel is simple. If the same user connects from two different countries and the time between those connections can't be made through conventional air travel, it's an impossible travel ...
Here are the steps to follow: Sign in to the Microsoft 365 admin center. Go to the Security and Compliance Center. Select 'Policies' from the left navigation menu. Click on 'Azure AD Conditional Access.'. Click on 'New Policy' to create a new policy. Give your policy a name and description. Select 'Users and groups' to specify ...
TP: If you're able to confirm that the location in the impossible travel alert is unlikely for the user. Recommended action: Suspend the user, mark the user as compromised, and reset their password. FP (Undetected user travel): If you're able to confirm that the user recently traveled to the destination mentioned detailed in the alert. For ...
Blumira's Free edition easily connects to Microsoft 365 to detect and respond to threats in minutes. Impossible travel activity is just one example of what you can detect with Blumira Free. Other unusual activity detections include: Any activity from anonymous or suspicious IP addresses. Activity from infrequent countries or terminated users.
Well maybe, but in the context of Microsoft Office 365, Impossible Travel is a security feature that is a great indicator of potential hacking attempts. The concept is straightforward. If you login to Office 365 from your office in Boston and then 20 minutes later you try to login from Dallas, or you login from home in Chicago and five hours ...
In the Microsoft Defender Portal, go to Cloud Apps -> Policies -> Policy management. Then choose Anomaly detection policy for the policy type. Select the policy you want to scope. Under Scope, change the drop-down from the default setting of All users and groups, to Specific users and groups.
To simulate an atypical travel risk detection, perform the following steps: Using your standard browser, navigate to https://myapps.microsoft.com. Enter the credentials of the account you want to generate an atypical travel risk detection for. Change your user agent. You can change user agent in Microsoft Edge from Developer Tools (F12).
I am currently using the impossible travel alert for Office 365 logins. However, the alert goes off even if the login from an impossible travel location was unsuccessful. This has made this alert useless because these unsuccessful logins are happening all the time as bots and bad actors are constantly trying to log in to my users accounts.
Microsoft Bing - Travel helps you in your travel journey starting right from inspiration, to exploration, planning and booking a trip. Find places, flights, hotels, packages and many more...
I have been testing out Microsoft 365 E5 features, and came across this quesiton. I was looking through AAD Identity protection risks, and noticed a user detected with an "Atypical travel" risk and "Impossible travel" risk. I was checking this page to see what each risk meant, but had trouble understanding the difference between these two risks.
Sep 07 2021 11:50 PM. @DJB This probably depends on the SIEM solution. Usually what happens is that both services are being ingested with different connectors or whatever they're called for your SIEM. In that sense, the SIEM needs to be able to determine that it's the same alert if both alerts come in via a different route.
Verify country-level locations are both unsafe. If after 7 days and logins from clearly different non-VPN locations don't trigger alerts, some policy configuration adjustments may be needed. Hello there I am trying to test the Impossible Travel Alert in the Microsoft Defender for Cloud Apps. For that, I use the NordVPN to login from 2.
As summer travel season approaches, companies streamline operations and reimagine team member and traveler experiences with the Microsoft Cloud FORT WORTH, Texas, and REDMOND, Wash. — May 18, 2022 — American Airlines and Microsoft Corp. are partnering to use technology to create better, more connected experiences for customers and American Airlines team members, supporting the […]
Risk detections in Microsoft Entra ID Protection include any identified suspicious actions related to user accounts in the directory. Risk detections (both user and sign-in linked) contribute to the overall user risk score that is found in the Risky Users report. ID Protection provides organizations access to powerful resources to see and ...
Go to the Azure AD Identity Protection page and set up the sign-in risk policy. To set up the policy, click on "Azure AD Identity Protection - Sign-in risk policy". Set the policy to either ...
The Microsoft Business Travel Letter Tool is a recently launched internal bot that makes the tedious process of filling out travel forms much easier for company employees, says Jay Clem, general manager of Human Resources IT for Microsoft Digital. "Our use case for our international travelers turned out to be an ideal scenario to show how our ...
Microsoft has taken a bold step to further reduce its impact on the environment by upping the cost of internal penalties for business travel. The technology giant will raise its carbon emission ...
I believe that the distinction is that impossible to travel to locations would mean that the user signed into two far-away locations within a timeframe that would make it impossible to travel to that quickly (London to Cleveland within the span of one hour). Atypical locations would track when someone travels to geographically distant locations ...
Microsoft 365: Plan Meetings and Corporate Travel. All of the apps in Microsoft 365 — Word, Excel, PowerPoint, Outlook, and Teams — are getting upgraded versions of the Copilot chatbots that ...
Candidates may use the 1-669-210-80-41 (prompt #2) travel phone number for changes Monday - Friday from 7 am to 6 pm PST only. For candidates located in India, please use the toll free 1-860-419-12-73 travel phone number for changes Monday - Friday from 9 am to 8 pm IST only. ... Following your interview and per the Microsoft candidate ...
zion609. •. You would need to set up trusted locations if using Conditional Access policies if I'm not mistaken, with at least Azure AD P1 license. For impossible travel detection, it would requires P2 license as I believe the feature is part of risk based user sign in. TLDR: cheapest solution is to addon P2 license imo.
Please click on the specific area of the page that your feedback is related to so it can be sent to the correct team.
Microsoft Travel - MSN ... Feedback
The price reduction in the Enterprise Suites without Teams is only $2.25, yet the Standalone cost is $5.25. For new customers, this equates to a pricing increase. Using Teams in F1 SKU's costs ...