

BBD header search block
Apply for a disabled person's travel pass.
Travel passes are issued free of charge by Travel South Yorkshire and entitle the holder to free travel within South Yorkshire on:
- local bus services, trams and trains
- Northern Rail services between South Yorkshire and West Yorkshire
- buses throughout England at off-peak times (these are between 9:30am and 11pm weekdays, all day at weekends and on Bank Holidays)
Qualifying benefit
If you receive one of the following, you will automatically qualify for a Disabled Persons Travel Pass. You must apply directly to Travel South Yorkshire providing evidence of your qualifying benefit.
- higher rate mobility component of Disability Living Allowance (DLA)
- Personal Independence Payment (PIP) standard rate mobility with an award of at least 8 points for Moving Around or Communicating Verbally
- PIP Enhanced Rate for Mobility (at least 8 points awarded for moving around)
- War Pensioner’s mobility supplement
If you have no qualifying benefit
If you live in South Yorkshire, you may qualify for a pass if you:
- are blind or partially sighted
- are deaf or without speech
- have a disability which has a substantial and long-term adverse effect on your ability to walk
- do not have arms or have long-term loss of the use of your arms
- have a learning disability
- have been or would be refused a driver’s licence on medical grounds (other than on the grounds of persistent misuse of drugs and alcohol)
- PIP standard rate mobility (at least 8 points awarded for planning and following a journey)
- PIP enhanced rate mobility (points awarded for planning and following a journey)
Travelling with a carer
If you qualify for a Travel Pass and are in receipt of:
- higher rate care component of Disability Living Allowance with some mobility
- PIP Enhanced daily living
- higher rate Attendance Allowance
Your Travel pass will allow one carer to travel with you for free.
Contact Customer Services
Want to talk to someone right now, is this page helpful.
You might also like… Blue Badge
You are using an outdated browser. Please upgrade your browser to improve your experience.
About your privacy and cookies
We use cookies to help make our website and services better. You consent to our use of cookies if you continue to use this website.

You are here:
Disabled person's travel pass.
A disabled person's travel pass entitles people to free travel at all times within South Yorkshire on:
- local bus services, trams and trains
- Northern Rail services between South Yorkshire and West Yorkshire
- buses throughout England at off-peak times (between 9.30am and 11pm weekdays, all day at weekends and on bank holidays)
You can't use your pass to travel on trams outside of South Yorkshire.
Travel passes are issued free of charge by Travel South Yorkshire .
How to qualify for a pass
You'll automatically qualify for a pass if you're under the age of 66 and:
- you receive the Higher Rate Mobility Component of Disability Living Allowance (DLA)
- you receive Personal Independence Payment (PIP) with an award of at least eight points in either 'moving around' or 'communicating verbally'
- you receive a War Pensioner's Mobility Supplement
- you have a Blue Badge parking permit
If you qualify for a pass and also receive one of the following benefits, the pass you receive will allow a carer to travel with you free of charge as well:
- Higher Rate Care Component of DLA
- Higher Rate Attendance Allowance
- Enhanced Daily Living Component of PIP
Applying for a pass
If you automatically qualify you can apply online for a travel pass by setting up an account with Travel South Yorkshire.
You'll need to provide copies of:
- proof of your age
- proof of your address
- proof of entitlement
- a recent passport-sized photograph of yourself
For online applications you can scan and upload the documents. If you're applying in writing you'll need to enclose a copy of your documents with your application.
If you don't automatically qualify
You may also be eligible for a pass if you live in South Yorkshire, you're under the age of 66 and:
- are blind or partially-sighted
- are deaf or without speech
- have a disability that has a substantial effect on your ability to walk
- do not have arms or have lost the use of your arms
- have a learning disability (local council registered)
- have been refused a driver's licence or would have been refused on medical grounds (but not for drug or alcohol misuse)
If you're over 66 years of age you may still qualify for a disabled pass if you're blind or partially sighted or if you require a carer to assist you when travelling.
We provide a free checking service on behalf of Travel South Yorkshire to confirm whether people who don't automatically qualify are eligible for a travel pass.
You can ask us to check is you're eligible using our online form below. If you are eligible, we'll issue you with a letter of entitlement. You'll need to provide this to Travel South Yorkshire to prove you can apply for a pass.
You can either scan your evidence documents or take a photo of them when you complete our form. You'll need to upload:
- proof of your eligibility (disability)
- proof of your age (your passport, NHS card, driving licence or birth certificate)
- proof of your address (a Council Tax or utility bill, or your NHS card)
Only fill in our online form to check if you're eligible if you don't automatically qualify for a pass.
Please allow seven days from submitting your application and proofs for us to make a decision.
When you've received your letter of eligibility or you meet automatic criteria you need to apply online for a travel pass . If you can't apply online you can contact Traveline for more advice on (01709) 515151.
Renewing an expired pass
For advice about renewing, call Traveline on (01709) 515151 up to two months before the expiry date to check that you are still entitled to a travel pass. They will advise you if you need a letter of entitlement from us.
If you are eligible, you can renew your travel pass online or fill in a paper travel pass application form .
Lost or stolen passes
Contact Travel South Yorkshire if you have lost your pass or it has been stolen. There is a charge for replacement passes.
A - Z Directory

Apply for a travel pass
You may be entitled to reduced travel, or even free travel, on bus services, trams and trains within South Yorkshire if you are:
- under 16 year old
- aged 16-18 years
- need to use public transport to get to school
- a disabled person
- a senior citizen.
All of these passes are issued by South Yorkshire Passenger Transport .
To apply for the following passes you will need proof of entitlement from your local Council:
- disabled person’s pass
- disabled person plus carer pass
- visually impaired person’s pass
- visually impaired person plus carer.
This site requires a JavaScript enabled browser. Please enable Javascript or upgrade your browser to access all the features.

Disabled Person's Bus and Train Pass
What a Disabled Person's Bus and Train Pass is, whether you qualify for a pass, how to apply or renew your pass, and what to do if you lose your pass. Including information about senior bus passes.
With a Disabled Person's Bus and Train Pass you can travel for free:
- on buses, trains and trams in South Yorkshire at any time.
- on Northern Rail trains between South Yorkshire and West Yorkshire.
- on any off-peak (9.30am to 11pm) and all day at weekends and bank holidays on any local bus journey in England.
If you want to help with parking accessibility, you need to apply to the Blue Badge scheme .
Do I qualify for a Disabled Person's Bus and Train Pass?
You will qualify for a Disabled Person's Bus and Train Pass if you live in Doncaster and you meet any of the following conditions:
- You are registered with one of the following disabilities with Doncaster Council Social Services
- Partially sighted
- Physically disabled
- Without speech
- You have a Learning disability
- You have been issued a Blue Badge (for parking) by Social Services
- You are in receipt of the higher rate mobility component of Disability Living Allowance (DLA)
- You are in receipt of Personal Independence Payment (PIP) with an award of 8 points in either “Moving Around” or “Communicating”.
- You are in receipt of a War Pensioner's Mobility Supplement
- You have been refused, or had your driving licence taken off you on medical grounds (other than on the grounds of persistent misuse of drugs and/or alcohol)
- A doctor or other medical professional has recommended that you do not apply for a driving licence for medical reasons, for example, because you have epilepsy.
- You have a disability or injury that has a substantial and long-term effect on your ability to walk
How do I apply for a Disabled Person's Bus and Train Pass?
- the higher rate mobility component of Disability Living Allowance, or
- Personal Independence Payment (PIP) with an award of 8 points in either “Moving Around” or “Communicating”, or
- a War Pensioner's Mobility Supplement,
The Disabled Person's Bus and Train Pass Application is made online; Doncaster Digital Venues is a list of locations in Doncaster where you can access a computer to claim.
If you need to provide information to support your application please complete the Disabled Person's Bus and Train Pass medical information request form, which is in the Downloads and Resources area at the bottom of this page, and email the completed form to [email protected]
Once we have all the information we need, we will write to you and let you know whether you are entitled to a pass. If you are entitled, to obtain your pass you must apply for a pass online attaching a scanned image or a photograph of the award letter and other evidence they need. If you do not have access to apply online you can phone travel South Yorkshire on 01709 515151.
The 'with carer' pass
A carer may be entitled to travel for free with you if you already qualify for a pass and also receive any of the following:
- the higher rate care component of Disability Living Allowance, or
- the higher rate of Attendance Allowance, or
- the enhanced rate living component of Personal Independence Payment (PIP)
To apply for a ‘with carer’ pass, please provide proof of your Disability Living Allowance, Attendance Allowance or Personal Independence Payment.
The carer can be anyone helping you to travel, such as a relative, friend, support worker or professional carer. It does not have to be the same person every time.
How long does my Disabled Person's Bus and Train Pass last?
The expiry date is shown on the front of the pass. Your pass normally lasts for up to five years, or until you reach 66 years of age, whichever comes first.
If you are blind or partially-sighted, your pass will automatically be renewed.
How do I renew my Disabled Person's Bus and Train Pass?
What if i lose my disabled person's bus and train pass.
Contact Travel South Yorkshire by phone on 01709 515151, by post (address is above) or dropbox at the Doncaster Interchange. A charge is made for issuing a replacement.
You should also contact Travel South Yorkshire if your pass is stolen, damaged or your address details change. Stolen passes will be replaced free of charge if you have a police crime reference number.
Further details can be obtained from Travel South Yorkshire.
Looking to apply for or renew a Senior Bus Pass?
Downloads & resources.
Run this page through the AI Enrichment process?: No
Display your introduction over featured image?: No
Did you find this page helpful?
Sorry to hear that. why wasn't it helpful, did you try using our search or a-z to find what you wanted, please try our search or a-z first..
These facilities can be found in the header of every page:
Do you want us to follow this up with you?
By clicking Submit, you consent to us contacting you in the future via email about this issue.

- Transport and access
- Older people
TRAVEL SOUTH YORKSHIRE - SENIOR TRAVEL PASSES
South Yorkshire
With a Senior Pass you are entitled to free off peak travel on buses across England (plus additional concessions in South Yorkshire) through the English National Concession Travel Scheme (ENCTS).

Description
Eligibility .
- You must live in South Yorkshire
- From your 66th birthday
You can apply for your pass online up to 2 weeks in advance of when you qualify.
- Free travel on local bus services and trams within South Yorkshire between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays.
- Half fare on Northern train services for travel between stations on the South Yorkshire rail network between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays
- Free travel on buses in all other parts of England between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays. (This pass is not valid on tram services outside South Yorkshire.)
- Free of charge (first issue)
- Free travel on Stagecoach services to hospital appointments before 0930 - please visit the Stagecoach website for further details.
Please be aware that no pass means that you could pay full fare.
Apply online...it's easy!
Set up a MyTSY account in your name (or log in if you already have an account)
Log in > Select Passes from the top menu > Concessions > Senior Pass
Complete all personal details and upload proof documents - visit our ‘What you need to apply’ guidelines page
Upload your photo – see the ‘Acceptable Photograph’ guidelines page as an unsuitable photo could delay your application
Check your order and go to checkout.
If all the details are correct your pass will be dispatched within 11 days of receiving your completed online application.
Apply by post
Download an application form (PDF, 511Kb)
Complete all personal details and post to the address below together with a photograph and photocopies of proof documents.
Contact Centre SYPTE 11 Broad Street West Sheffield S1 2BQ
If all the details are correct your pass will be dispatched within 25 days of receiving your completed application form.
Please note proof documents must be photocopies and not original documents as all documents are destroyed once the pass is ordered.
A completed application form can also be submitted by dropping it off at the Customer Service Desk at your local Travel South Yorkshire Interchange .
Pass Protection
Pass protection can be taken out against Senior Citizen Passes for £5 for the duration of your pass, up to five years.
This will enable you to replace your old pass free of charge should you lose it during the time in which it is valid.
Address details:
Published: 09 August 2019
Cookies on GOV.UK
We use some essential cookies to make this website work.
We’d like to set additional cookies to understand how you use GOV.UK, remember your settings and improve government services.
We also use cookies set by other sites to help us deliver content from their services.
You have accepted additional cookies. You can change your cookie settings at any time.
You have rejected additional cookies. You can change your cookie settings at any time.
- Department for Science, Innovation & Technology
Cyber security skills in the UK labour market 2024
Published 16 September 2024

© Crown copyright 2024
This publication is licensed under the terms of the Open Government Licence v3.0 except where otherwise stated. To view this licence, visit nationalarchives.gov.uk/doc/open-government-licence/version/3 or write to the Information Policy Team, The National Archives, Kew, London TW9 4DU, or email: [email protected] .
Where we have identified any third party copyright information you will need to obtain permission from the copyright holders concerned.
This publication is available at https://www.gov.uk/government/publications/cyber-security-skills-in-the-uk-labour-market-2024/cyber-security-skills-in-the-uk-labour-market-2024
This is a summary of research into the UK cyber security labour market, carried out on behalf of the Department for Science, Innovation and Technology ( DSIT ). The research explores the nature and extent of cyber security skills gaps (people lacking appropriate skills) and skills shortages (a lack of people available to work in cyber security job roles) using:
Representative surveys of cyber sector businesses and the wider population of UK organisations (businesses, charities and public sector organisations) [footnote 1] .
Qualitative research with recruitment agents, cyber firms and medium/large organisations in various sectors.
A secondary analysis of cyber security job postings on the Lightcast labour market database, as well as reviewing the supply of cyber security talent through sources such as the Higher Education Statistics Authority ( HESA ) and Jisc.
This is the sixth iteration of the research, which has been carried out on an annual basis since 2019. This report on the cyber security labour market is consistent with the key learnings from previous years. The main findings are as follows:
Across the economy, around half (44%) of businesses have skills gaps in basic technical areas. Incident management skills gaps have increased from 27% in 2020 to 48% in 2024.
Demand for cyber security professionals has fallen, with core cyber job postings decreasing by 32% between 2002 and 2023. There have been challenging macroeconomic factors and job cuts in the technology sector, but cyber security has been more resilient than the wider digital sector.
The UK has made significant improvements in training new potential talent for the cyber security labour market and the number of cyber security graduates has increased by 34%.
Skills gaps
The proportion of UK businesses with basic and advanced technical skills gaps has not changed significantly across the 6 years of data. We estimate that approximately 637,000 businesses (44%) have a basic skills gap, where employees responsible for cyber security lack the confidence to carry out the basic tasks laid out in the government-endorsed Cyber Essentials scheme, and are not using external cyber security providers for these tasks. Approximately 390,000 businesses (27%) have gaps in advanced skills, such as penetration testing. These are skills which are not outsourced, and which are considered important (i.e. appropriate for businesses with more complex cyber security needs).
We estimate that 30% of cyber firms in 2024 have faced a problem with a technical skills gap, which is lower than in 2023 (49%). There has been a significant decline in reported skills gaps across many areas, for instance security testing (23%, down from 35%). In contrast, the skills gap for cryptography and communication security has increased (24%, up from 12%).
In the qualitative research, employers and recruiters thought that AI is likely to have a major impact on the cyber skills landscape, although there was a great deal of uncertainty about what the future will look like. Four potential changes were identified; increasing automation of cyber tasks (which could lead to job losses), the need for skills to understand and act upon AI tools, roles becoming ‘ AI cyber’ rather than just ‘cyber’ and the emergence of deep specialisms such as ‘cyber security machine learning.’
The diversity of the cyber sector workforce is consistent with previous years. There were signs of an upward trend in 2022 for women and people from ethnic minority backgrounds but this has not been sustained. People from ethnic minority backgrounds make up 15% of the sector workforce, and 9% of those in senior cyber roles (i.e. requiring 6 or more years of experience). 17% of the workforce are female and women account for 12% of senior roles. 13% are neurodivergent, and this group makes up 8% of senior roles. 6% are disabled, with 4% in senior roles. This suggests that diversity remains an embedded and persistent challenge in the UK’s cyber security workforce.
Recruitment and staff retention
Demand for cyber security professionals has fallen, a trend reflected across the digital and wider sectors. This decline has taken place against a backdrop of challenging macroeconomic conditions and technology layoffs worldwide. The number of core cyber job postings has decreased by 32% (from 71,054 in 2022 to 97,319 in 2023). Other job postings requesting cyber security skills have also decreased by 39%. However, whilst the number of vacancies has reduced, we estimate that employment in the cyber workforce has still increased by 5% within the last year (as new individuals enter the workforce and fill sustained demand for roles).
The number of students enrolled in cyber security courses has increased by 14% (from 18,270 to 20,890) and the number of students graduating in a cyber security course has also increased by 34% (from 4,330 to 5,790). In 2022/23 there were 580 new starts on cyber security apprenticeships in England, an increase of 18%.
As with previous years, cyber sector businesses reported that they find positions for staff with 3 to 5 years of experience the hardest to fill and 61% of job postings request 2-6 years of experience. However, lack of work experience has become less of an issue for cyber sector firms who had hard-to-fill vacancies, declining between 2021 (35%), 2023 (27%) and 2024 (16%).
There is some evidence of a move away from remote working which had become widespread during the pandemic. In the qualitative research, some employers observed more people are returning to the office and recruiters said that clients are increasingly requiring candidates to be based in specific locations. This is reflected in the job postings analysis, where the proportion of postings with no regional location listed (i.e. the roles were marked as ‘Remote’ or ‘UK-wide’) has fallen from 28% to 22%. We estimate that there is a need for c.6,800 new people each year to meet demand, in addition to the c.4,800 to replace those exiting the sector, i.e. a total requirement of c.11,600 per year. A total of c.8,100 individuals entered the cyber security workforce in 2023, leaving an estimated shortfall in 2023 of c.3,500 people. This is lower than last year’s estimate of c.11,200. However, even though the workforce gap has decreased this year, the total shortage of cyber security professionals continues to grow each year as the unmet demand from previous years accumulates.
1. Introduction
1.1 about this research.
The Department for Science, Innovation and Technology ( DSIT ) commissioned Ipsos and Perspective Economics to conduct the latest in an annual series of studies to improve their understanding of the current UK cyber security skills labour market. In February 2023 the parts of The Department for Digital, Culture, Media and Sport ( DCMS ) responsible for cyber security policy moved to the new Department for Science, Innovation and Technology ( DSIT ). The previous study was published by DSIT in 2023 : (fieldwork in 2022). The studies prior to this were published by DCMS in 2022 (fieldwork in 2021), 2021 (fieldwork in 2020), 2020 (fieldwork in 2019) and 2018 (fieldwork in 2018).
The 2024 research, in line with previous years, aimed to gather evidence on:
- Current cyber security skills gaps (i.e. where existing employees or job applicants for cyber roles lack particular skills)
- Current skills shortages and the level and type of job roles they affect (i.e. a shortfall in the number of skilled individuals working in or applying for cyber roles)
- The role of training, qualifications, recruitment and outsourcing to fill skills gaps
- Where the cyber security jobs market is active geographically
- The roles being labelled as cyber roles versus ones that are not but require a similar skillset
- The role that recruitment agents play in the cyber security labour market
- Diversity within the cyber sector
- Staff turnover in the cyber sector
- Statistics on the size of the UK’s cyber security recruitment pool
- An estimate of the overall cyber workforce gap
- Recruitment agents’ views of the recruitment pool and how it has changed in the last year
For reference, any mention of ‘cyber’ throughout this report refers to the cyber sector. Any reference to ’cyber security’ refers to how individuals and organisations reduce the risk of cyber-attacks and is a component of working in a cyber sector role. Any reported change between years within this report is statistically significant to 95%.
1.2 Summary of the methodology
This section contains a brief outline of the research methodology. Greater methodological detail can be found in the accompanying technical report.
The methodology consisted of 4 strands:
Quantitative surveys – Ipsos conducted a representative telephone survey with 4 audiences: general businesses, public sector organisations, charities and cyber sector firms. The main estimates on skills gaps and shortages reported in this study are based on the survey data. Fieldwork was between 11th August and 10th November 2023.
Qualitative interviews – Ipsos conducted a more focused strand of qualitative research, with 28 in-depth interviews split across cyber firms, medium and large businesses and public sector organisations, and recruitment agents. The interviews explored the challenges these organisations faced in addressing skills gaps and shortages, and the approaches they were taking on recruitment, training and workplace diversity. Interviews took place between September and November 2023.
Job vacancies analysis – Perspective Economics analysed cyber security job postings on the Lightcast labour market database, showing the number, type and location of vacancies across the UK. This also covers remuneration, descriptions of job roles and the skills, qualifications and experience being sought by employers. This work primarily covered vacancies across the 12 months of 2023, supplementing the work done in the 2023 study (which covered vacancies from January 2022 to December 2022).
Supply side analysis – Perspective Economics replicated the methodology used on the 2021 cyber recruitment pool research to estimate the overall size of the current recruitment pool, as well as those likely to be entering the pool within the next 12 months (across 2023). This strand produces further statistics on the diversity, educational and occupational backgrounds, and salaries of this pool of labour, as well as outflows from the pool.
1.3 Acknowledgements
Ipsos and Perspective Economics would like to thank colleagues at DSIT for their project management, support and guidance throughout the study.
2. Who works in cyber security roles?
This chapter explores the people covering cyber security across organisations, including their career pathways into the role, their specialisms and the qualifications they hold.
For context, outside the cyber sector, we asked participating organisations to choose the staff member most responsible for their cyber security to complete the survey. Just like in the previous years’ surveys, these individuals are typically not cyber professionals.
2.1. Size of cyber teams
Cyber teams outside the cyber sector.
Just under half of business (46%) have 1 person involved in running or managing their organisations cyber security. For charities this is lower at just over a third (35%), however, the public sector appears to be the best resourced when it comes to cyber security with only one in ten organisations (10%) having a cyber security team of 1 person. Cyber teams seem to have a similar level of staffing to last year, the percentage of organisations having just 1 person to manage cyber security among the private (50%), public (17%) and charity (47%) sectors have remained stable. The median cyber team size for public sector organisations was 3 people while for private sector organisations it was 2.
Figure 2.1 demonstrates that larger businesses are more likely to have cyber teams of more than 1 person, as was found last year. Large, medium or even small companies are less likely to have teams of 1 person than micro-organisations. Among medium and large businesses, the median cyber team size was around 3. In line with last year, under a fifth of large (19%) and medium (15%) businesses had 4-5 people in these roles.
Figure 2.1: Percentage of businesses with just 1 employee responsible for cyber security
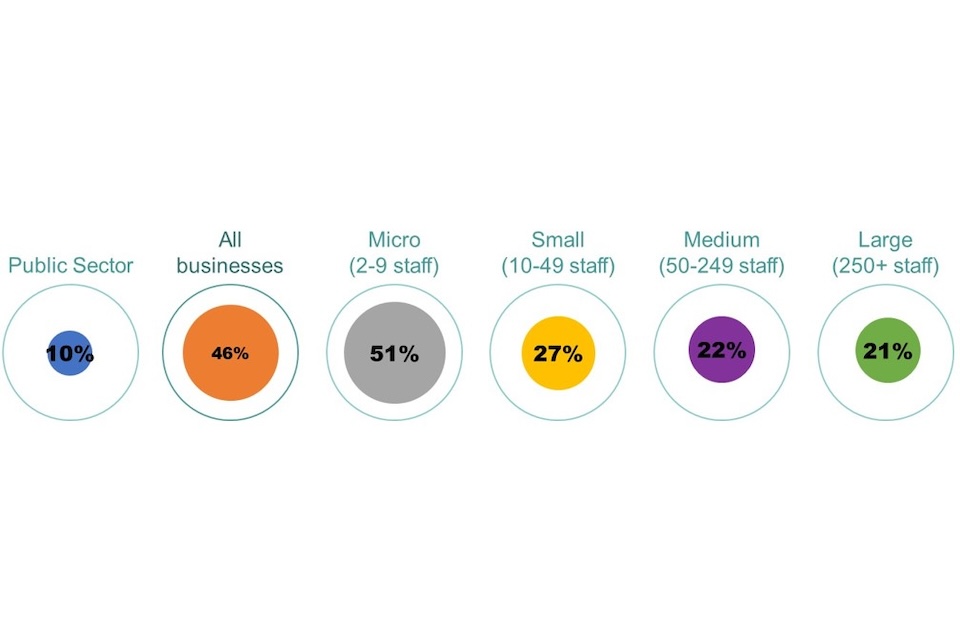
Figure 2.2: Percentage of businesses with just 1 employee responsible for cyber security (trend data)
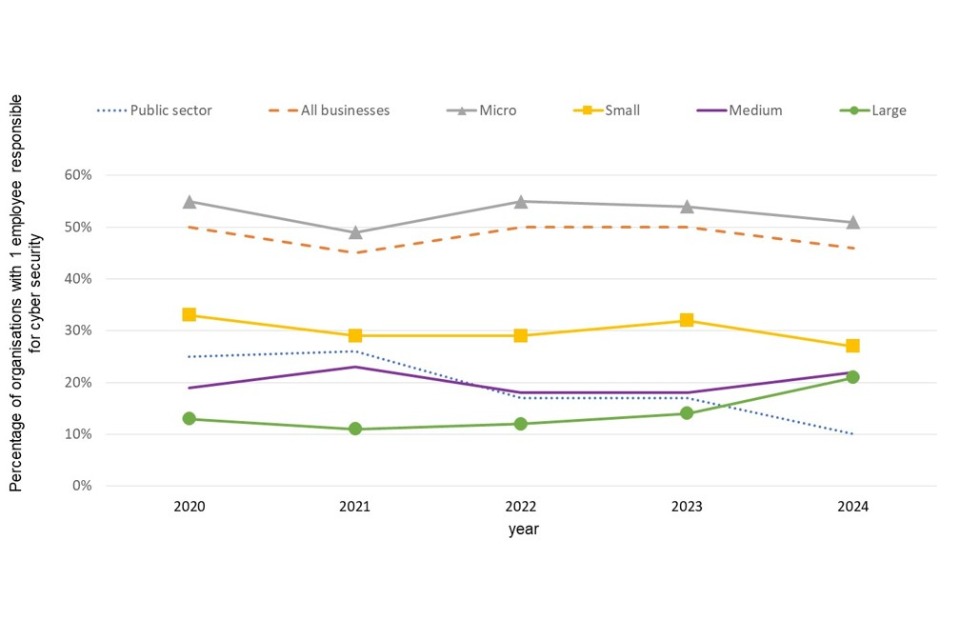
Bases: 130 public sector; 930 businesses; 520 micro; 241 small; 121 medium; 48 large
Among the private sector, those that outsource any aspects of cyber security to an outside organisation, meaning a business’s cyber security could consist of a mix of outsourced and non-outsourced tasks, tend to have cyber teams of more than 1 person. Nearly two thirds (64%) of those that outsource have a cyber team of more than 1 person versus 46% of those who do not outsource.
These figures are in line with last years’ findings in which 58% of those that outsourced had more than 1 person versus 43% who did not outsource. Therefore, an explanation for this could be similar to last year that this is because larger businesses are more likely to outsource cyber security. While 38% of businesses outsource, this increases to 65% among large businesses. This trend was also found last year with 33% of businesses outsourcing increasing to 62% for large organisations.
Cyber teams within the cyber sector
The cyber security sectorial analysis for 2024 found, like last year, most firms within the cyber sector in the UK this year are small (24%) or micro (55%) in size. The percentage of micro firms is unchanged from last year (55%) however, there has been a significant decrease in the proportion of small businesses compared to last year (27%).
The percentage of cyber sector businesses employing cyber teams of certain sizes has remained similar to last year. Only a minority of cyber sector businesses have a cyber team with 30 or more people.
Figure 2.3: Percentage of cyber sector businesses employing cyber teams with the following number of people
2.2. Career pathways into cyber roles
Career pathways into cyber roles outside the cyber sector.
Among businesses outside of the cyber sector, 84% reported that cyber security roles within their organisation had been absorbed into an ongoing non-cyber security related role (Figure 2.4) showing no change from last year.
In the qualitative research, cyber security leads who were not dedicated specialists had typically taken on cyber responsibilities as part of a wider role, for instance, overseeing IT for the business or being Head of IT. Consistent with previous years, they could feel stretched and unable to dedicate enough time to cyber security.
There is too much work for one person. In addition to the technical side of it, we are in a constant cycle of auditing, PSN connection compliance, looking at business continuity across the organisation.
(Public sector organisation, 250-999 employees)
Cyber security leads who were taking on cyber security along with other responsibilities often learned on the job.
I cover a bit of everything in my role. For cyber security, I had not got any experience of that before starting this job. I have only learnt in this job.
(Private sector organisation, 50-249 employees)
Where they had done any training, this was through vendors (e.g. Microsoft) or publicly available resources such as the National Cyber Security Centre’s online training or YouTube videos. As we have found in previous years, cost and time are barriers to training.
So, it’s a lot of online [training] and in some cases the best resource is YouTube because it’s got such a massive user base. There’s a lot of people putting a lot of good information out there. Obviously, you just have to be careful what you’re looking at, it’s best to look at the verified sources.
Organisations were unlikely to recruit someone externally into a cyber specific role who was already working in a cyber security related role (3%). This number is similar to last years’ (4%), and shows organisations are still reluctant to hire external cyber security talent, preferring to include cyber security responsibilities in the roles of current employees.
Figure 2.4: Percentage of those in cyber roles outside the cyber sector who have come in through particular career pathways from 2020-2024
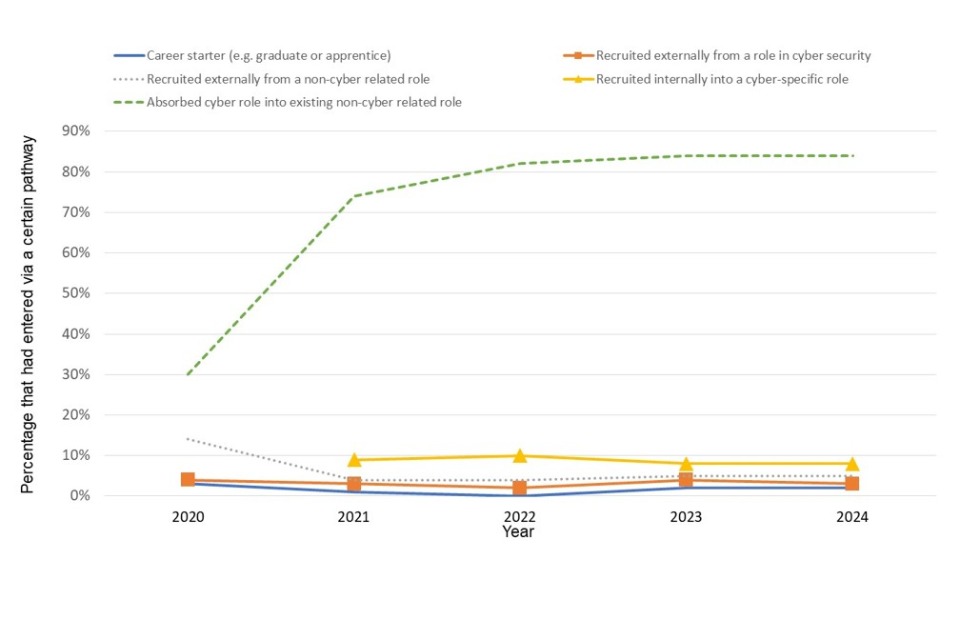
Bases: All businesses; 2024: 1060; 2023: 1108; 2022: 1070; 2021: 1041; 2020: 1152
Are cyber roles labelled as such across organisations?
Among charities, cyber security was mainly covered informally (83%) with only 14% of charities reporting cyber security was a formal part of their a job description, charity income however did affect these figures with fewer charities with an income of £500,000 or more (65%) cover cyber security informally than charities with an income of under £100,000 (89%), while for just under a third of charities with an income of £500,000 cyber security was a formal part of their job role (31%) compared to 8% for charities with an income under £100,000.
As with charities, most businesses covered cyber security informally (90%) but this was less common among public sector organisations with only one in two covering cyber security informally (50%). While large (41%) and medium (28%) businesses were more likely to have cyber security as a formal part of their job description than micro or small organisations (7%).
In the qualitative research, we heard two reasons why cyber security roles are undertaken informally. One is that there is no perceived need for a dedicated cyber security person in the organisation.
Cyber security is part of my job description. They don’t want to or need to go in the direction of employing a cyber security specific person.
(Public sector organisation, 50-249 employees)
The other is that there is a need, but this has yet to be recognised by senior management.
I don’t have a cyber security person in my team. I am picking up that role with the other responsibilities I have in the business. I would love to have a specialised cyber security person in my team. For a company our size, we do need one. That is what I am taking to the board members.
Just under half of those in the cyber sector workforce joined from a previous role in cyber security (48%). This figure has remained close to half since this question was asked in 2020 as shown by Figure 2.5. This year around a third of the cyber workforce had been recruited from non-cyber security related roles (35%), again this is similar to last year (33%).
Less than one in five of those in the cyber workforce had joined as a career starter (17%), this is broadly the same as last year (20%). As was the same in previous years, it is more common for cyber firms to take on those already in the cyber labour force (48%) than career starters (17%).
Figure 2.5: Percentage of cyber sector workforce who have come in through particular career pathways
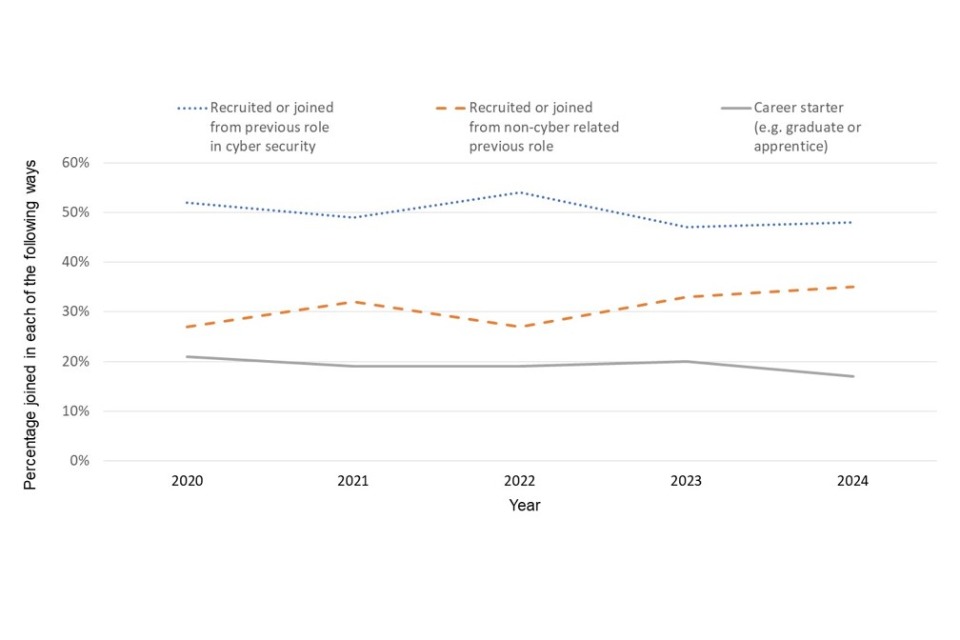
Bases: 171 cyber sector businesses (excluding those that could not break down their workforce)
Are internships or work placements offered in the cyber sector?
Similarly, to the previous year just under a third of cyber firms (30%) had offered any internships or work placements. This figure has remained stable since this question was introduced, with it being 29% last year, 27% in 2021 and 28% in 2020. Like last year, this figure was higher among those that had been trying to recruit over the past year and a half (51%) compared with those who had not (11%).
2.3 Specialisms of those in UK cyber sector firms
Proportion of cyber sector workforce working in particular specialisms.
For the second year this research has included a question to measure the proportion of the workforce who work in the specialism outlined by the UK Cyber Security Council’s Careers Framework. Like last year, there is a high prevalence of Cyber Security Generalist with just over 6 in 10 cyber sector firms having a person in this role (62%). Once again, this year Digital Forensics and Cryptography and Communications Security had the lowest percentage of coverage across the cyber sector.
After Cyber Security Generalist, Cyber Security Governance and Risk Management made up the largest proportion of roles across the cyber workforce (46%), which is a slight change from last year in which Cyber Security Management was the second most common. The proportion of professionals who work in each of the specialisms has remained stable between 2023 and 2024.
Figure 2.6: Percentage of cyber sector workforce who work in each of the 16 specialisms outlined in the UK Cyber Security Council’s Careers Framework comparing 2023 to 2024
Bases: Cyber sector businesses where specialisms were specified; 2024: 144; 2023: 137
This year a question asking which responsibilities are considered to be part of a Cyber Security Generalist role was included. Cyber Security Generalists are often expected to have responsibilities across a range of cyber security areas. For cyber sector firms which said they had a Cyber Security Generalist role, just over eight in ten (83%) thought it was a generalist responsibility to advise IT staff and business managers on cyber security risks and controls including procedures and staff behaviours whereas just over half (51%) thought generalists were responsible to recruit, train and assess others in relation to cyber security.
In the qualitative research, we asked employers and recruiters what they understood by the term ‘generalist.’ A common definition was a single person or small cyber teams who have a wide range of cyber security responsibilities.
It’s a finger in lots of pies, but master of none! I would classify myself as a cyber security generalist.
(Public sector organisation, 1,000 or more employees)
Another common understanding of a generalist was a senior person, such as a chief security officer or consultant, who has to work across the whole field and understands both strategic and operational elements of cyber security. The role of ‘generalist’ was also associated with governance/non-technical roles.
I’d say quite a lot of us who are senior consultants are still generalist. Over my career I’ve looked at lots of different things, lots of different areas.
(Cyber sector firm, 1,000 or more employees)
Qualitative feedback on the UK Cyber Security Council’s Cyber Career Framework
Most employers and recruiters taking part in the qualitative research had not heard of the Cyber Career Framework or the 16 cyber security specialisms. Cyber firm employers were more likely to have some awareness of the Framework.
Employers and recruiters thought there were benefits to using the Cyber Career Framework. Some felt it could be helpful for people thinking about working in the cyber sector or just starting out on their career because it explains what the various roles in cyber security involve.
If I put myself in any of those kids’ shoes, security as a topic to them is security, but what actually is it? That Framework breaks it down into more granular roles and if they read it, it would give them a bit of an understanding to say security engineering does this, you make things work, you talk to the business, stuff like that. It gives them that granularity and tries to bring it to life for them. Because when you’re looking at cyber, you almost don’t know where to start. That gives them that starting point.
(Recruitment agent)
As well as being a valuable resource for new entrants, some thought the Framework could usefully provide a shared understanding between employers and educational providers.
Being able to work using that framework as a collaborative framework between the employer and the college to say, well, let’s try and get as many of this or get all of these aspects in. It’d be great because there’s a common Framework for both of us.
Some non-cyber organisations thought that the Framework would be useful when recruiting for cyber roles, for instance writing job descriptions and providing guidance on questions to ask potential candidates.
I would use this in the interview process when interviewing a generalist person. I would have questions for the candidate around these different roles and responsibilities.
(Private sector organisation, 1,000 or more employees)
Employers saw advantages to using the Framework to help identify gaps for training within their organisation.
If my company was trying to improve its cyber security knowledge for its team, they could use something like this. The staff would be able to support our clients better in terms of asset management or incident management.
However, a few employers felt that neither the Framework nor the 16 specialisms were relevant to their organisation. They believed that it was better suited to larger organisations, or that their organisation did not need to know these skills.
It feels more aimed for a larger businesses, not one our size.
A few employers thought that, in practice, the 16 specialisms overlapped, and were not actually as distinct as the Framework portrays. One commented that the Framework siloes different roles.
My immediate concern is that siloing up something which is already fairly siloed. A lot of the work that we do with clients is trying to help them break down the silos in some of their teams. Anyone that works in security operations should understand vulnerability management, inclusion detection, threat intel, incident response. So, what is the difference between those roles? Is there really value in splitting them out?” (Cyber sector firm, 1,000 or more employees)
Overall, though, employers and recruiters felt positive towards the Framework and some said that it would be beneficial to raise awareness of it.
A broader promotion of that skills Framework, whether that’s through some industry heavy weights or people to promote that out in the industry. Being able to promote that would definitely be a good thing.
2.4 Qualifications of those in UK cyber sector firms
Prevalence of different types of cyber security qualifications
This year 63% of cyber sector firms reported they had any employee working towards a cyber security-related qualification or certified training. This finding is in line with both last year (61%) and the year before that (62%) indicating that levels are relatively stable across recent years.
Figure 2.7 shows the qualifications cyber firms say their staff hold. Like last year, just under half of all cyber firms (46%), whether they had or were working towards a qualification or not, said staff held a technical qualification or certified training. 27% of cyber firms said staff had a specialist higher education qualification almost identical to last year (28%). The number of cyber security apprenticeships (11%) has remained relatively stable compared to last year (18%). We look at apprenticeships in more detail in Sections 6.1 and 9.4.
Figure 2.7: Percentage of cyber sector firms that have staff with the following types of qualifications or accreditations
Bases: All cyber firms: 180; All with or working towards a qualification 114
Figure 2.8: Percentage of cyber sector firms that have staff with the following types of qualifications or accreditations (trend data)
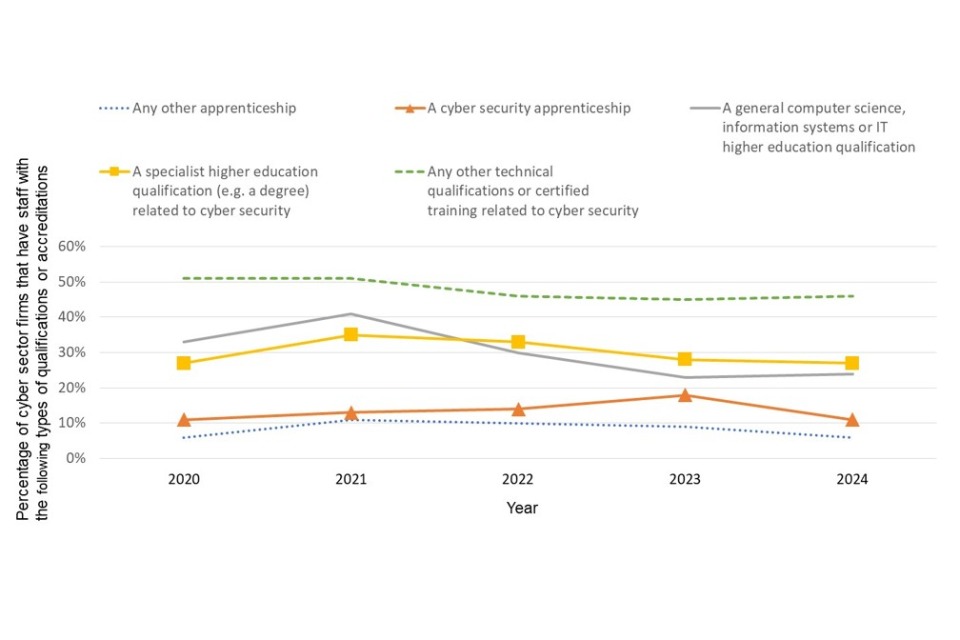
Bases: All cyber firms: 180
Qualitative findings on professional standards and Chartered status for cyber professionals The UK Cyber Security Council has created the first professional standards for cyber security, against which cyber security training and qualifications will eventually be benchmarked. It has also created professional titles (including chartership) for various cyber security specialisms to indicate the level of competence of a professional. Professional titles are now available in Governance and Risk Management, Secure System Architecture and Design and Audit and Assurance through CIISec and Security Testing through The Cyber Scheme. Over 100 practitioners now hold professional titles. Titles for further specialisms will be released in due course.
As with the Cyber Career Framework, most were not aware of this route to the chartership, although employers from cyber firms were more likely to have heard of this.
Attitudes towards professional standards and the idea of chartership were mostly positive. Some felt this would provide standardisation to the cyber sector as is already the case for other professions.
There are professional standards for other roles, like accountants and surveyors for example. This will actually give employers the knowledge that they are dealing with qualified professionals, who have certain skill sets.
Similarly, some felt that chartership would bring credibility to the profession. It demonstrated to employers, as well as clients, that these individuals were well-qualified to undertake certain roles.
That would be very useful when recruiting to have these professional standards that people have to reach, and I presume they have to requalify regularly. You are not just taking their word for it, you have professional standards to go by.
Some had practical questions; how long chartership would take, how much it would cost, how requalification would work and how applicants would be assessed. A few were concerned that chartership would focus on academic ability at the expense of practical experience. Some wondered how chartership would fit with existing standards and accreditations.
Maybe over time I can see these coming into play, but there are already standards there, like you have your CREST certifications, ISC2. It’s understanding how these standards will fit into these. How do they correspond?
Some employers expressed a wait and see attitude, saying that they would only consider chartership if it became widely recognised by the industry or was requested by clients.
We may start using, provided customers were asking for it. 50% of our business is public sector and 50% is commercial, so it will be led by what industry wants.
Furthermore a few questioned whether chartership would be dynamic enough to account for the rapid changes seen in the cyber sector in comparison with other professions. The need to keep up to date was also raised in relation to the Cyber Career Framework.
Things we did 2 years ago are out of date already. You need to be dynamically chartered in cyber to understand everything that is coming down the line.” (Cyber sector firm, 1-9 employees)
3. Diversity in cyber security
This chapter explores diversity within the cyber workforce, focusing specifically on gender, ethnicity, disability, and neurodiversity [footnote 2] . It includes diversity estimates from the quantitative survey and qualitative findings.
As in previous years, survey questions on diversity are asked of cyber sector firms rather than the wider business population. As cyber firms are the primary recruiters and employers of cyber related positions and because most businesses carry out cyber roles informally, including businesses would give an inaccurate view of diversity in the cyber security workforce. The qualitative findings do include the perspectives of non-cyber organisations and recruitment agents.
3.1 Estimates of diversity in the cyber sector
All workforce statistics.
It is important to bear in mind that the data from this study are workforce level estimates derived from employer survey data. As with previous years, because these estimates can be very variable we checked for outliers but no outliers were identified this year.
As can be seen from Figure 3.1, the proportion of women in the cyber workforce is 17%, which is lower than both the UK workforce as a whole and the digital workforce (although the gap is less marked). 15% of the cyber workforce are from ethnic minority backgrounds, which is in line with the UK workforce overall. In contrast, 6% are disabled [footnote 3] , which is lower than both the digital and the UK workforce, the same pattern seen in previous years. [footnote 4] 13% of the cyber workforce are neurodivergent. There are no reliable statistics to compare this figure to other sectors.
Figure 3.1: Percentage of cyber sector workforce that come under the following diverse group
Base: c140 cyber sector business for all workforce estimates (in each case excluding those that were not able to answer these questions, or refused)
The overall pattern is that there is a lower proportion of these demographics in senior roles compared to the cyber workforce overall. [footnote 5]
As Figure 3.2 illustrates, diversity in the cyber sector overall has remained stable compared to previous years. The female, ethnic minority, disabled, and neurodivergent proportion of the workforce has remained broadly consistent over the past five years. The start of an upward trend in 2022 for those from ethnic minority backgrounds and women has not been sustained and there are now signs of a downward trend for ethnic minorities. The share of neurodivergent workers is trending upwards over time.
Figure 3.2: Percentage of cyber sector workforce that come under the following diverse group (All cyber workforce trend data)
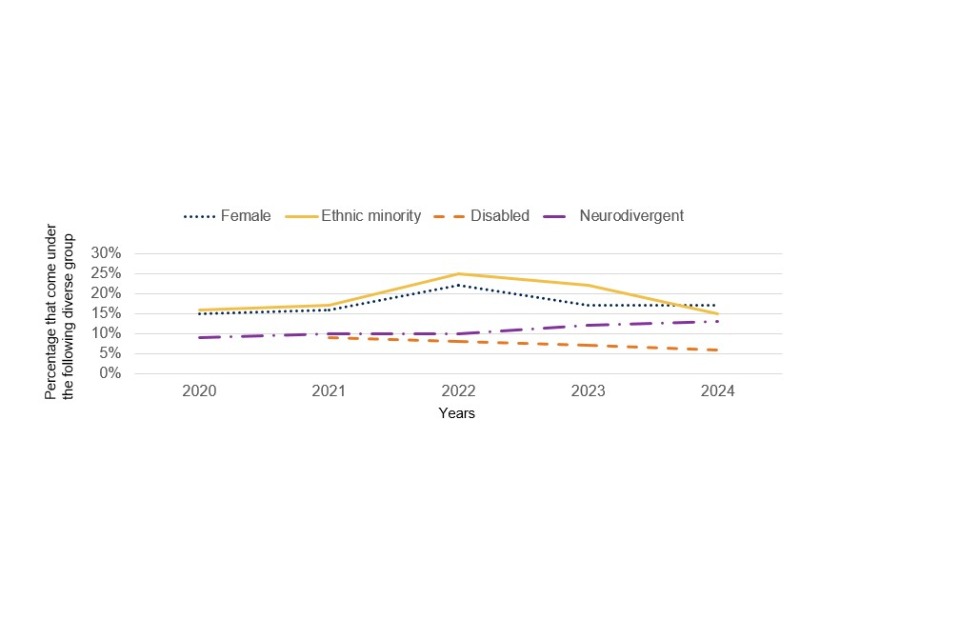
Base: c. 140-220 cyber sector businesses for all workforce estimates (in each case excluding those that were not able to answer these questions or refused)
Senior workforce statistics
Senior cyber professionals are defined as those who have 6 or more years of experience. The latest study found no significant change in the level of diversity at a senior level in the past year. As can be seen in Figure 3.3, the proportion of disabled people in senior cyber roles has been consistently low over time. The proportion of women in senior cyber roles has been steady following a drop between 2021 and 2022.
Figure 3.3: Percentage of cyber sector workforce that come under the following diverse group (Senior cyber workforce trend data)
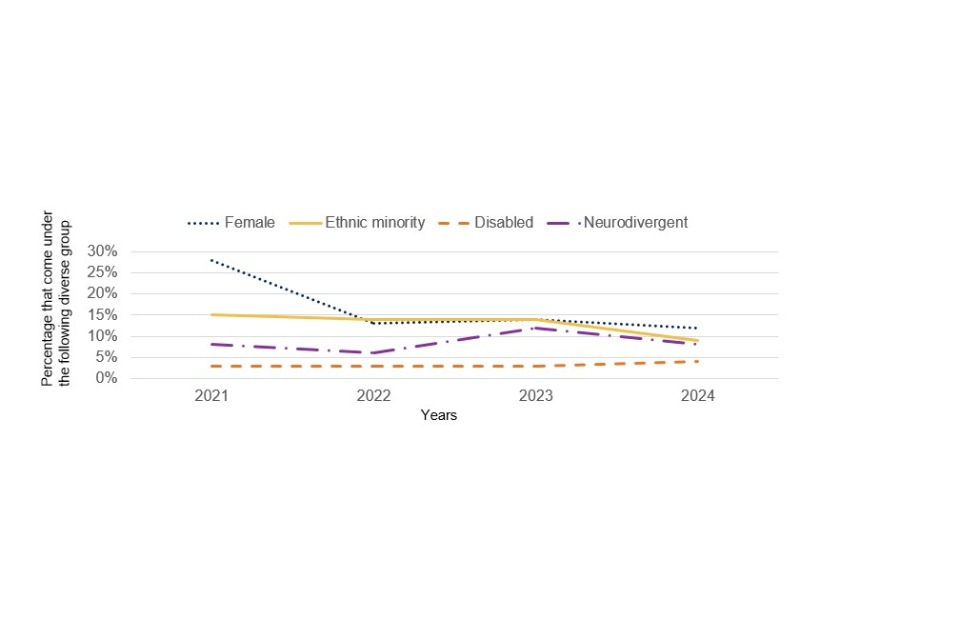
3.2 Attitudes towards workforce diversity
In the qualitative research, employers defined diversity in a variety of ways, including diversity in gender, ethnicity, disability, neurodivergence, sexuality, social class, religion, nationality and age. As we have found in previous years, employers did not perceive the cyber sector as very diverse, especially in terms of female representation and ethnicity, which tended to be the most common ways in which employers thought about diversity.
As an industry, it’s unnecessarily dominated by white men. It’s always important to make sure you’re giving [women and ethnic minorities] the opportunity to come in.
A related point is that perceptions of the industry can be shaped by the stereotype of white males in dark rooms.
There are insufficient role models in the industry. If you think in the cyber world, it is very white male-orientated, mid 20s, early 30s, drinking Red Bull in front of a screen. That is the stereotype.
(Cyber sector firm, 1-9 employees)
While employers saw lack of diversity in the cyber sector as an issue, some believed that the landscape is changing for the better.
It’s not very diverse but it is trying. The one that is most noticeable is around gender diversity.
This was echoed by recruiters, who said that employers are increasingly asking for diverse candidates. This is partly because diverse teams are valued for performing better.
I think it’s a really key thing. I think everyone recognises now that diverse teams are very much more high performing teams.
Some employers said that diverse teams are particularly important for cyber security because of the need to solve problems and continually counter threats.
Cyber security is very much about problem solving. When you drop a problem in a team of people, what you hope is that every single one of them will think of a different way of solving it. That’s the first part. The second part is that everybody feels comfortable enough to share.
(Cyber sector firm, 10-49 employees)
A broader factor is the desire to have a diverse workforce. One recruitment agent thought that this is particularly an issue for leadership roles.
For leadership roles, absolutely. If you’re a publicly traded company, there’s that pressure there to have diverse leadership. But even architecture or engineering roles, there’s definitely that pressure there to try and produce diverse short lists. We’re probably going to get our knuckles wrapped if, for instance, we sent a shortlist of, say, four or five people and they were all white males.
However, some cyber employers felt that although they were able to recruit diverse candidates for entry level and more junior roles, diversity at senior levels is a particular challenge. One way of countering this is having leadership and mentoring programmes for diverse employees.
We are broadly at parity in gender in our early years, recruitment in graduate and [their apprentice scheme]. We have a good ethnic diverse mix in those grades. As you get more senior, that tends to whiten out, and the number of men, or proportion of men, increases.
This is one example of the variety of inclusive practices which some cyber firms have in the workplace. Others are flexible working, internal forums, recognition awards for women in cyber, making adjustments for people with disabilities, and being mindful of religious festivals such as Eid. Some public and private sector organisations have similar diversity initiatives, but these are company-wide rather than specifically relating to the cyber workforce.
3.3 Diversity in recruitment processes
Just under half (47%) of cyber firms have tried to recruit individuals into cyber roles since January 2022. [footnote 6] Amongst these firms, 42% have taken some action to encourage applications from diverse applicants which is consistent with 2023 (40%). This means they have targeted at least one of these diverse backgrounds. 14% have taken action to encourage applicants from all the diverse backgrounds asked about in this study (women, people from ethnic minority backgrounds, disabled people, and neurodivergent people). This is also similar to 2023 (18%).
As can be seen in Figure 3.4, and similar to last year, cyber firms are most likely to focus their efforts to recruit women. As we have discussed, in the qualitative strand employers commonly associated diversity with a lack of female representation, which helps explain why recruitment efforts are more likely to be directed at this group. The proportion of cyber firms who have made changes to recruit from ethnic minority backgrounds and neurodiverse backgrounds has not significantly changed.
Figure 3.4: Percentage of cyber firms who have tried to recruit over the last 18 months and have made changes to recruit across the following groups
Base: 84 cyber sector firms who tried to recruit since the start of 2022
In a new question this year, we asked cyber firms about recent, specific steps taken to boost applications from diverse groups, focusing on those who adjusted recruitment for diversity. Although the base size (35 firms) is low, and therefore should be treated with caution, responses give a sense of the most commonly used strategies:
- 43% hired through non-degree routes
- 43% attended networking events/conferences and career programmes for diverse groups
- 40% took action to diversify the senior leadership team
- 40% worked with recruitment agencies to find more diverse candidates
- 37% ran talks or events in education settings
- 29% worked with third sector organisations to help identify and support more diverse groups
- 20% have hired through a scheme to promote diversity
- 20% set diversity metrics/quotas for recruitment In the qualitative interviews, employers mentioned having more inclusive job specifications, increasing diversity through entry level recruitment, using blind recruitment, setting quotas, using referral schemes, and recruiting from other countries.
We sketch our requirements. [Internal recruitment team] make sure that we are not using any offensive or challenging words or phrases. They word it in a considerate way to get a much broader response.
Recruitment agents said they use their networks to find diverse candidates and also work with organisations to ensure their job specifications are flexible and attractive. In terms of employer requests, some were informally asking for more diverse recruits, while others set specific quotas, particularly on the basis of gender. One recruiter said some organisations gave them incentives to find candidates with disabilities.
It can come down to education with the client as well. Being open and flexible on locations and working patterns and things like that. You flex on those things and therefore you can attract more diverse candidates.
In line with the qualitative findings from previous years, employers and recruiters felt that a lack of diversity in the talent pool is a major barrier to recruiting individuals from diverse backgrounds. Some employers felt that this is particularly an issue in their local region because it is not ethnically diverse.
I don’t think there is enough women in the industry to recruit from. Which is a challenge. There is still not enough women choosing it as a career option and I have been in this industry since the mid-80s.
As we have also found in previous years, some employers did not have any strategies in place beyond not excluding anyone on the basis of their background. For some, attracting more diverse candidates is simply not on their radar. Others said that they do not have the expertise or resources to do so.
We just recruit from whoever applied. It is not something that is not on the radar or off the radar. It just would not be a thing. We just go from the pool of applicants. No sort of discrimination.
We don’t positively discriminate, we just look for the best person who can do the job. We are not a large employer like the civil service, who employ thousands of people and can look at diversifying strategies. We just look for the best person for job.” (Private sector organisation, 1,000 or more employees)
4. Current skills and skills gaps
This chapter explores the cyber security skills that organisations feel they need and the extent of current skills gaps. Cyber security skills gaps exist when individuals working in or applying for cyber roles lack particular skills necessary for those roles. This is different from skills shortages, which are a shortfall in the number of skilled individuals working in or applying for cyber roles. We cover skills shortages with regards to recruitment in Chapter 6.
4.1 Technical skills gaps outside the sector
Basic technical skill gaps.
Each year, the survey asks cyber security leads within organisations to rate how confident they are in carrying out a range of basic cyber security tasks and functions. These functions comprise the technical areas covered under the Cyber Essentials scheme as well as other basic aspects of cyber security. Some tasks have been added since the launch of the initial survey.
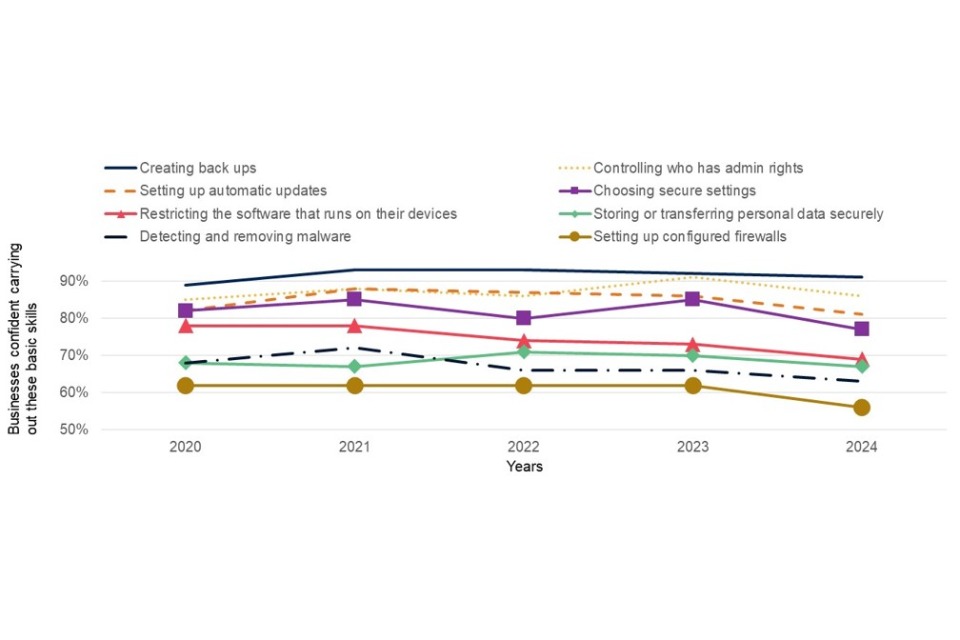
Figure 4.1 illustrates that confidence in carrying out these tasks has remained relatively consistent across all five years of the study, although this year has seen more significant declines than previously noted in some areas.
Figure 4.1: Extent to which businesses are very confident or fairly confident carrying out each of these basic skills gaps across all 4 years of the study (Base is where such tasks are not outsourced except for setting up new accounts and authentications)
Bases: c.600+ businesses that do not outsource each task
Figure 4.1, which focuses just on those businesses that conduct these functions in house, reveals that the areas of most prevalent skills gaps continue to be around the setting up and configuration of firewalls, detecting and removing malware and the secure storage and transfer of personal data. Even here, however, only a minority of cyber security leads across the business population – no more than one in five for any measure – say they are not confident in their business’s ability to carry out these tasks. Although the pattern broadly follows those of 2023, confidence in choosing secure settings and controlling who has admin rights has significantly decreased in comparison.
Figure 4.2: Extent to which businesses are confident in performing basic cyber security tasks (Base is where such tasks are not outsourced except for setting up new accounts and authentications
Bases: c.600+ businesses that do not outsource each task. Unlabelled bars are under 5%
In order to provide a more complete picture of the state of skills gaps in the total business population, Figure 4.3 also includes businesses that outsource cyber security, and separates organisations into different categories – businesses as a whole, large businesses (with 250 or more employees), charities and public sector organisations.
The results in figure 4.3 continue to show that a large minority of organisations lack confidence in several of the basic skills areas, and that basic cyber security advice and guidance is still needed for businesses outside the cyber sector. The most common area where organisations lacked confidence was a new code included in the survey for this year, a third of businesses and charities reported that they were not confident in dealing with cyber security breaches (33% of businesses and 34% of charities).
There are some changes this year when comparing the percentage of organisations not confident in certain basic tasks to the results in the 2023 study. Businesses this year were less confident in restricting software (22% vs 18%), choosing secure settings (15% vs 10%), setting automatic updates (13% vs 10%) and controlling who has admin rights (9% vs 6%). Meanwhile figures for large businesses remained mosltly consistent with last year, however more large businesses this year were not confident in setting up configured firewalls (13% vs 2%). There were no changes for charities and the public sector between this and last year.
Figure 4.3: Percentage not confident in performing basic cyber security tasks, by type of organisation
Bases: 930 businesses; 46 large businesses (with 250+ staff); 190 charities; 130 public sector organisations. N.B. these figures are rebased on the full survey samples, but the questions are only asked of a subsample. The subsamples are small for large businesses, charities, and public sector organisations (c.46+).
A combined basic technical skills gap indicator
We can use these findings to estimate the proportion of businesses with a basic cyber security skills gap. We do this by combining all 10 tasks listed in Figures 4.1 and 4.2 and identifying the percentage of organisations that are not confident in undertaking at least one of these basic functions. This gives us an overall figure of 44% of businesses that can be said to have a basic technical skills gap. Once again, this is lower among public sector organisations (24%) and large businesses (26%) and higher among charities (51%).
The survey is designed to be representative of the UK business population. This means that we can extrapolate from our finding that 44% of businesses have a basic technical cyber skills gap and estimate that approximately 637,000 UK businesses have such a gap. [footnote 7] This is a significant fall from the 2023 survey, when 50% were estimated to have a basic technical cyber skills gap.
Figure 4.4: Basic skills gaps trend data
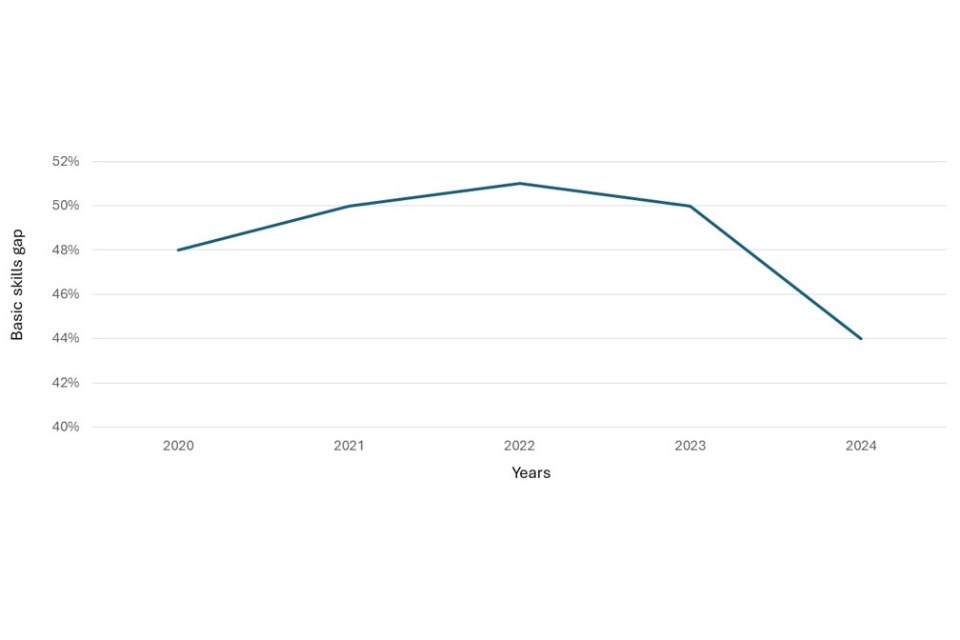
Bases: 930 businesses
Beyond these foundational cyber security skills required for basic cyber hygiene, some organisations may judge that they also require more advanced technical skills to stay cyber safe. This may be because of the sector in which they operate, their clients, supply chain or partner relationships, among other factors.
The definition of advanced technical skills used here was based on data obtained from the 2018 cyber security labour market study. These are skills that may be important for organisations with more complex cyber security needs, and includes skills such as penetration testing, forensic analysis, interpreting malicious or user activity monitoring tools.
Organisations rated how important it was that their in-house cyber security teams had these skills, giving each one a score from 0 (meaning they felt it was not at all important) to 10 (meaning it was essential). As in previous years, the findings reveal that large businesses and public sector organisations are more likely to consider these skills as critical in their environment.
Observing the trend since 2020, it is noticeable that large businesses, charities and the public sector are all now much more likely to consider these skills as essential. This is particularly true in the public sector, where the proportion considering them essential has risen from fewer than one in ten (9%) in 2020 to over one in five (21%). This is one potential indicator of the increased sophistication of the cyber threat.
Figure 4.5: Perceived importance of advanced cyber security skills for those working in cyber security roles outside the cyber sector
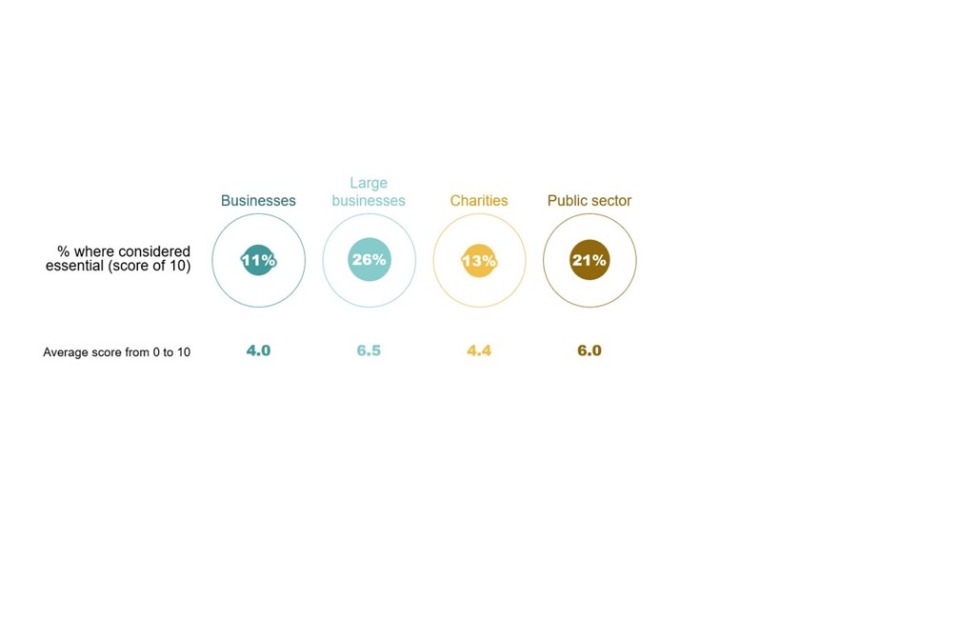
Bases: 1060 businesses; 48 large businesses (with 250+ staff); 190 charities; 130 public sector organisations
Figure 4.6: Perceived importance of advanced cyber security skills for those working in cyber security roles outside the cyber sector (trend data)
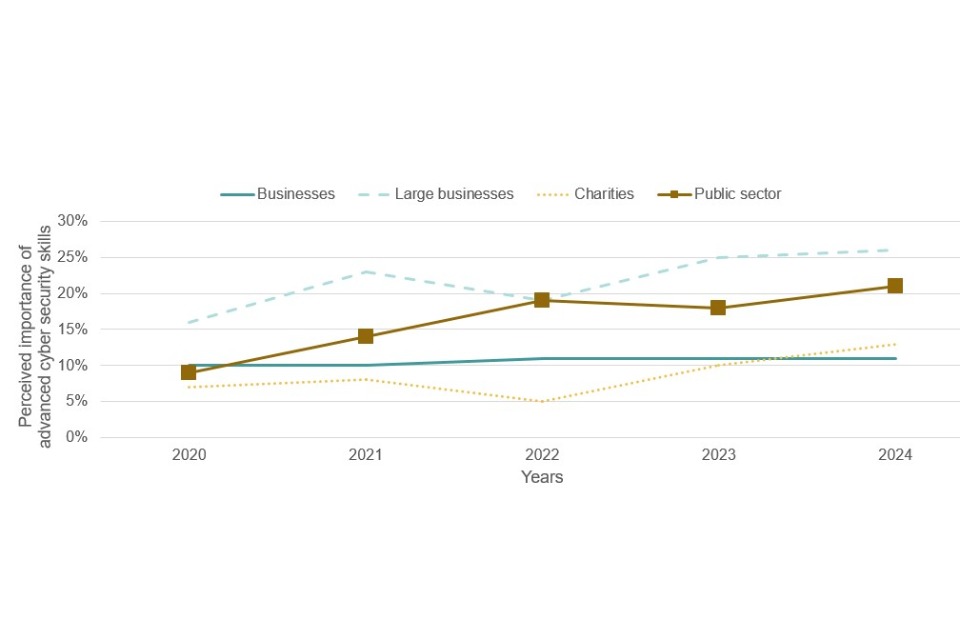
Advanced technical skills gaps
The survey also measures businesses’ level of confidence in these advanced technical skills.
Figure 4.5 focuses on the views of businesses who judge this set of skills to be important for their organisation, and who do not outsource them but would attempt to resource them in-house if needed. These findings suggest that little has changed since 2023. Similar to 2023 there continues to be four areas where a majority of these businesses do not feel confident: forensic analysis of breaches (59%), penetration testing (55%), interpreting malicious code (53%) and security architecture or engineering (53%).
Figure 4.7: Extent to which businesses are confident in performing advanced cyber security tasks (where such tasks are identified as important for the business and not outsourced)
Bases: c.350+ businesses that do not outsource each task
Once again, we can look at the views of a broader spectrum of businesses, including those who either outsource these tasks or who do not consider them to be important for their organisation, as well as charities and public sector organisations.
In interpreting these findings, it should be noted that these are self-identified skills gaps, where the cyber security lead in an organisation admits to not feeling confident. Additionally, in calculating the prevalence of advanced skills gaps, we have assumed that those who outsource these elements of cyber security to an external provider, or who do not consider them as important for their organisation, do not have a skills gap.
The results of this analysis reveal a somewhat greater disparity between different types of organisations in the prevalence of these gaps in advanced skills, although the major gaps are the same across all organisation types – interpreting malicious code, forensic breach analysis and penetration testing. Across all these tasks, the relatively small number of charities in the sample are noticeably more likely to report a skills gap.
Figure 4.8: Percentage not confident in performing advanced cyber security tasks, by type of organisation (Base out of all organisations)
Bases: 1060 businesses; 190 charities; 130 public sector organisations.
N.B. These figures are rebased on the full survey samples, but the questions are only asked to a sub-sample of those who don’t outsource these tasks. The subsamples are very small for public sector organisations.
The percentage of charities confident in performing certain advanced tasks are mostly consistent between this and last year, however there is an increase in the number charities reporting they were not confident in carrying out vulnerability scans compared to last year (25% in 2024 vs 15% in 2023). Public sector results are also mostly consistent between 2023 and 2024, although there is a decrease in the percentage of public sector organisations who were not confident in interpreting malicious code (14% in 2024 vs. 25% in 2023). There are however more differences between results form this and last years survey for private sector organisations explored in the section below.
Extrapolating advanced technical skills gaps across the business population
This analysis of the full sample of private sector firms allows us to extrapolate to the wider population of UK businesses and to estimate the size of the skills gaps in each of these areas:
- Around 289,000 (20%) have a skills gap in forensic analysis (vs 26% last year) – a significant decrease
- Around 289,000 (20%) have a skills gap in penetration testing (vs 26% last year) – a significant decrease
- Around 260,000 (18%) have a skills gap in interpreting malicious code (vs 25% last year) – a significant decrease
- Around 260,000 (18%) have a skills gap in security architecture (vs 24% last year) – a significant decrease
- Around 231,000 (16%) have a skills gap in threat intelligence (vs 19% last year) – consistent with the previous year
- Around 202,000 (14%) have a skills gap in vulnerability scans (vs 18% last year) – a significant decrease
- Around 173,000 (12%) have a skills gap in monitoring user activity (vs 13% last year) – consistent with the previous year
A combined technical skills gap indicator
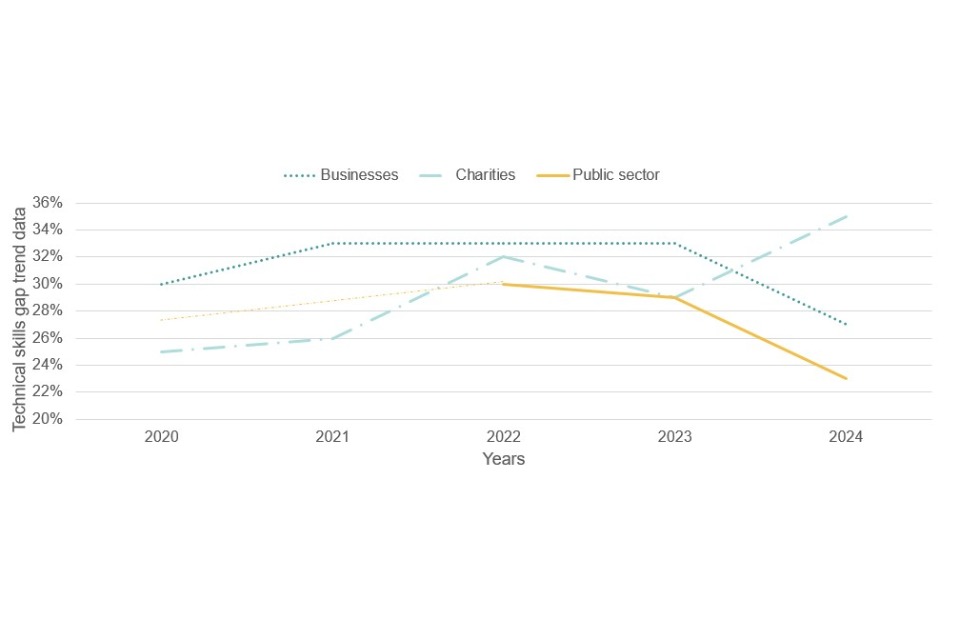
Following the same process as the basic cyber security skills gap calculation, we have merged the 7 advanced cyber security tasks referenced in Figures 4.7 and 4.8, to calculate the percentage of organisations that are not confident in carrying out at least 1 of these tasks.
27% of businesses have an advanced technical skills gap which equates to approximately 390,000 UK businesses. 35% of charities and 23% of public sector organisations also have an advanced skills gap. These results are somewhat lower than those recorded in last year’s study for businesses and public sector.
Figure 4.9: Technical skills gaps trend data
4.2 Technical skills gaps within the cyber sector
As in previous years, a survey of businesses in the cyber sector was carried out to identify areas where there might be gaps in technical skills. Once again, we found that only a minority of cyber sector employees report that their existing employees lack technical skills - 26% report that this is the case, compared to 22% in 2023. The impact of this on the ability of cyber firms to meet their business goals appears modest. 24% report that employees lacking technical skills affected their ability to meet business goals to some extent.
However, technical skills gaps among job applicants for jobs in the cyber sector are perceived to be much more prevalent – 47% report that applicants they have seen lack technical skills. This perceived skills gap – and the difficulty it presents in filling vacancies within cyber businesses – has a greater impact on their business goals. 19% report that candidates lacking technical skills affected their ability to meet their business goals to a great extent, and 28% reported that it impacted their business goals to some extent.
Over time, the size of this technical skills gap appears to have declined. In 2020, 32% of cyber businesses, looking back over the previous 12 months, reported that their employees lacked technical skills, and 59% had observed a technical skills gap among applicants.
Combining these two measures, we can estimate that 30% of cyber firms in 2024 have faced a problem with a technical skills gap (compared to 49% in 2023).
Figure 4.10 illustrates which specific types of skillsets are seen to be lacking. These are drawn from the Chartered Institute of Information Security (CIISec) Skills Framework .
While there remains a substantial overall shortfall across many different skillsets, there has been a significant decline in reported skills gaps across many areas – particularly security testing (23%, down from 35%), cyber security governance and risk management (21%, down from 31%), network monitoring and intrusion detection (16%, down from 27%) and cyber security audit and assurance (18%, down from 28%). In only one areas has there been a comparable increase in reported skills gaps since 2023 – in cryptography and communication security (24%, up from 12%).
Figure 4.10: Percentage of cyber firms that have skills gaps in the following technical areas, among those that have identified any skills gaps
Bases: 128 cyber sector businesses identifying skills gaps
4.3 Incident response skills
Perceived importance of incident response skills outside the cyber sector.
The ability to respond to cyber incidents in-house as needed is a critical part of organisations’ cyber preparedness. We have once again asked organisations to evaluate how important incident response skills are to their business, on a scale of 0 (meaning it is not at all important) to 10 (meaning it is essential). As Figure 4.11 shows, 20% of businesses regard these skills as essential. This represents a significant decrease from 2023, when 24% of businesses regarded in-house incident response skills as essential.
Large businesses (44%) and public sector organisations (39%) are more likely to feel that these skills are essential.
Figure 4.11: Perceived importance of incident response skills for those working in cyber security roles outside the cyber sector
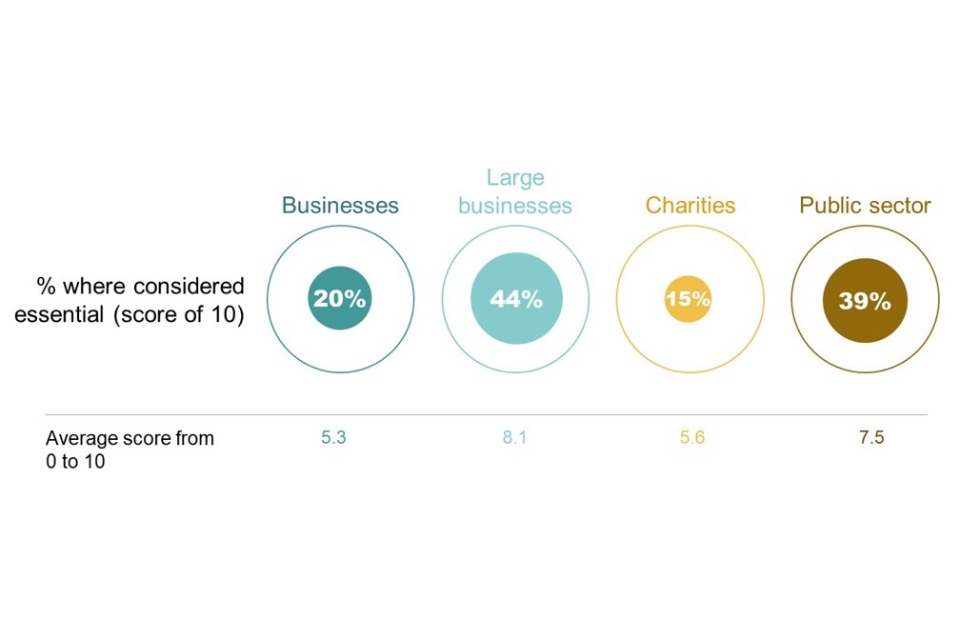
Bases: 930 businesses; 48 large businesses (with 250+ staff); 190 charities; 130 public sector organisations
A significant proportion of businesses (38%) choose to outsource some element of their cyber security. Among those who do, incident response is an area that is very often selected to be outsourced – more than four in five (82%) of businesses do so.
Incident response skills gap
Whether or not it is outsourced, the ability to respond to an incident continues to be a major concern for organisations. As in previous years, we again find that a large proportion of businesses lack confidence in their staff’s ability to deal with an incident if it occurs. Indeed, among businesses who do not outsource incident response, this year nearly half (48%) say they are not confident in their incident response capacity, up significantly from 41% in 2023.
However, there is a growing disparity between the assessment of businesses as a whole and those of public sector organisations and larger businesses with 250+ staff. Despite widespread concern among businesses as a whole, only a small and shrinking minority of public sector bodies (8%, down from 13% in 2023) and large businesses (3%, down from 7% in 2023) now say they are not confident in their incident response capacity.
Figure 4.12: Percentage not confident in carrying out activities related to incident response
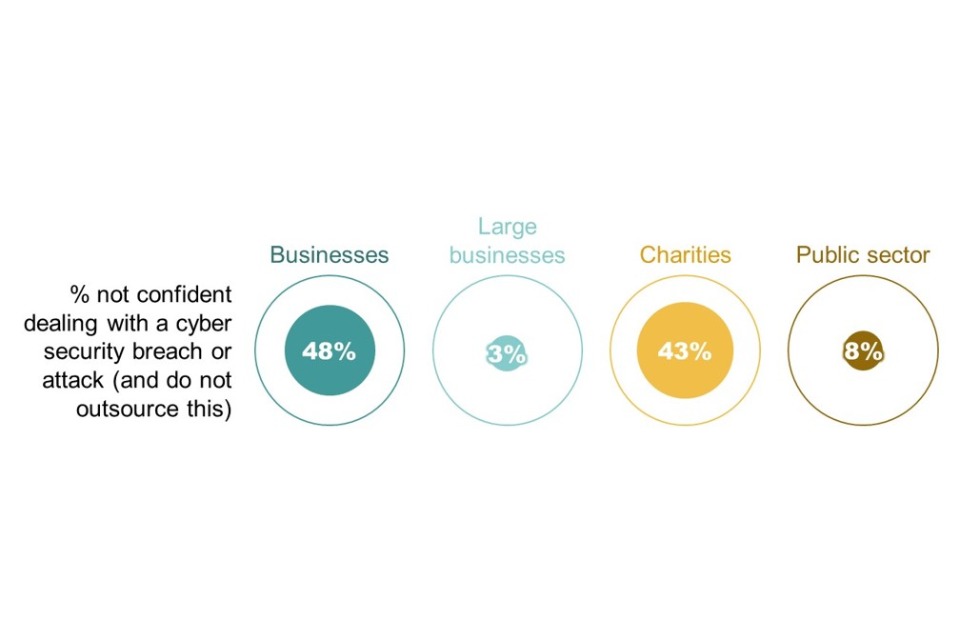
Bases: 591 businesses; 25 large businesses (with 250+ staff); 131 charities; 55 public sector organisations.
N.B. these figures are rebased on the full survey samples, but the question is only asked of a subsample. The subsamples are very small for large businesses and public sector organisations (c.25+).
Figure 4.13: Percentage not confident in carrying out activities related to incident response
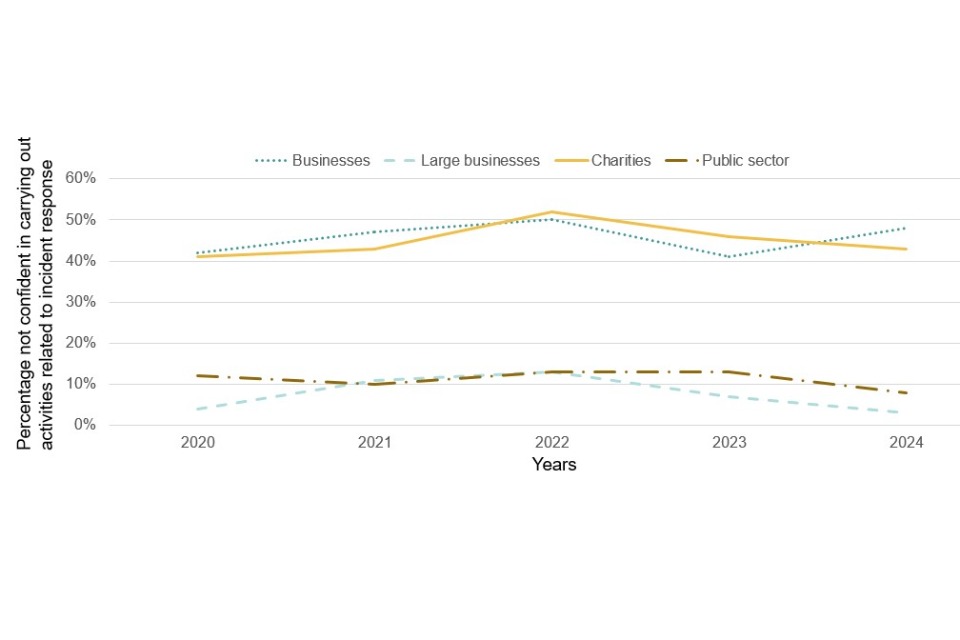
This lack of confidence in incident response among many businesses is illustrated by the concern that many of them feel about devising an incident response plan. Only 43% say they would feel confident in devising such a plan, compared to 52% who would not feel confident. The proportion who lack confidence here is similar to what we saw in 2023 (46%). Many charities feel the same way (46% confident, 47% not confident). Again, confidence in devising an incident response plan is highest among large businesses (88%) and public sector organisations (70%).
4.4 Complementary skills
The perceived importance of complementary or soft skills in the cyber sector.
Cyber sector businesses mostly appreciate the importance of complementary or ‘soft’ skills. They were again asked to rate the importance of those in cyber roles having these skills, using a scale from 0 (not at all important) to 10 (essential).
At 8.2, their average rating of the importance of these skills is similar to that given in the last three years, with 28% rating these skills as essential (10 out of 10). This level was higher, but not significantly so, in 2023 (32%).
Do cyber sector firms identify a complementary skills gap?
Once again this year, DSIT ’s Cyber Security Sectoral Analysis study, conducted using a comparable methodology to the larger survey of non-cyber organisations, provides quantitative data on cyber firms’ perceptions of gaps in complementary skills.
Despite the high level of importance they attach to soft skills, many report that their businesses are lacking in this area. Just over one in three (34%) report that their firms have a complementary skills gap, consistent with 2023 (43%) Only 4% of cyber firms say this has impacted their ability to meet their business goals to a great extent. As we discuss in Section 6.2, candidates with both complementary and technical skills are in particular demand among employers.
The survey results show that cyber sector businesses are, by and large, aware of the importance of complementary skills (sometimes referred to as soft skills). We asked these firms to rate how important it is for those in cyber roles to have complementary skills, where a score of 0 means not at all important, and 10 means it is essential. The average result, similar to the 2020, 2021 and 2022 scores, is 8.2 out of 10. Almost one in four (28%) give the top answer of 10.
Ability of cyber leads outside the cyber sector to undertake tasks requiring complementary skills
The survey also examines the confidence that cyber leads have in carrying out specific tasks required to develop and embed good cyber security practice within organisations – preparing training materials and communicating cyber security risks to senior internal stakeholders.
Figure 4.14 shows the proportion of organisations where cyber leads reported that they had a skills gap in these areas. Once again, organisations that feel confident in these areas are in the minority – indeed, the proportion of businesses reporting a lack of confidence here has risen over time if we compare 2020 with 2023. However, cyber leads in public sector bodies continue to be markedly more confident in doing so than their private and charity sector peers.
Figure 4.14: Percentage not confident in carrying out a range of tasks that require a mix of technical and complimentary skills
Bases: (asked to a random half of full sample): c.465 businesses; c.97 charities; c.74 public sector organisations.
Figure 4.15: Percentage not confident in preparing training materials or sessions
Figure 4.16: Percentage not confident in communicating cyber security risks to directors, trustees or senior management
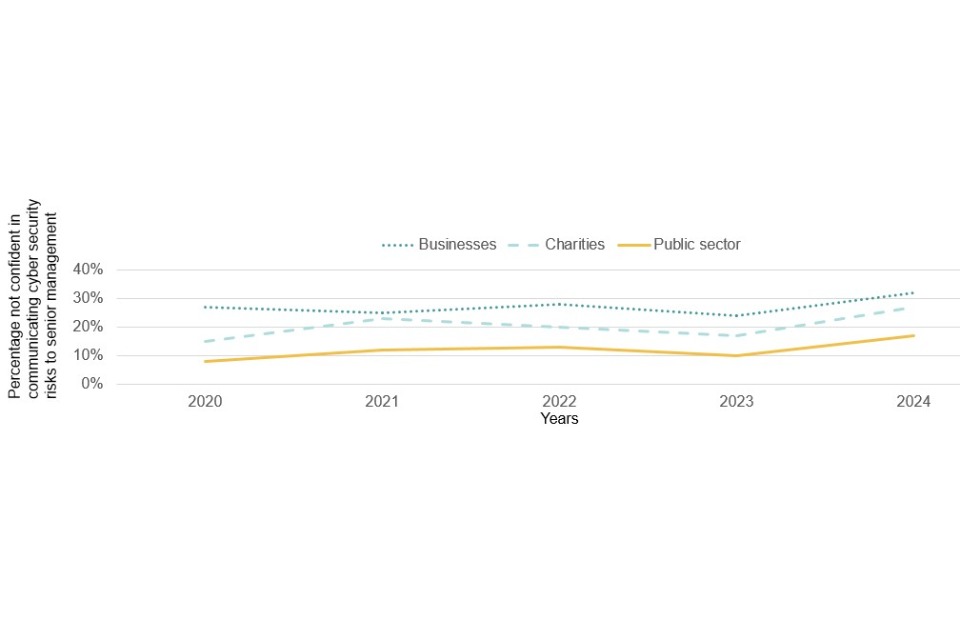
4.5 Governance and compliance skills
Self-identified gaps in carrying out cyber security governance tasks.
Governance tasks are another area where a large proportion of cyber leads continue to report skills gaps. Figure 4.17 shows that nearly half (48%) of cyber leads within businesses say they are not confident in their ability to undertake a cyber security risk assessment, with the same proportion lacking confidence in developing cyber security policies and 42% writing or helping to develop a business continuity plan.
In previous years, charities reported similar levels of skills gaps on governance and compliance as businesses. However, in comparison to 2023, there has been a drop in charities lacking confidence in all three areas.
The contrast with firms in the cyber sector continues to be stark – almost none lack confidence in these areas.
Figure 4.17: Percentage not confident in carrying out a range of cyber security governance tasks
Bases: (asked to a random half of full sample): c.465 businesses; c.93 charities; c.56 public sector organisations.
Figure 4.18: Percentage not confident in carrying out a cyber security risk assessment
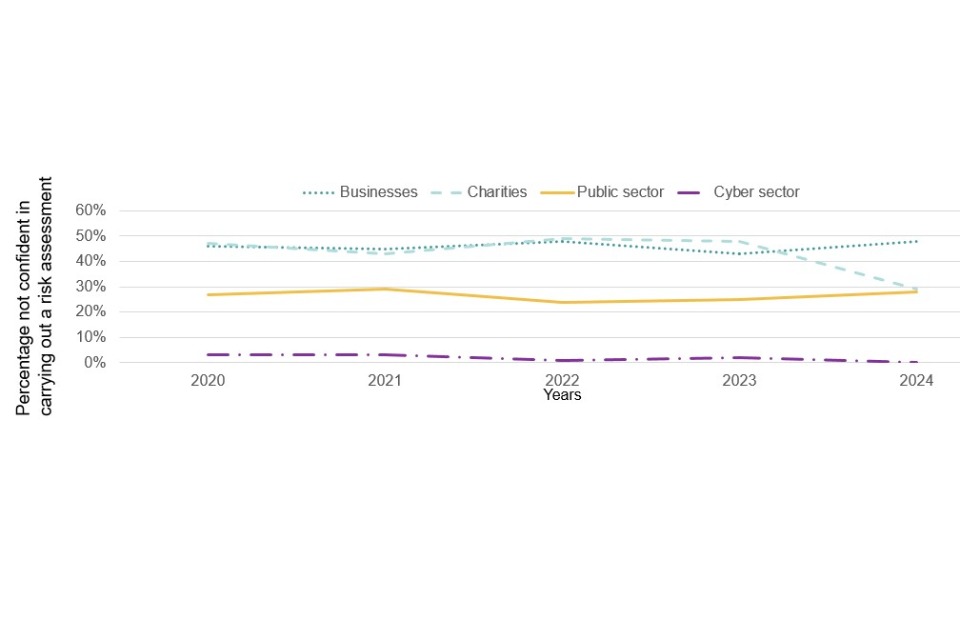
Figure 4.19: Percentage not confident in developing cyber security policies
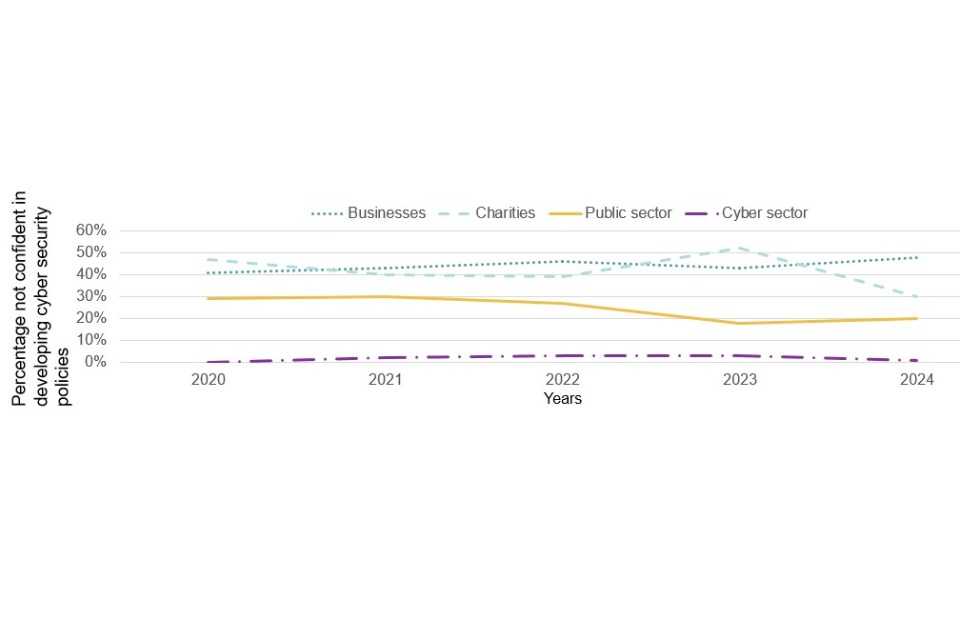
Figure 4.20: Percentage not confident in writing or contributing to a business continuity plan
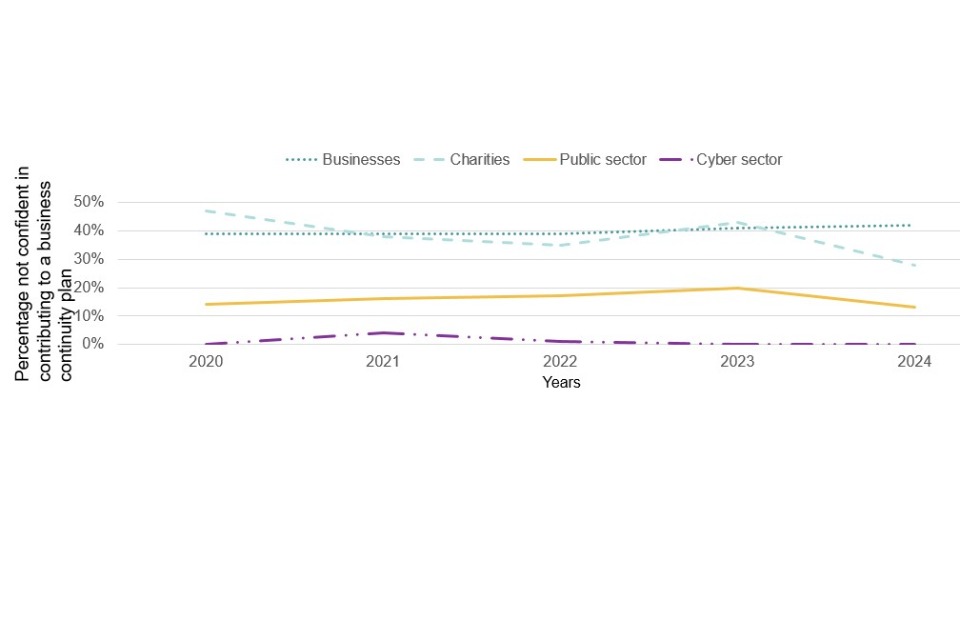
Despite this widespread lack of confidence in governance and compliance skills, there is a broad consensus among cyber sector employers that these skills are important. Half (50%) say that it is essential for staff to understand the legal or compliance issues affecting cyber security, which is in line with 2023 (42%).
4.6 Cyber skills gaps in the non-cyber workforce
While cyber leads and their teams within organisations need to have a wide range of detailed technical and best practice knowledge in cyber security at their disposal, it is just as important for the wider workforce outside these teams to understand cyber security risks and to follow the rules and processes put in place by their organisation.
Perceptions of skills gaps
Most cyber leads feel that senior management at their organisations have an adequate understanding of the risks, rules and processes relating to cyber security. In businesses, around two-thirds say their senior managers understand the cyber risks they face (66%) while around three in five believe that senior managers understand cyber security staffing needs (62%), and the steps to follow when managing a cyber incident (60%). A little over half (54%) say their managers know when cyber breaches need to be reported externally. This is significantly lower than 2023 for businesses.
It is notable that once again this year, senior management within large businesses and the public sector are felt to have a better understanding of these issues, while charity managers are felt to understand them less well.
Figure 4.21: Percentage of cyber team leads that feel their organisation’s senior managers understand the following aspects of cyber security very or fairly well
Table 4.1: Percentage of cyber team leads that feel their organisation’s senior managers understand the following aspects of cyber security very or fairly well for 2023 vs. 2024
In the qualitative research, some cyber leads said they struggle to get senior management to take cyber security seriously and to focus time and energy on it. Some felt senior management did not grasp the importance of issues such as governance or see cyber security as a priority.
They’re happy to look into it, but it needs a lot of explaining and it’s not treated at the moment as an urgent priority. It’s treated as a ‘let’s work on it in the background and slowly develop it over the next year or two.’
Some cyber leads found it difficult to convince their senior team to invest in cyber security. While there was some awareness of its importance, cyber security was not regarded as a pressing matter.
The management team don’t want to spend any money. Cyber security is on their radar, but it’s not seen as urgent. We need to make them more aware.
Beyond senior management, cyber leads’ assessment of ability of non-specialist staff within their organisation to undertake various cyber-related tasks varies greatly, as Figure 4.22 illustrates. Among businesses, few express a lack of confidence in non-specialists’ staff being able to carry out basic tasks such as identifying fraudulent emails or websites (5%) or using acceptably strong passwords (8%). However, working collaboratively with those directly responsible for cyber security has increased since 2023 (19% to 27%).
There is much more concern about non-specialist staff’s abilities when it comes to more technically demanding areas such as storing or transferring personal data securely (37% not confident – and 49% in large businesses) or detecting malware on the organisation’s devices (34%). In these areas, there has been little change in the assessment of cyber leads since 2023.
Figure 4.22: Percentage not confident in non-specialist staff being able to carry out various tasks that can impact on cyber security
Bases: 465 businesses; 22 large businesses (with 250+ staff); 190 charities; 130 public sector organisations. The subsamples are very small for large businesses and public sector organisations (c.20+) so they have not been included.
Table 4.2: Percentage not confident in non-specialist staff being able to carry out various tasks that can impact on cyber security for 2023 vs. 2024
Bases: 465 businesses; 190 charities; 130 public sector organisations.
As we have found in previous years, cyber security leads felt that it can be very challenging to ensure staff understand what they need to do to reduce the risk of cyber attacks.
We know what all the pitfalls are, but it’s trying to get that over to other people.
A recruitment agent made the point that cyber staff need to be able to articulate the benefits of cyber security to the rest of the organisation.
Security has been seen as a blocker, it needs to be seen as an enabler. Cyber specialists need to be able to build a case for what they do more compellingly than before.
4.7 Qualitative findings on future skills needs
In the qualitative research this year, we asked employers and recruiters about future skills needs and what impact they thought AI and automation would have. Some brought AI up spontaneously. Participants highlighted AI ’s impact on the threat landscape; AI can enable threat actors to carry out attacks which are quicker, much greater in number and increasingly sophisticated. From a more positive perspective, participants highlighted the role AI platforms and software can play in protecting against cyber threats. AI tools are already being deployed and some cyber firms are exploring different use cases for AI .
We have not even scratched the surface. AI could be used as a threat or to protect your business. I think that is a very much a growing area with cyber security.
(Private sector, 1,000 or more employees)
Employers and recruiters generally believed that AI is likely to have a major impact on the skills landscape. Some thought that this will happen quickly.
I think that [cyber skills] are going to have to change very, very quickly and be really, really agile. Just the rise of AI , where that’s going to be next year, in two years, is going to be phenomenal. We need to be able to keep up with that pace.
Participants thought that AI would impact the cyber skills landscape in a number of ways. Some said that there would be more automation of cyber tasks. Examples given were first level security operations analysis and code review. There was some concern that AI and automation could lead to job losses in the cyber sector.
Some participants highlighted that skills will need to evolve in order to understand – and act upon – AI tools. Some felt there are risks in using tools that are not fully understood and/or are automated.
The marketing at the moment is very much automated and managed threat response. Here is a tool which will scale all your logs and flash up a light on the screen. You do run the risk of just looking at traffic lights and going ‘oh right, I’ve got a red light. I’m supposed to do something?’
(Private sector, 250-999 employees)
Other changes predicted by participants are roles becoming ‘ AI cyber’ rather than just ‘cyber’ and the emergence of new niches and deep specialisms such as ‘cyber security machine learning.’ While there was general agreement that AI is likely to transform the skills landscape, there was also a great deal of uncertainty about how this will play out.
I think [cyber security skills] will change dramatically. AI can be seen as a threat and also as a positive. How it is going impact, I think it is very difficult to tell.
5. Outsourcing cyber security
The focus of this chapter is on organisations outside the cyber sector that outsource any aspects of cyber security and specifies the functions outsourced.

5.1 The prevalence of outsourcing
Charities are least likely to outsource with less than 3 in 10 (28%) doing so, followed by businesses (38%). The public sector is most likely to outsource with more than 6 in 10 (61%) organisations outsourcing any aspect of their cyber security.
Figure 5.1: Percentage of organisations that outsource any aspects of their cyber security to external providers
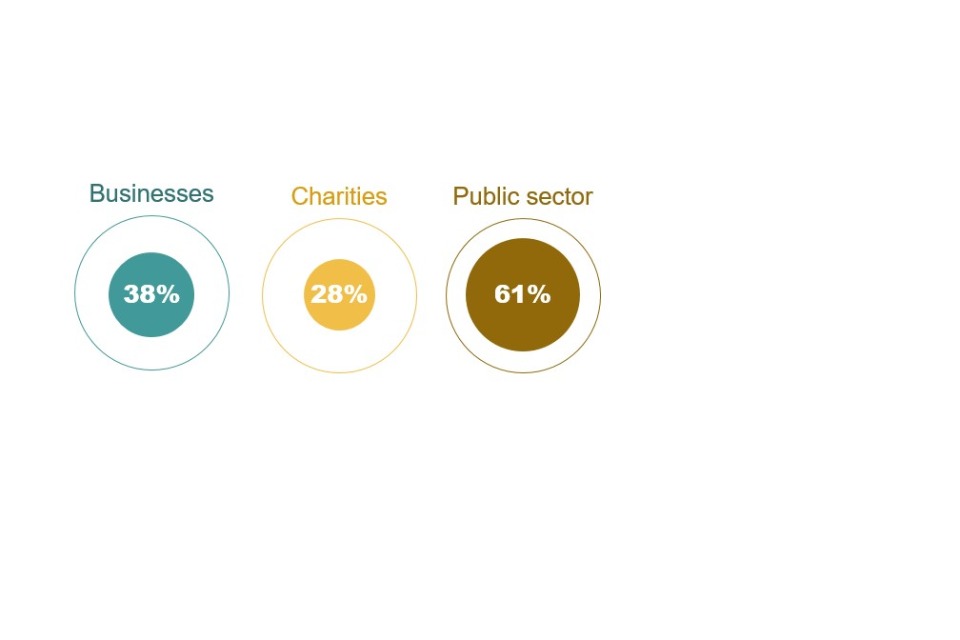
Bases: 930 businesses; 190 charities; 130 public sector organisations
The trend for outsourcing has been fairly consistent over the different waves of this research, as can be seen in Figure 5.2. Public sector organisations have been most likely to outsource, followed by businesses and then charities.
Figure 5.2: Percentage of organisations that outsource any aspects of their cyber security to external providers (Organisation trend data)
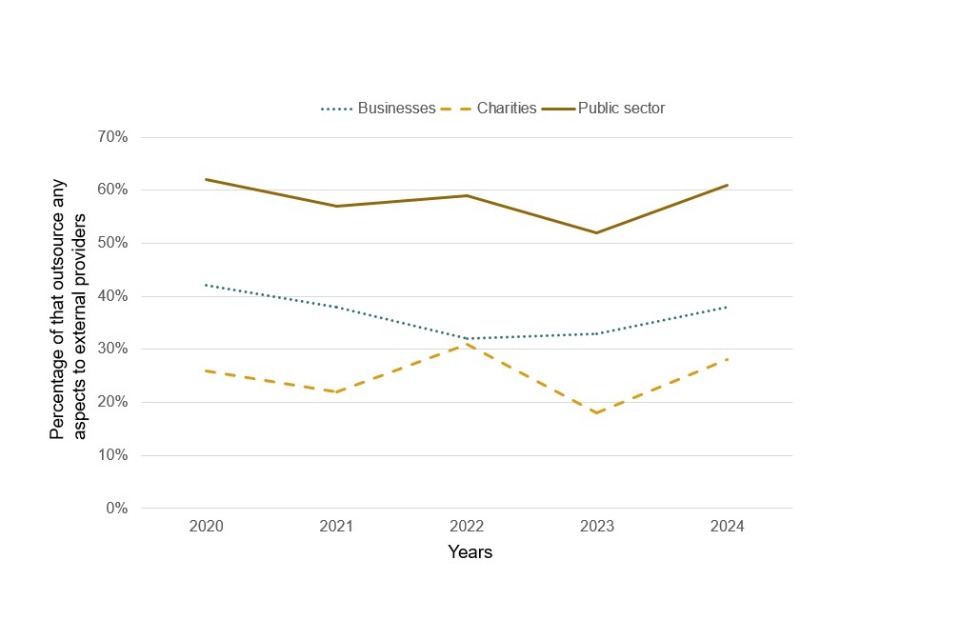
Consistent with estimates from the previous three waves of this research, companies in the finance and insurance sector are still more likely to outsource cyber security functions (62% vs. 40%l). Conversely, the sectors least likely to outsource cyber security are entertainment, service or membership organisations (17%), information and communication (19%), agriculture (32%) and wholesale (35%).
In the next sections, the specific basic and advanced functions that are outsourced are outlined. The split between basic and advanced functions is based on the definition and categorisation of cyber security skills established in the 2021 study.
Outsourcing of basic functions (including incident response)
Figure 5.3 outlines the types of basic cyber security functions different organisations outsource. Amongst all organisation types, setting up firewalls and incident response or recovery is part of the top 3 basic functions outsourced and controlling admin rights are in the bottom 3. This pattern is in line with 2023.
Similar to previous years, most organisations handle at least some elements of cyber security internally, even if they enlist services from external providers for certain tasks. However, of organisations that outsource, some outsource all the basic functions of cyber security which are outlined in Figure 5.3. This includes 42% of charities, 31% of businesses, and 47% of public sector organisations. This is similar to previous years for public sector and business, but a higher proportion of charities have reported outsourcing all their cyber functions in 2024.
Figure 5.3: Percentage of organisations outsourcing various basic cyber security functions, among those that outsource any aspects
Bases: (among those that outsource cyber security): 403 businesses; 76 charities; 86 public sector organisations
Use of Security Operations Centres ( SOCs )
Usage of Security Operations Centres ( SOCs ) is similar to previous years (see Figure 5.4 below). Public sector (36%) and large businesses (34%) are more likely to use SOCs , while charities (12%) and businesses (17%) are less likely.
Figure 5.4: Percentage of organisations that outsource using Security Operations Centres (All organisations trend data)
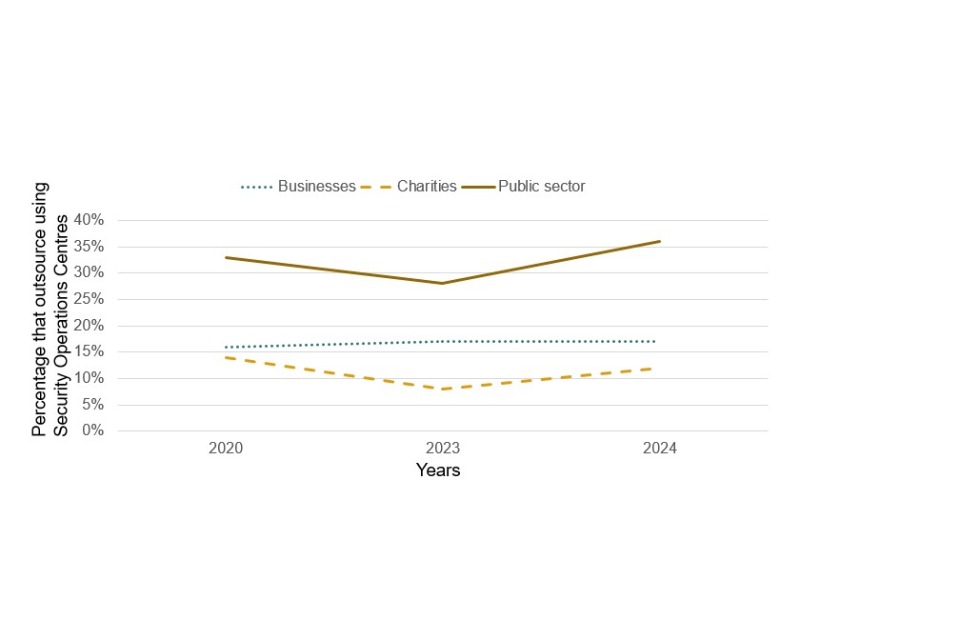
Outsourcing of other more advanced functions
Figure 5.4 illustrates the advanced cybersecurity functions that are outsourced by businesses. This chart includes two sets of figures, namely, businesses that outsource any aspect of cyber security, as well as all businesses (including those who do not outsource at all).
Similar to 2023, just under 1 in 5 businesses (18%) outsource any of these advanced functions. There is again a broadly even spread between which functions are outsourced, with automated defence against malicious network, interpreting malicious code, and vulnerability scans being the most outsourced, similar to last year. Please note that due to low base sizes for charities and public sector, we have not reported their proportions for advanced cyber security functions that have been outsourced.
Figure 5.5: Percentage of businesses outsourcing various advanced cyber security functions, among those that outsource any aspects
Bases: 930 businesses; 403 businesses that outsource cyber security
In the qualitative research, we found that some organisations that outsource do so in very specific and limited ways, for instance penetration testing, staff training or advice on cyber security policies and procedures.
We outsource monitoring the endpoint to the business and also use them to advise us on our policies and procedures around cyber security. They have the knowledge and experience.
For other organisations, outsourcing cyber security responsibilities on an ongoing basis is necessary because they do not have the resources, skills and knowledge in-house.
We have outsourced because we are only two here [in the IT department], we cannot look after everything. It’s the volume and the skills set that they are able to bring. They have been able to stop cyber attacks coming through e-mails and stop any ongoing threats.
6. Recruitment and skills shortages
This chapter deals with organisations’ approaches to recruitment, skills shortages – a shortfall in the number of skilled individuals working in or applying for cyber roles, and an exploration of the changes to the candidate pool. It will also focus on exploring the challenges and barriers organisations face when trying to address skills shortages and changes to the candidate pool.
6.1 Approaches to recruitment
A little under half (47%) of cyber sector businesses have tried to recruit someone into a cyber role since the beginning of 2022. This is in line with last year, when just over half (53%) had been trying to recruit.
As Figure 6.1 shows, this decline is also reflected in the average number of vacancies reported by each cyber firm. After a sharp increase to 8.2 in 2023, this has now fallen back again to an average of 6.1 per firm.
Figure 6.1: Mean number of vacancies per cyber firm trend over last 4 years
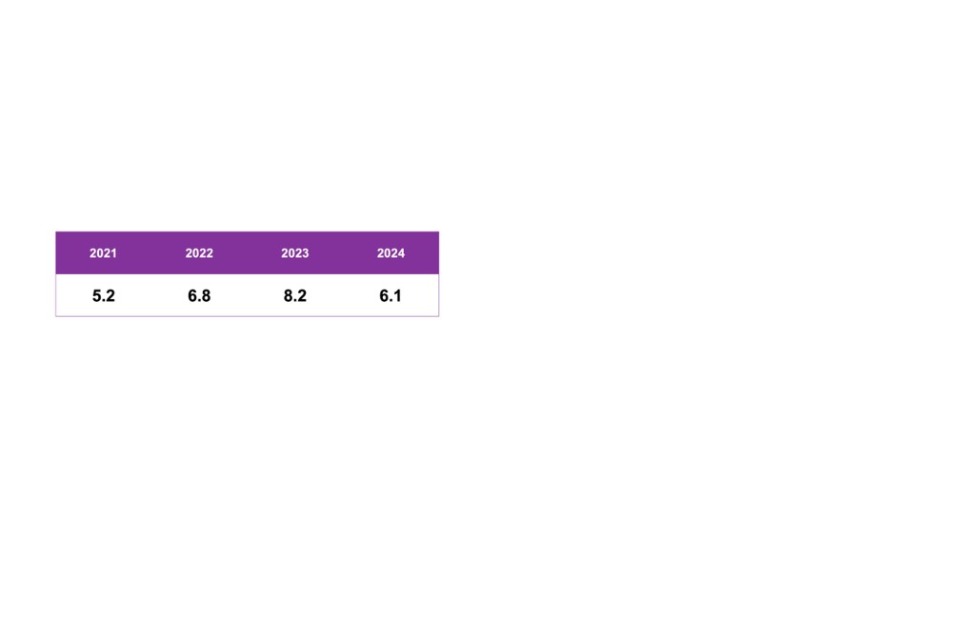
Bases: 84 cyber sector businesses that have had vacancies in cyber roles since the start of 2022
In this chapter, we focus on the approach and experiences of the 47% of cyber businesses that have attempted to recruit recently. We then later in the chapter also look at those who have had vacancies they found hard-to-fill.
Most common recruitment methods
Figure 6.2 shows the most common outreach methods used by the cyber businesses that had recently tried to recruit into a cyber role, and how they compare to those reported in 2023.
Once again, results are broadly comparable with those obtained in previous years: however, the use of social networks has once again moved ahead of other methods. Now mentioned by 43%, of all the outreach methods, social networks have seen the sharpest increase since the first year of the study in 2020, when they were mentioned by only 26%. Word-of-mouth recommendations (33%) and using a generalist recruitment agency (27%) are the next most popular. Both generalist and specialist recruitment agencies have seen an increase in reported use over the last year, with generalists having a statistically significant increase.
In addition, there has been an increase in those reporting that they used a generalist recruitment website such as Indeed (climbing from 15% in 2023 to 27% in 2024).
Just under half (44%) of cyber businesses had used a single recruitment method. Of the remainder, one in four (25%) had used two recruitment methods, and 23% had used three or more. Only a few (8%) had used no recruitment methods over the last year.
It is notable that the use of professional networks – either via word-of-mouth (33%) or using a professional networking website like LinkedIn (43%) – remains the most popular approach for those recruiting into cyber roles, ahead of conducting a broader search using an agency (32% generalist, 30% specialist) or a job advert (20%).
Figure 6.2: Percentage of cyber firms with vacancies that have used the following recruitment methods (unprompted – multiple answers allowed)
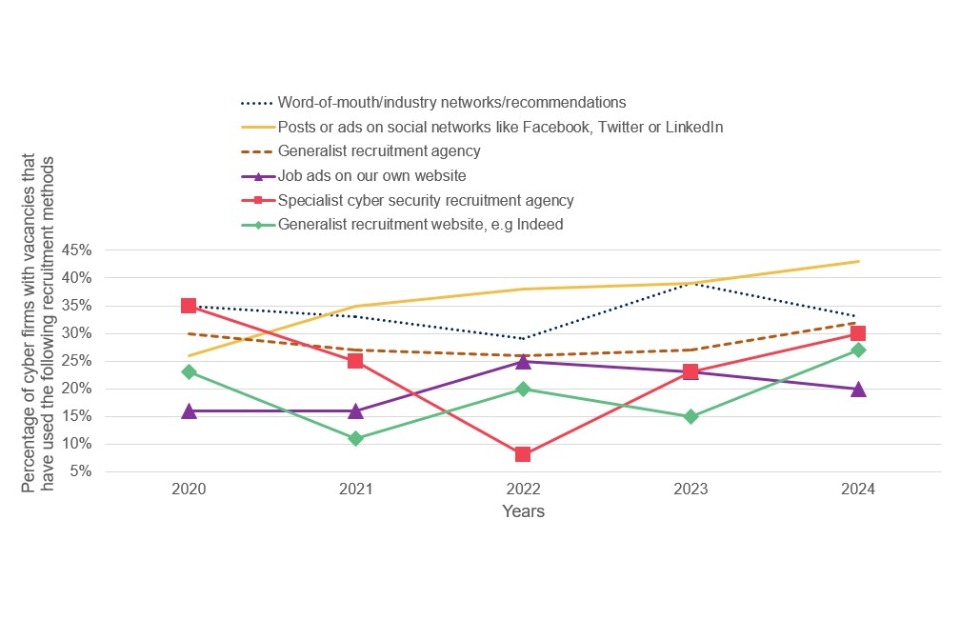
Bases: cyber sector businesses that have had vacancies in cyber roles since the start of 2022. 2024: 84; 2023: 96; 2022: 118; 2021: 81; 2020: 139
Qualitative findings on cost of recruitment
In this year’s qualitative research, we asked employers and recruiters about the cost of recruitment. The most popular forms of recruitment, word-of-mouth and social media, have the obvious advantage of being cheaper than using a recruitment agency. One cyber firm said they had been spending about £160,000 a year on recruitment agents. Since switching to LinkedIn, their annual recruitment costs had fallen to £10,000.
Although recruitment agents cost more than other recruitment methods, other options may be less successful. For instance, a couple of employers had advertised roles and got no responses at all. Recruiters also save employers time by filtering candidates. Some employers expressed a sense of inevitability about using recruitment agents.
We do internal referrals, so that avoids an agency fee. Because that’s probably the one biggest chunk of cost in that space. But it’s something that we factor into the cost to do business. It would be nicer if it wasn’t there, but it is what it is really.
Recruitment agents recognised that employers would rather not pay agency fees and that sometimes they are used as a last resort if other methods have not worked. Recruiters said they have to be competitive on costs and that some clients, particularly new ones, will negotiate on cost. One recruiter observed that fees in the UK (around 15% of the candidate’s annual salary) are lower than other European markets, where they can range from 20%-35%.
There’s obviously a lot of pressure on internal talent teams to try and find people directly, so you don’t have to pay external fees, which is fine. It is what it is. For the harder roles, whereby they’ve tried those avenues and they haven’t succeeded for three or six months, then that’s generally where they come to us, because we have quite deep networks.
Recruitment agents explained that employers use them because their networks enable them to find the right people for roles. These networks are built through referrals, industry networking, LinkedIn and head hunting. Networks also include the pool of candidates previously placed. Recruiters said they are often competing against internal talent teams. However, they felt that internal teams do not have their networks or a deep understanding of cyber.
Although cyber is a niche, there’s so many niches within cyber that it can be difficult to pinpoint the exact skill set. A good example is a security analyst. You can get a security analyst job that pays £35k, and then you can get a security analyst job that pays £120k. It might be a security analyst on reverse engineering malware, or it might be a security analyst on administering systems. It’s two very different jobs.
Employers also raised salary demands when asked about the cost of recruitment. A few mentioned the costs and time involved in getting new joiners up to speed.
I had someone who came to me last year, who looked really good on paper, who wanted a salary that was about 25% above market rate and he had no practical experience.
Qualitative findings on the impact of remote working on recruitment
There is some evidence in the qualitative strand of a move away from remote working. Remote and hybrid working had become widespread during the pandemic, widening the available talent pool. Some employers observed that more people are returning to the office. Recruiters said that clients are increasingly wanting candidates to be based in specific locations.
Businesses now want more in office presence. Last year it was just find the right skills, now they want it in a geography, which limits the pool.
Employers and recruiters highlighted the benefits of being in the office in terms of collaboration, knowledge sharing, onboarding new staff, socialising, and security (especially for less experienced staff). In person presence was thought to be particularly important for leadership and sales roles, as well as consultancy assignments which need to be on-site.
It does seem to be going back to more people in the office some of the time and the advantages to that are collaboration and maybe the social aspects of it as well.
Recruitment agents felt there can be a mismatch between what employers and employees want in terms of in person working. One recruiter pointed out that people with 5-12 years’ experience often also have young families and value being able to work from home some or all of the time.
It’s swinging back that’s for sure. A lot of organisations are really now saying we want people back in the office two to three days a week. There’s some clients I’m working with that want people back in four to five days a week.
Continuing to offer remote working could potentially be an advantage for organisations which struggle to compete on salary and which have been negatively impacted by the talent pool being widened.
Being flexible in terms of work-life balance is definitely going to appeal to people, particularly as the world spins back around again to more office-based roles. Promoting that work-life balance is really key.
Qualitative findings on public sector recruitment
This year we explored public sector recruitment in the qualitative research. Employers and recruiters consistently highlighted salary as a problem. A recruitment agent gave the example of a public sector organisation offering a salary of £75,000 for Chief Security Officer role which, based on private sector benchmarks, should have been closer to £175,000. Recruiters said that public sector organisations get around salary difficulties by lowering the level of experience required for a role, as well as using contractors to plug gaps.
They need to offer candidates the right salary levels at the start if they want permanent people and to attract the right talent.
There were other barriers for public sector organisations mentioned, although less often than salary. These were that the rise of remote working has made the work/life benefits associated with the public sector less compelling (although this may be changing as discussed in the previous section), budgetary constraints on cyber resources and pensions being less attractive than they were. However, some employers and recruiters felt that public sector organisations had some distinct advantages to offer cyber staff. These were better overall packages (e.g. pensions and holiday entitlement), work-life balance including flexible working, job stability, interesting work and a sense of purpose.
The attractive part of being public sector, and something that we want to push really, is the social value. When you’re in the public sector, you’re making a difference to people’s lives. There’s also the stability as well. Career stability, great pension, good benefits.
(Public sector, 1,000 or more employees)
A few said that the government could potentially play a positive role as a cyber employer by reviewing public sector salaries, as well as helping to grow talent through entry level roles and apprenticeships.
Qualitative findings on the recruitment of entry level roles and apprentices
Employers thought that entry level and apprenticeship recruitment have a number of advantages. It is more affordable (and some organisations simply cannot afford more experienced candidates). The candidate base is more diverse and may also bring other skills, such as soft skills, to the table. It can also be easier to mould staff to the organisation’s needs.
There are challenges in getting people with the right skills. For example, we use a lot of Microsoft tool sets, Defender type capabilities. All of that is at a premium cost, so we will try and develop and grow our own.
However, employers often said that entry level and apprenticeship recruitment have some significant drawbacks. A key barrier is having insufficient – or indeed no – resource to train these employees up. A related point is that supporting inexperienced staff can take up a significant amount of senior time and, for cyber firms, diverted them from client work. It can be harder to coach junior people remotely because there is little or no opportunity to learn through observation and informal conversations.
I think for us, we need to hire senior staff in cyber because we can’t offer that support and mentoring of a junior cyber person. It needs to be someone who can come in at a senior level and hit the ground running.
Some employers felt that inexperienced candidates may lack basic work skills. A few speculated that the pandemic could have exacerbated this issue.
I don’t know whether it’s COVID or some other factor, but just generally their readiness to come do a full-time job seems to be quite low. And there’s quite a lot of wellbeing challenges and capability challenges that a lot of the last three or four years of new early career joiners have had. Their last stages of education were often done completely virtually.” (Cyber sector firm, 1,000 or more employees)
Employers thought that these roles carry a greater risk that a candidate is not a good fit because they have no track record. Another risk is that they leave after being trained up. For cyber firms, a specific issue is that clients want to work with more experienced people.
It could be a baptism of fire sometimes. It’s hard to gauge how they’re going to go until they actually start the job. There is that element of if there’s no track record, then what can you measure?” (Private sector organisation, 50-249 employees)
Employers raised specific benefits and barriers in relation to apprenticeships. Some felt that these candidates could be even more mouldable and enthusiastic because they had chosen to start working in cyber security instead of going to university.
The very, very big pro is being able to grow your own. What we’ve learned from bringing the apprentices in is you do grow your own, and you can mould them and nurture them and make them fit the holes in the organisation that you’ve got.
Another benefit of apprenticeships which employers mentioned is that government funding can be available. A few employers also highlighted the benefits to apprentices because they can learn on the job, earn a salary and get a qualification.
From our point of view, degree apprenticeships are the best deal ever. They’re not publicised well enough. I talk to lots of people about our degree apprentices. Government pay 95% of that, and we pay the 5% of that whole three-year degree. That student comes out with no debt and we pay a salary and I think that they need to promote that more.
However, employers also felt that apprenticeships have some distinct disadvantages. Some of these relate to apprentices being assumed to be school leavers. Employers thought that they were even less prepared for work than graduates because they are younger and had not had the experience of studying at university. Employers said that apprentices require more support and pastoral care than other entry level roles.
We have to put a lot more of a pastoral wrapper around those apprentices than we would do for a graduate, and that’s taken us a while to understand exactly what that looks like, and the differences that a 17, 18 year old needs in terms of support and understanding and coaching that a 22, 23 year old does, or a 40 year old does.
Cyber firms had particular concerns about apprentices working with clients because of their age and inexperience.
That would really worry me about offering apprenticeships, it’s their lack of experience. They need to be client-facing from the start and my worry would be putting an 18 year old school leaver in front of a client, are they going to have the gravitas?” (Cyber sector firm, 1-9 employees)
Some employers thought that the course content for cyber security apprenticeships is not always current. For instance, courses do not incorporate new areas such as AI . One employer commented that courses are generally a year behind industry.
A lot of them don’t keep up with industry. They’re like a year behind. He’s [cyber apprentice] learning his basics but some of those basics will fall off. A lot of this stuff can be automated. Some of the stuff that he’s being trained on now will be automated by our other part of the business.
A related issue is that some course content may not be relevant for employers. One example given was apprentices working for a consultancy firm learning hands on skills such as operating a vulnerability management tool which they would not use. There can also be the practical issue of fitting in work around studies. Some employers said it would be helpful to have employer input into course content so that it is more up to date and relevant (e.g. include soft skills).
We ask them, what have you learned today? And they talk about things that, well, really do we need to know about that? Things like how to do vulnerability scanning, how to do ethical hacking, simulations. We don’t really do any of that.
We asked employers what would encourage them to take on entry level employees or apprentices. They said there would need to be a clear need (for instance the business was growing) as well as sufficient internal resources to support junior staff. For apprenticeships, employers said they would welcome some sort of financial help such as funding or tax incentives.
Some sort of bursary, we are absolutely strapped for cash. That would attract good candidates and that would be fantastic. You see that in other sectors, education for example. We give them a bursary and that attracts people.
Employers said it would be helpful to be able to access information and support. In particular, they would like to understand the benefits of cyber apprenticeships, what apprenticeships cover and their relevance to their organisation.
Depends what is included in cyber apprenticeships. I am looking for all round knowledge of technology and how it works and applying a management system to it. So, to offer it in the future, I would need to see a well-structured apprenticeship programme.
Employers would also like information about the practicalities such as finding training providers, how to put apprentice programmes together and what support is available. Some commented that government could have a role in raising awareness of cyber apprenticeships and providing information.
We need to know how it works, what benefits the organisation will get from it.
On entry level roles, employers said it would be beneficial to understand potential career pathways, as well as what training resources and funding are available. As we have seen in Section 2.3, employers and recruiters thought that the UK Cyber Security Council’s Cyber Career Framework is a valuable resource for new entrants into the sector.
6.2 Hard-to-fill vacancies
As in previous years, most of these hiring businesses have experienced at least some difficulty in filling these roles. This year, seven in ten (70%) of cyber firms with vacancies say they have had at least one vacancy that was hard-to-fill – a slight increase from the 67% who reported this in 2023.
Overall, we estimate that (55%) of vacancies themselves are hard-to-fill this year. This compares to 37% in 2023.
Reasons behind hard-to-fill vacancies
The main reasons for these vacancies being hard-to-fill have remained consistent, as Figure 6.3 shows. Without being prompted, cyber firms most commonly say that the reason for hard-to-fill vacancies was a lack of technical skills or knowledge, which is cited by over half (52%).
This was also the top reason given in the 2021, 2022 and 2023 studies. Other significant reasons included low pay or benefits that did not meet candidates’ expectations (26%) or a lack of soft skills (24%). The proportion reporting that a lack of work experience was an obstacle to hiring declined from 27% in 2023 to 16% in 2024. It was as high as 35% in 2021, suggesting that the pool of candidates with relevant professional experience is increasing as the sector matures, even if this is not necessarily translating into suitable skillsets to meet market demand.
Figure 6.3: Most common reasons offered by cyber sector businesses for having hard-to-fill vacancies (unprompted – multiple answers allowed)
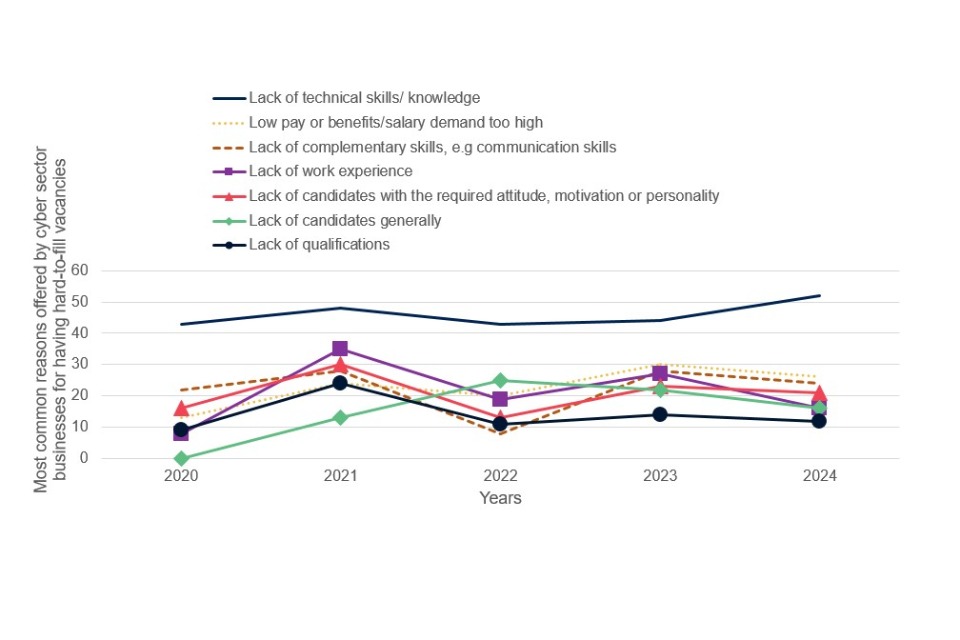
Bases: Cyber sector businesses that have had hard-to-fill vacancies in cyber roles since the start of 2022. 2024: 84; 2023: 64; 2022: 79; 2021: 46; 2020: 79.
Specific roles affected by skills shortages
The survey once again reveals widespread skills shortages across both generalist and specialist roles. Among cyber sector businesses with hard-to-fill vacancies, 40% report that these were in generalist roles, equating to 13% across the overall sector population.
As Figure 6.4 shows, most commonly, these were generalist roles within cyber security itself (31%). [footnote 8] Only smaller minorities reported that these were generalist sales (10%) or IT roles (5%), or at senior management level (5%).
Figure 6.4: Percentage of cyber sector firms that have found it hard-to-fill the following generalist job roles (multiple answers allowed)
Bases: 180 cyber sector businesses; 58 that have had hard-to-fill vacancies in cyber roles since the start of 2022
Rather than in generalist roles, though, most of these hard-to-fill vacancies tended to be in specialist roles – 59% vs. 40% in generalist roles. Unlike in previous years, the most frequent hard-to-fill specialism this year was around security governance, compliance and legal, mentioned by nearly three in ten of those with a hard-to-fill vacancy (28%).
Penetration testing, the most frequently mentioned area of skill shortage in previous surveys (mentioned by 19% in 2023), was mentioned by only 9% of those with hard-to-fill vacancies this year. This may indicate that the supply of this skillset within the market is starting to more closely mirror demand, which is critical but confined to a relatively small subset of firms. Further waves of research will be needed to validate this trend.
Figure 6.5: Percentage of cyber sector firms that have found it hard-to-fill the following specialist job roles (multiple answers allowed)
Specific levels or grades most affected by skills shortages
As Figure 6.6 illustrates, most skills shortages continue to be in mid-level or more senior roles that require at least 3 years of experience, with a significant rise from 2023. This is well in line with results from previous years, although significantly fewer this year report that their hard-to-fill roles are at principal level or above, requiring 6+ years of experience (22%, compared to 42% in 2023).
Figure 6.6: Percentage of cyber sector businesses that have found it hard-to-fill positions at the following levels, among those that have had hard-to-fill vacancies
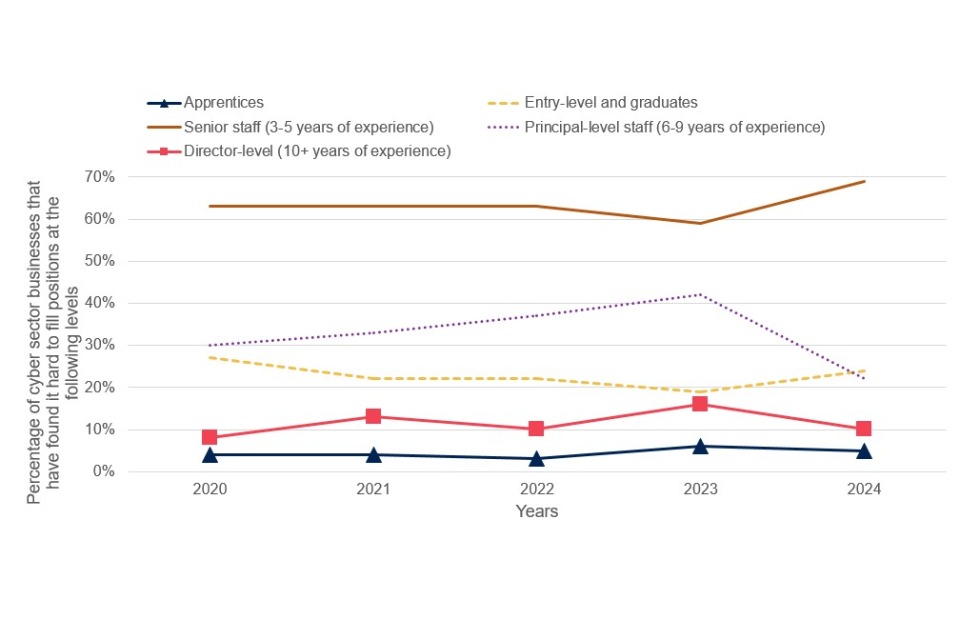
Bases: Cyber sector businesses that have had hard-to-fill vacancies in cyber roles since the start of 2022. 2024: 58; 2023: 64; 2022: 79; 2021: 46; 2020: 79
This was echoed in the qualitative research; finding cyber employees with mid-level experience can be particularly challenging. One recruitment agent suggested that the pandemic has made this shortage more acute.
It’s the people who are at the 5-9 years’ experience mark. We had a global plague 4 years ago so they don’t exist. So you either hire less than what you need or more.
Qualitative findings on hard-to-fill roles
Employers and recruiters highlighted roles relating to the cloud, security architecture, secure development and threat intelligence as being particularly hard-to-fill.
The market has changed in the last few years. Post-pandemic, many organisations have moved completely cloud based, with no physical server. There is a huge uptick of organisations wanting to be more cloud first or cloud-centric.
A couple mentioned AI experience as being in short supply. As we discuss in Section 4.7, this is a growing area of importance in the sector.
AI in general is something that is particularly hot at the moment. It’s hard to find, it’s also very new, so no one’s got 20 years’ experience in Gen AI .
Recruitment agents commented that employers sometimes want a challenging mix of skills, for instance very specific technologies in a particular location (because the role is in person). One example of a difficult role to fill was an employer looking for someone who had both cloud and coding skills and who would also be a good fit with the team.
They’re looking for someone that’s got a very, very strong background in cloud. They also want a bit of coding in there as well. Cloud and coding normally are two different skill sets. They want someone with a vibrant personality and that will fit into the team and all this sort of stuff as well.
Candidates who have both complementary (sometimes referred to as soft skills) and technical skills continue to be in great demand. As we have found in previous years, the ability to understand both the technical and business elements of cyber security is highly valued.
People that have a really deep and broad technical security background but can also talk and converse with the business. It is quite a rare skill set.
One area where shortages did not tend to be identified by cyber firms was in entry level roles. These roles were defined in a wide variety of ways. As Figure 6.7 illustrates, definitions of the minimum requirement for ‘entry level’ work in cyber security varied from having no qualifications at all, to having A-Levels, an undergraduate degree, or 2-3 years’ of work experience.
Similarly in the qualitative strand, there were several different understandings of what an entry level role is, and no commonly accepted definition of what would qualify someone to be appointed into one of these roles. It may be important to define ‘entry level’ more closely to enable future candidates to identify what type and level of qualification they should aim for.
Figure 6.7: Percentage of cyber firms that have chosen the following as minimum requirement for an entry level role
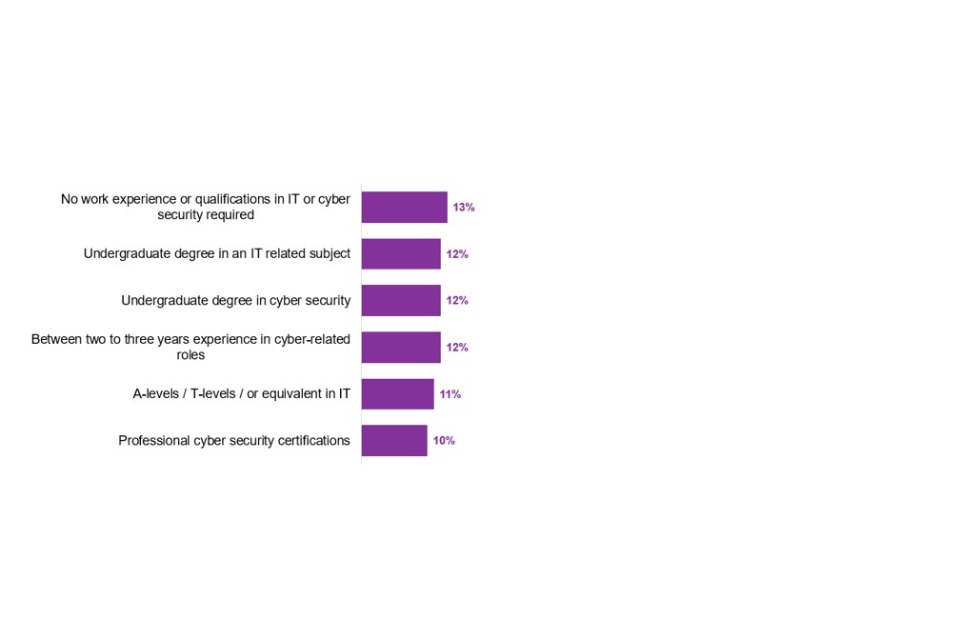
Bases: 180 cyber sector businesses. Only specific categories mentioned by 10% or more shown.
7. Cyber security job vacancies
This chapter sets out a profile of online cyber security job vacancies. This is based on our analysis of secondary job vacancy data using the Lightcast Analyst platform. It explores the number of job postings, the roles, skills, qualifications, and experience levels in demand, where the demand is coming from (both in terms of economic sectors and geographically) and the salary levels offered. This data focuses on the 2023 calendar year (1st January to 31st December 2023).
Whereas the survey results covered in other chapters are based on a random sample of businesses from the wider population, the charted findings from this secondary analysis are based on the entire dataset of online job postings.
7.1 Core versus all cyber job roles
The separately published technical report lays out the methodology used for this analysis. The approach is consistent with that of previous years, allowing for an understanding of the changes in the cyber labour market over time. The search strategy follows that of the 2023 study, using the Lightcast Analyst platform to undertake two searches (consistent with the ‘core’ and ‘enabled’ roles search used in 2021 and 2022 studies). This includes a search for:
- Core cyber roles are formally labelled or commonly recognised as cyber security jobs. They have a greater demand for skillsets and tools directly related to cyber security, such as information systems, cryptography, information assurance, network scanners, and security operations. In other words, these are job roles where some aspect of cyber security is the main job function. This would typically include job titles such as Cyber Security Architect, Cyber Security Engineer, Cyber Security Consultant, Security Operations Centre ( SOC ) Analyst and Penetration Tester.
- All cyber roles includes the core cyber security roles mentioned previously, in addition to roles that may not formally be labelled or commonly recognised as cyber security jobs, but they still require cyber security skills. Alongside cyber security skills, they demand more general IT and business skills, such as project management, risk assessment, network engineering, SQL, system administration, and technical support. This might be because the job requires light touch knowledge and application of technical cyber security skills (e.g. for IT technicians or governance, regulation, and compliance roles) or because the job role includes cyber security functions among other things (e.g. network engineers whose role includes but is broader than just network security). Typical job titles include Computer Support, IT Support Analyst and Applications Analyst.
It is worth noting that all these cyber security job roles typically require a mix of technical and nontechnical cyber security skills. Therefore, these cannot simply be differentiated as technical vs. nontechnical jobs in cyber security.
To be clear, this is a different distinction from the formal versus informal cyber roles discussed in previous chapters, which addresses the fact that most organisations, especially micro businesses, have people carrying out cyber functions on a largely ad hoc or informal basis. By contrast, all the job postings included in this secondary analysis have, by definition, technical aspects of cyber security within their job descriptions. They are all formal cyber roles.
7.2 Number of job postings
The monthly trend for core and all cyber security online job postings is set out in Figure 7.1, spanning the two-year period from January 2022 to December 2023. In the most recent twelve months (i.e. January 2023 to December 2023), demand for cyber security professionals has slowed.
In 2023, there were 97,319 relevant job postings. This includes 48,492 job postings across core cyber roles (an average of 4,041 per month), and 48,827 other job postings requesting cyber security skills.
When compared to 2022 levels, this suggests that the number of core cyber job postings has decreased by 32% (from 71,054 in 2022). Demand for ‘all cyber roles’ has also decreased by 39% in this time period.
Figure 7.1: Monthly number of core and all cyber online job postings from January 2022 to December 2023
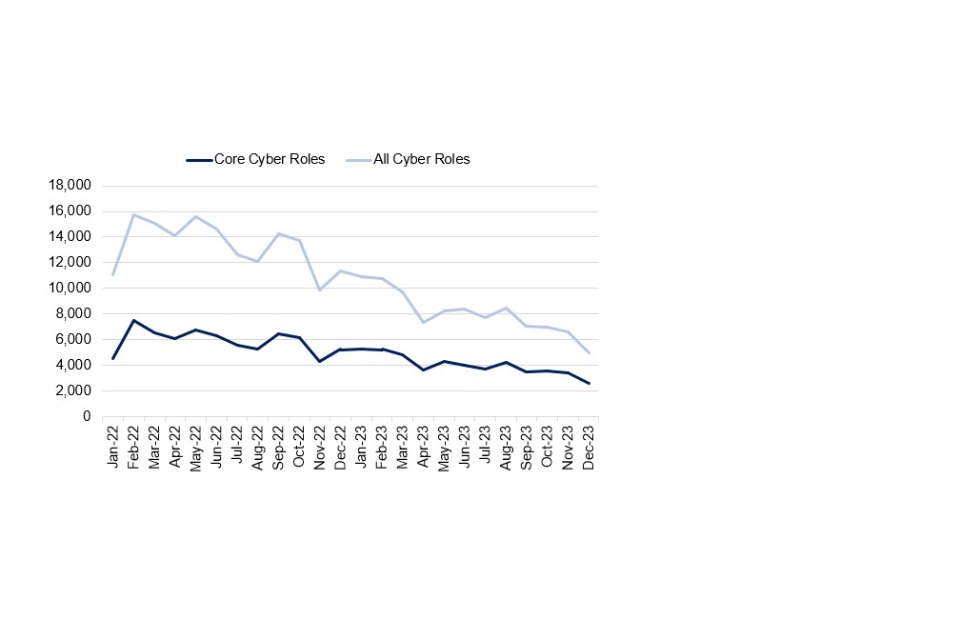
Source: Lightcast Bases: 257,354 online job postings from January 2022 to December 2023 (of which 97,319 were in 2023); 119,546 across core cyber (48,492 in 2023)
Figure 7.2 sets out how the volume of cyber security job postings has changed since January 2021. The job postings for each subsequent month are indexed to January 2021, which has an index score of 100. The indices highlight some seasonal drops in demand in both years, however, this drop is expected and is experienced across core cyber vacancies, wider cyber vacancies, and all digital sectors.
The chart indicates that there has been greater growth in job postings since January 2021 across core cyber roles and all cyber roles than that experienced by all digital sectors. Despite high demand for cyber security professionals in 2021 and early 2022, this demand somewhat slowed towards the end of the 2022. As reflected in both charts, in 2023 there was a slow-down in recruitment activity across not only cyber security professional roles but also across the digital sector as a whole.
Figure 7.2: Index of online job postings (January 2021=100)
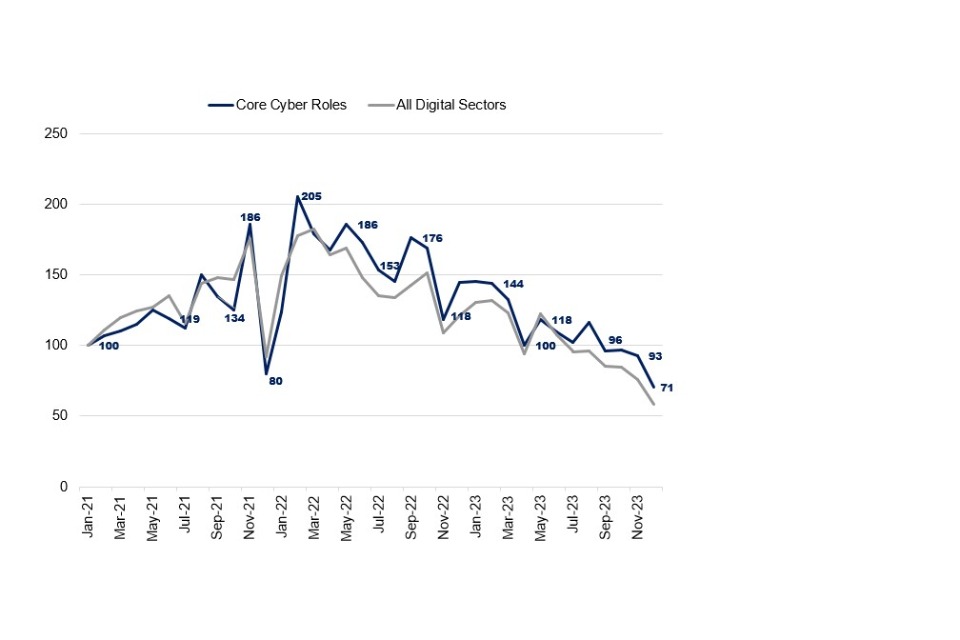
Source: Lightcast Bases: 3,506,124 online job postings from January 2021 to December 2023 (of which 985,675 were in 2023); 173,132 across core cyber (48,492 in 2023); 3,332,992 across all digital sectors (888,356 in 2023)
In the qualitative research, recruiters said that demand in the cyber security market has softened. This was attributed to the economic outlook and organisations limiting their spend. Recruiters said that companies do not have the budget to hire and some were even cutting costs in cyber security for the first time. Another factor mentioned is the market readjusting after a post-COVID spike in demand.
There was a real acceleration coming out of COVID. Everyone moving towards cloud computing and the shackles came off organisations as they started to grow and develop again and the whole market went a bit nuts. There was extreme demand out in the market and that has softened somewhat over the last 12 months. There probably needed to be a bit of a softening because salaries and demand were going a little bit out of control.
A couple of large cyber firms mentioned that they had been impacted by lower spend on cyber security services. One firm made redundancies and had hired fewer staff as a result.
We had to do a restructure this year. We’ve made some redundancies. We saw that the market was going quiet around January this year, so we decided to reduce the number that we were going to recruit.
7.3 Geographical differences
The remainder of this chapter focuses on online job postings from January to December 2023 only. Figure 7.3 shows the proportion of job postings for core cyber roles from each UK region (where region has been provided in the job listing) for 2023. On the heatmap, a darker colour indicates a higher density of cyber jobs in that region. In line with last year’s report, the strongest concentration of job posts falls within London and the South East. However, there has been some growth in regions such as the West Midlands (8% from 6.3%), Yorkshire and the Humber (up to 8% from 6.8%).
Notably, we estimate that 22% of these postings [footnote 9] had no regional location listed (i.e. the roles were marked as ‘Remote’ or ‘UK-wide’). This is a decrease from 2022 (28%), which suggests that there is a downward trend in job postings for remote working and working from home across all regions in cyber security. As we discussed in Section 6.1, in the qualitative research both employers and recruitment agents observed that there has been a move away from remote working.
Figure 7.3: Percentage of core cyber job postings from each UK region (where location is known) Ranking
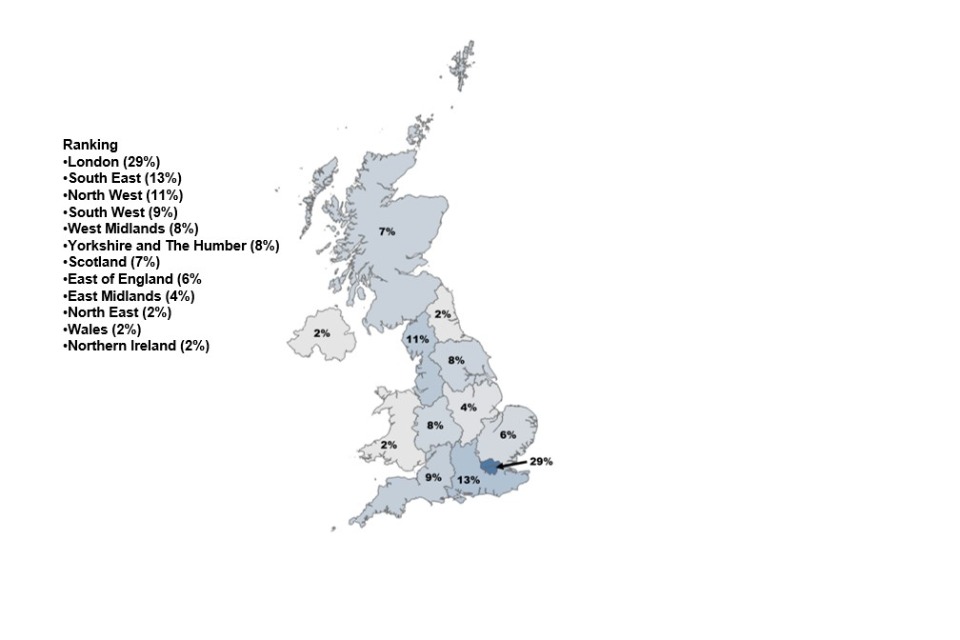
London (29%)
South East (13%)
North West (11%)
South West (9%)
West Midlands (8%)
Yorkshire and The Humber (8%)
Scotland (7%)
East of England (6%
East Midlands (4%)
North East (2%)
Northern Ireland (2%)
Source: Lightcast Base: 38,012 online job postings with location data from January 2023 to December 2023
Figure 7.4 sets out the top cities by number of core cyber job postings alongside the heatmap that highlights the top fifteen UK local authorities in terms of Location Quotient rankings [footnote 10]
The top five cities by number of absolute job postings have once again remained consistent from 2021 and 2022, with Greater London, Manchester, Bristol, Birmingham, and Leeds having the highest number of cyber security job postings.
In terms of Location Quotient ranking by workforce jobs, Reading is the top for cyber security job postings. Some of the highest demand areas include Cheltenham, Bristol, and Manchester. In 2023, there has also been strong demand in areas such as Gloucester, Guildford, Cambridge, Birmingham, and Belfast.
Figure 7.4: Number of core cyber job postings and Location Quotients in the top 15 UK Local Authorities
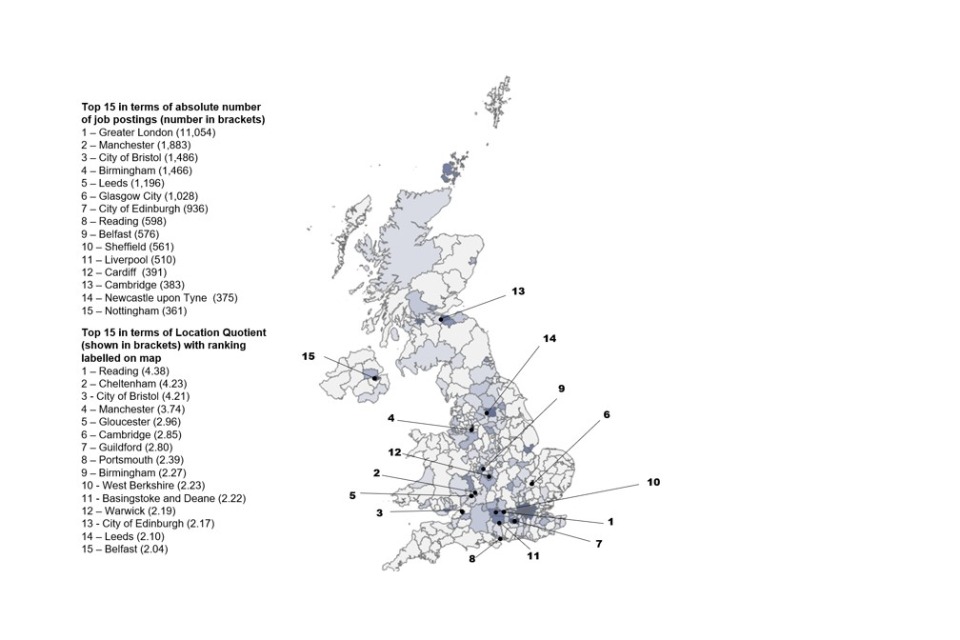
Source: Lightcast Base: 37,806 online job postings with local authority location data from January 2023 to December 2023
7.4 The job roles being advertised
Figure 7.5 lists the identified core cyber roles by job title. Vacancy data can contain several variations of similar titles (e.g. Cyber Security Analyst, and Cyber Analyst), and therefore, as with previous years, minor variations in roles have been combined. [footnote 11]
Figure 7.5: Top recurring job titles among the core cyber job roles identified
Source: Lightcast Base: 17,560 online job postings with job titles from January 2023 to December 2023 featuring one of the top 50 job titles (across 48,492 core cyber job postings).
The four most demanded roles have remained consistent with 2022, however, with some changes in relative proportion. Security Analyst job postings have increased from 16% of roles to 25% of roles in 2023. The proportion of Security Architect postings has decreased, from 11% in 2022 to 3% in 2023.
The top four recurring job titles suggest consistent demand for cyber security professionals within mid-level management roles, particularly within domains such as consultancy, professional services, finance, and public sector, as explored subsequently in Section 7.5. However, many of these roles will have complementary skillsets, and may reflect how employers and recruiters are defining and categorising roles.
7.5 The sectors demanding cyber security staff
Job postings within the dataset are typically advertised through a recruitment agency, with almost half of roles in the dataset linked to recruiters. However, for those roles with a named employer, the data suggests the following sectoral breakdown.
This is not necessarily a comprehensive breakdown. As noted earlier in this chapter, the Lightcast dataset is liable to omit some key large employers that do not post job adverts directly. The following sets out the sectors with the highest demand for core cyber roles in 2023. It is important to note that almost 17,000 (42%) core cyber roles were posted by recruitment agencies, suggesting a demand among employers to use recruiters [footnote 12] . Consequently, the following looks at the top sectors for core cyber postings, excluding employment activities.
Figure 7.6: Percentage of job adverts for core cyber roles coming from specific sectors (where the employer is named)
Source: Lightcast Base: 23,667 core cyber job postings with sector data from January to December 2023 (excluding recruitment agency postings). [footnote 13]
Two of the biggest employers for core cyber roles in 2023 were Unilever and CGI. Further exploration of the key employers of core cyber roles highlights that there remains significant demand among public sector (e.g. NHS), professional services and finance (e.g. Lloyds Banking Group, Deloitte, Barclays, KPMG, EY), telecommunications (e.g. BT, Vodafone), and aerospace and defence (e.g. BAE Systems).
7.6 The skills, qualifications and experience being demanded
Skills in demand.
There has been no major change in the type of skills being demanded for core cyber roles compared to last year. The top three technical skills requirements mentioned in job descriptions are cyber security skills, auditing, and computer security. Other sought-after skills areas include ISO/IEC 27001, vulnerability, risk management, Microsoft Azure, penetration testing, and programming (e.g. Python). Figure 7.7 sets out some of the top requested skills.
Figure 7.7: Top skills requested for core cyber job roles
Source: Lightcast Base: 48,492 online job postings from January 2023 to December 2023
Experience requirements
Figure 7.8 demonstrates that, over the last year, the most common request from employers looking to fill core cyber security roles has been for applicants with mid-level experience (2-6 years, 61%), followed by entry-level applicants (22%).
This preference for mid-level experience is in line with the previous studies.
Figure 7.8: Percentage of core and all cyber job postings asking for the following levels of minimum experience (where any minimum requirement is identified)
Source: Lightcast Base: online job postings with minimum experience listed from January 2023 to December 2023; 13,211 across core cyber; 70,284 across all cyber.
Education requirements
Figure 7.9 sets out minimum education requirements that employers are looking for in core and wider cyber job postings. The results show that 80% of core cyber employers require applicants to have a minimum of a bachelor’s degree (or equivalent), with a further 9% wanting postgraduate qualifications such as a master’s degree or PhD. The proportional share of requirements for wider cyber roles is similar, with just over 80% of employers looking for candidates with a bachelor’s or higher degree. This is in line with findings from the previous study.
Figure 7.9: Percentage of core and all cyber job postings asking for the following levels of minimum education (where any minimum requirement is identified)
Source: Lightcast Bases: online job postings with minimum experience listed from January 2023 to December 2023; 10,552 across core cyber; 54,379 across all cyber.
Qualitative findings on assessing candidate proficiency
In the qualitative interviews, employers and recruiters generally thought that qualifications such as Certified Information Systems Security Professional (CISSP) are beneficial and can give a candidate a more favourable weighting, particularly given the requirement for five years’ experience in relevant domains. As we have found in previous years, employers highly value tangible experience. This is especially the case for candidates who have particularly relevant experience. A recruitment agent gave the example of a fintech firm recruiting someone who has worked with other fintech businesses to set up their security practices. Employers and recruiters felt that qualifications have more significance for very technical roles, where qualifications such as CREST (Council of Registered Ethical Security Testers) certifications are expected. They thought that qualifications can also be helpful when recruiting for junior roles, where candidates do not have much experience. Some employers evaluate the potential of entry level and junior candidates through assessments such as ‘capture the flag’ (a gamified exercise designed to test cyber security skills).
If someone wants a junior person then they might need to have some sort of entry level qualifications, but clients are really more looking at what real life experience can you actually bring to the table rather than a qualification. In an ideal world, you’ve got the qualifications and the real-life experience as well.
7.7 Salaries
Using the Lightcast Analyst platform, we estimate the mean salaries by averaging the midpoints of the advertised salaries and the number of observations. Across the 12 months of 2023, the average (mean) advertised salary was £56,800 for a core cyber job posting (with a median value of £55,000). Please note due to the updated platform, we do not provide a full time series analysis.
As a comparison, for all employee jobs within Standard Industry Classification (SIC) 2007 code 62, which is the computer programming, consultancy and related activities industry code, the mean annual pay increased by 5% from £48,600 in 2022 to £51,300 in 2023 (with median increase of 5% from £42,000 in 2022 to £44,100 in 2023). [footnote 14]
Using this value as a proxy for IT jobs in the UK suggests there is a wage premium of approximately 25% for core cyber security jobs compared to IT jobs (when comparing median salaries). [footnote 15] Figure 7.10 sets out the percentage of core cyber roles offering salaries within the following ranges, where the salary is advertised.
It is also worth noting that around 70% of online core cyber job postings do not contain any salary information, compared to 75% last year. This may suggest limited salary transparency for cyber security roles, or that there continues to be an increase in the use of recruitment agencies and therefore, undisclosed salaries on job adverts.
Figure 7.10: Percentage of core cyber job postings offering the following salaries (where salary or salary range is advertised)
Source: Lightcast Base: 14,176 core cyber online job postings with salary data that can be mapped to a specific UK region from January 2023 to December 2023 (the remainder are based in the UK but may include national or remote locations)
Geographical variations in salaries
London has the highest mean advertised salary for core cyber roles, and is consistently ahead of other regions, as shown in Figure 7.11. Whilst there is variation in salaries across regions, pay disparity across regions continues to decrease (i.e. £23,200 difference between highest and lowest region in 2021, £18,800 in 2022 and £18,300 in 2023).
Figure 7.11: Mean salary offers for core cyber job postings, by region (where the salary or salary range is advertised)
Source: Lightcast Base: 14,176 core cyber online job postings with salary data that can be mapped to a specific UK region from January 2023 to December 2023 (the remainder are based in the UK but may include national or remote locations
8. Staff turnover in the cyber sector
This chapter measures staff turnover within the cyber sector and the reasons why staff have left their posts (where employers are aware of the reason). These statistics were included for the first time in the 2021 report. In keeping with last year, the timeframe captured in these statistics is the last 18 months before the survey, which this time roughly equates to the start of January 2022.
8.1 An estimate of cyber workforce staff turnover
We estimate that 11% of the cyber workforce (within the cyber sector) left their posts in the 18 months prior to the survey (i.e. since around January 2022). This is a bare minimum estimate, as the size of the total workforce in our calculations assumes, for simplicity, that all these staff were all in post 18 months ago (i.e. they did not join and leave within the last 18 months, which is possible). The turnover rate is the same as the last two waves of the data (11% in 2023 and 2022).
8.2 Why employees leave their roles
A total of 8% left of their own volition, with the remaining 3% leaving due to either dismissal or redundancy. This is consistent with the previous two waves of the study where 9% left of their own volition and 2% were dismissed.
In cases where staff left of their own volition, we asked employers about the reasons behind this. It is important to note that this data, shown in Figure 8.1, covers employers’ perceptions of why these employees left their posts, which may be different from employees’ own views. The most common reasons offered by employers is that staff left because the company offer was not good enough and employees were looking for better pay or benefits elsewhere. This is similar to last year.
Figure 8.1: Reasons employers give for staff leaving cyber job roles, among those where any employees left of their own volition (unprompted – multiple answers allowed)
Bases: 49 cyber sector businesses that have had employees leave out of their own volition. Only specific categories mentioned by 5% or more shown.
As can be seen from the table below, employers’ perceptions of why staff leave out of their own volition has remained consistent, particularly from 2023 to 2024.
Figure 8.2: Reasons employers give for staff leaving cyber job roles, among those where any employees left of their own volition (Trend data) (unprompted – multiple answers allowed)
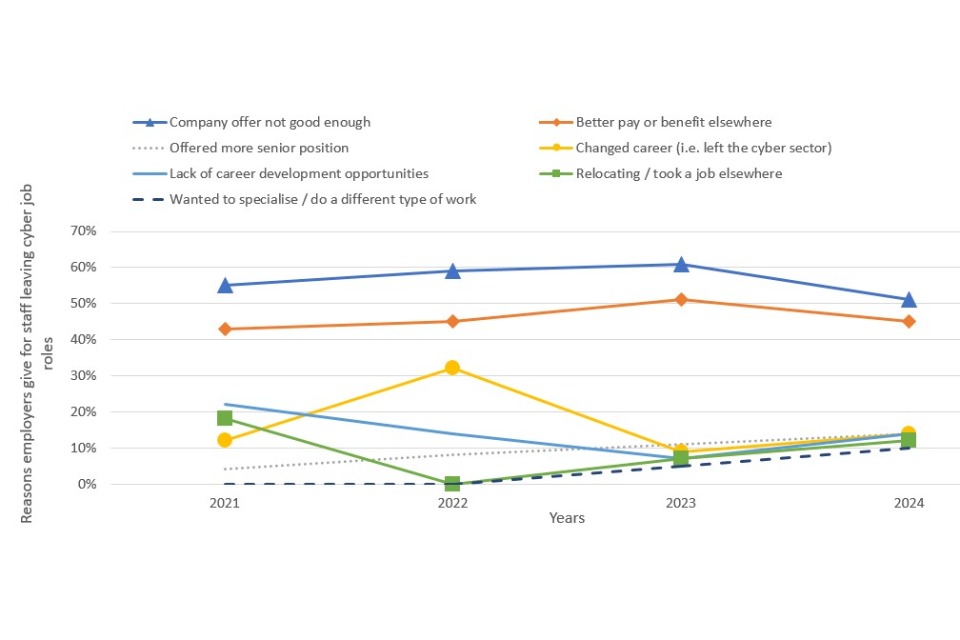
Bases: Cyber sector businesses that have had employees leave since the start of 2021. 2024:49; 2023: 57; 2022: 78; 2021: 49 Only specific categories mentioned by 5% or more shown.
In the qualitative research, employers said that salary is a key reason why staff move. Smaller cyber firms explained that they lose people to bigger competitors who can offer greater opportunities and more pay. Public sector employers said cyber staff can leave for better paid private sector roles. If they have obtained qualifications, their market value increases.
He did really well. He got a 2.1 on the degree apprenticeship programme. But then we couldn’t keep him because there were other businesses who were offering a similar job for a lot more money.
Some employers said that cyber staff had left for lifestyle reasons. We specifically asked about burnout in the qualitative research this year. A few employers felt that burnout was not really an issue in their organisation. They said they ensure staff do not work long hours and take leave regularly. For other employers, burnout was more of a concern. Incident response and recovery roles and sales jobs were highlighted as being particularly pressurised. One recruitment agent thought that as cyber security has become more high profile, the pressure on senior leaders has increased. They had seen people leave senior leadership roles because of this to go back into technical lead roles.
I first saw it [burnout] start to rear its head about six or seven years ago. I think that comes from the increased awareness of cyber within organisations, the fear that companies don’t want to be that next company on the front page of a paper or the victim of a ransomware attack. So, people can feel like it’s very much a 24/7 role, that your head is going to be on the chopping block if there is a breach.
Employers tried to mitigate the risk of burnout by ensuring staff have downtime and go on leave. Some had put in place wellbeing resources such as mental health support.
With no warning, you’re suddenly asking people to potentially work 100 hours a week for two or three weeks. So, we’ve got quite good protocols in place around monitoring that and making sure that people realise they’ve got someone as a backup so they can take the downtime.” (Cyber sector firm, 1,000 or more employees)
In the qualitative research, we asked employers about their approach to retaining staff. Employers mentioned the opportunity to develop skills through training and working on new tools, offering career advancement, and doing interesting work.
Employers felt that a good workplace culture and feeling part of a team encourage employees to stay with them. Employers used strategies such as giving employees awards, celebrating promotions and offering time off for charity work. One cyber firm highlighted the positive role played by their Environmental, Social and Governance ( ESG ) policy in their work culture.
I think really people stay for the team, it’s the team here. It is not just about the competitive salary, it is also about the culture of the company. The business has a really strong ESG policy. It is not just about coming to work to earn money, it is about coming to work to be part of something bigger.
Some employers said that flexible working and the ability to work at home can be an effective retention strategy.
It is not always about money, it is about giving people good work/life balance.
9. The supply side of cyber security skills
This chapter explores the supply of cyber security skills within the UK. It draws upon the methodologies used in the previous Cyber Skills in the UK Labour Market (2023) research and the UK Cyber Security Recruitment Pool research. These reports estimated the size of the UK cyber security workforce and the upcoming recruitment pool, based on a review of existing literature and wide range of labour market datasets.
In addition, this strand provides statistics on the estimated characteristics of the cyber security recruitment pool in terms of demography, diversity, location, education, earnings, and entry to the cyber security workforce. It also explores routes into cyber security, including higher and further education, apprenticeships, and retraining and reskilling initiatives.
This chapter provides an update to the previous research, using most recent data where available.
9.1 The role of higher education
This section focuses on the latest data on graduate enrolments outcomes from the Higher Education Statistics Authority ( HESA ) and Jisc. The research team made a bespoke data request for cyber security and computer science enrolments and outcomes covering up to the academic year 2021/22 (most recent available).
UK Higher Education provides a considerable range of courses, modules, and opportunities to explore cyber security at both undergraduate and postgraduate level. As the demand for cyber security professionals has grown in recent years, the Higher Education sector has responded through the provision of:
- Dedicated cyber security courses (in cyber security or digital forensics)
- General computer science or computing courses with one or more modules in cyber security
- Non-technical courses with modules in cyber security (e.g. cybercrime modules in psychology)
The National Cyber Security Centre ( NCSC ) has certified several of these degrees at Bachelor’s and Master’s level under the NCSC -certified degrees programme. It has also supported the development of Academic Centres of Excellence in Cyber Security Research ( ACE-CSR ) and Academic Centres of Excellence in Cyber Security Education ( ACE-CSE ).
Table 9.1 shows the number of courses provided by UK Higher Education Institutions in cyber security and computer science (based on unique course titles offered in 2020/21 and 2021/22).
Table 9.1: Number of cyber security and computer science courses and providers (2019/20 and 2020/21 academic years)
Source: Analysis of Jisc / HESA data (2020 – 2022)
This identifies 74 universities providing cyber security undergraduate courses, and 84 universities providing cyber security postgraduate courses in the UK. This is a small increase from 70 and 80 universities respectively in last year’s report. Further, the number of cyber security related courses offered has increased by 4% (from 557 to 580).
The number of universities providing computer science courses has increased and the number of undergraduate and postgraduate courses have also increased by 2% (from 4,691 to 4,788).
Despite smaller increases in the provision of cyber security and computer science courses when compared to previous years, demand for studying cyber security and computer science has increased more markedly in the previous year. Tables 9.2 and 9.3 provide updated figures (from the previous cyber skills research) for student enrolment and graduates in both cyber security and computer science courses for 2021/22.
Table 9.2 shows an increase of 14% in the number of students enrolled in cyber security courses from 2020/21 to 2021/22, while Table 9.3 shows an increase of 7% in the number enrolled in computer science courses. The tables also show that the number of cyber security and computer science graduates have grown by 34% and 26% respectively. This highlights relatively strong growth in cyber security provision at both undergraduate and postgraduate levels, indicating that many higher education institutions are responding to the increasing demand for cyber security professionals in the economy, as well as increased demand among students to learn cyber security skills.
Table 9.2: Breakdown of student enrolment and qualifiers in cyber security courses in UK Higher Education institutions (HEIs, 2020/21 and 2021/22 academic years)
Source: Analysis of Jisc / HESA data (2020 – 2022) (numbers are rounded to the nearest ten, may not sum due to rounding).
Table 9.3: Breakdown of student enrolment and qualifiers in computer science courses in UK Higher Education institutions (HEIs, 2020/21 and 2021/22 academic years)
Source: Analysis of Jisc / HESA data (2020 – 2022) (numbers are rounded to the nearest 10/, may not sum due to rounding).
These tables show that, in the most recent available year (2021/22), the number of individuals enrolled in cyber security courses has increased by 14% and the number of cyber security graduates has increased by 34%.
Furthermore, computer science enrolments have also increased by 7% and the number of computer science graduates has increased by 26%.
Student profiles
This section provides the breakdown of graduates in cyber security and computer science courses for the latest year of available data (2021/22), in terms of gender identity, ethnicity, domicile, age and entry from state schools.
Gender identity
In previous research, there has been a significant gender gap identified within the cyber security industry. Figure 9.1 highlights the gender split at undergraduate and postgraduate level for both cyber security courses and other computer science courses. This highlights that within cyber courses only 14% of graduates at undergraduate level and 24% at postgraduate level identify as female. This suggests a small increase in postgraduate participation from female students since the previous year (3% increase); however, the participation levels remain low compared to both computer science, and wider HE participation.
Figure 9.1: Gender Identity of Cyber Security and Computer Science Graduates (2021/22)
Source: Analysis of Jisc / HESA data (2021/22). Base: Cyber Undergraduates n=3,215, Cyber Postgraduates n=2,561, Computer Science Undergraduates n=24,790 & Computer Science Postgraduates n =23,550
Figure 9.2 highlights that in the academic year 2021/22, at least 19% of cyber security and 14% of computer science students were from ethnic minority backgrounds. There is a small decrease in the proportion of ethnic minority students, with a 3% decrease for cyber security students and a 3% decrease for computer science students from the figures set out in the previous year’s report, albeit this may also be due to the further increase in the proportion with unknown ethnicity.
Figure 9.2: Ethnicity of Cyber Security and Computer Science Graduates (2021/22)
Source: Analysis of Jisc / HESA data (2021/22). Base: Cyber courses, n =5,790 & Computer Science, n =48,440
The following figures explore the domicile (i.e. prior home addresses) of cyber security and computer science students in 2021/22. Figure 9.3 shows that 89% of cyber undergraduate students are from the UK. When compared with figures from the Cyber Recruitment Pool research (2018/19), the ratio of students from the UK (c.90%) has remained consistent in recent years. A closer look at cyber security students at all levels (undergraduate and postgraduate) in 2021/22 shows that 72% of students were from the UK, 25% of students were non-EU, and 3% were from the EU.
Figure 9.3: Domicile of Undergraduate Cyber Security and Computer Science Enrolled Students (2021/22)
Source: Analysis of Jisc / HESA data (2021/22). Base: Cyber courses, n =14,140 & Computer Science, n =103,270
Figure 9.4 highlights that the proportion of non-EU computer science postgraduate students has continued to grow, from 56% in 2020/21 to 64% in 2021/22, surpassing enrolment levels of UK students. Further, the number proportion of non-EU cyber security postgraduate students has risen from 45% to 60%, also surpassing enrolment levels of UK students. This highlights the international attractiveness of the UK as a destination for cyber security and computer science.
Figure 9.4: Domicile of Postgraduate Cyber Security and Computer Science Enrolled Students (2021/22)
Source: Analysis of Jisc / HESA data (2021/22). Base: Cyber courses, n =6,750 & Computer Science, n =52,620
Further analysis shows that of the 1,292 cyber security graduates from the UK who were employed (and provided job role SOC2020 code) at the time of the Graduate Outcomes survey, 96% (1,143) reported that they stayed in the UK to work. This suggests that domestic graduate retention in the cyber security market is stronger than the previous year, where 90% of UK cyber security graduates reported staying in the UK to work.
State School Marker
The marker for ‘state school’ attendance is a useful proxy for exploring the diversity of students entering particular courses. Figure 9.5 sets out the proportion of UK domiciled students enrolled in cyber security and other computing courses. This highlights that at least 75% of students enrolled in cyber security courses are from state school backgrounds, compared to 73% for wider computer science courses. A very small proportion are from privately funded schools. Please note that there is also a significant group of ‘unknown’; many of these students are likely to have attended state-funded schools also.
Figure 9.5: State School Marker – Cyber Security and Computer Science students from the UK – Enrolled in 2021/22
Source: Analysis of Jisc / HESA data (2021/22). Base: UK Domiciled students enrolled in Cyber courses, n =15,110 & Computer Science, n =100,050
At undergraduate level, Figure 9.6 highlights that the 73% of students enrolled on cyber security courses are within the 18 to 24-year age range. However, 26% of undergraduate students enrolled in cyber security courses are 25 or over, and this figure increases to 66% at post-graduate level. This may indicate significant demand among older students or those seeking to upskill in cyber security to do so through the higher education system.
Figure 9.6: Age of Cyber Security (top) and Computer Science (bottom) Students – Enrolled in 2021/22
Source: Analysis of Jisc / HESA data (2021/22). Base: Cyber courses, n =20,890 & Computer Science, n =155,880
Figure 9.7 sets out the percentage of students enrolled in full-time, part-time, and other forms of study by age. This highlights that younger students are more inclined to study full-time, whilst more mature students are likely to study part-time, typically given work or other commitments. This means that exploring sufficient provision of part-time or distance learning opportunities in cyber security for mature students may help to stimulate increased demand.
Figure 9.7: Age of Cyber Security Students – Enrolled in 2021/22 (all levels)
Percentage of Students Enrolled (by age, by level)
Source: Analysis of Jisc / HESA data (2021/22). Base: Full-time (FT), n =16,250; Part-time (PT), n=4,650
Graduate Outcomes
The most recent HESA data on graduate outcomes covers the 2020/21 academic year, based upon the responses to the Graduate Outcomes Survey.
Graduates are asked about their activities within approximately 15 months after they complete their studies, so the responses received can show activity taking place between December 2021 and September 2022 (for those that completed the Graduate Outcome Survey following their studies). Of the 4,429 students that graduated in cyber security courses in 2020/21, just under 50% (2,022) participated in the Graduate Outcomes Survey. Similarly, just over 40% (16,658) of the computer science graduates participated in the Graduate Outcomes Survey.
Figure 9.8 shows the overall graduate outcomes for those that graduated in the academic year 2020/21. The results show that in the most recent year, 66% of cyber security graduates entered full-time employment, and a further 10% of cyber security graduates entered employment and further study. The number of graduates entering full-time employment is higher than the levels seen in the previous year, while the number entering employment and further is lower (60% and 11% respectively). A further 7% entered part-time employment.
This means that, of the c.4,400 students that graduated in cyber security in 2020/21, and for the c.5,800 cyber security graduates in 2021/22, we estimate that approximately 85% of these will enter the labour market within 15 months. We explore sectors and roles for these graduates in subsequent subsections.
We also note that 7% of cyber security graduates were unemployed within fifteen months of graduating. This compares to 5% across all graduates [footnote 16] , potentially indicating a recurring challenge with respect to ensuring that cyber security graduates have the soft skills and interview skills, as well as ability to pass technical tests often required to secure a graduate role.
Figure 9.8: Overall Graduate Outcomes (2020/21 academic year)
Source: Analysis of Jisc / HESA data (2020/21). Base: Cyber courses, n = 2,020 & Computer Science, n =16,660
Employment outcomes
Using the Standard Occupational Classification ( SOC ) codes for the 2020/21 academic year, we can understand the most popular careers for cyber security graduates. Figure 9.9 displays the top job roles, based on the proportion of cyber graduates in each role.
The data highlights that 30% of cyber graduates are employed in cyber security professional roles; this has remained relatively consistent from the 2019/20 academic year and may demonstrate continued use of the new SOC code for ‘cyber security professionals’, as well as more focused employment outcomes.
The proportion of cyber graduates in programming and software development professional roles is lower at 10%, compared to 11% in 2019/20. However, a substantial proportion of cyber graduates move into IT-related roles that may require cyber specific knowledge, and many of those that state they are in ‘programming roles’ etc may ultimately work for cyber security firms.
Figure 9.9: Top job roles based on Standard Occupational Classification ( SOC ) 2020 for cyber security graduates (2019/20)
Source: Analysis of Jisc / HESA data (2020/21). Base: Total Graduates, n=1,530 in FT or PT employment Figure 9.10 displays the top roles for computer science graduates, with 40% of these graduates employed as programmers and software development professionals. The proportion of graduates in this role has decreased from 42% in 2019/20. However, only 1% of computer science graduates from 2020/21 consider that they are employed in cyber security professional roles (not shown on chart below). While this reflects an important inflow, it does highlight the continued race for talent across a wide range of digital sectors for computer science graduates.
Figure 9.10: Top job roles based on Standard Occupational Classification ( SOC ) 2020 for computer science graduates (2020/21)
Source: Analysis of Jisc / HESA data (2020/21). Base: Total Graduates, n=12,700 in FT or PT employment With respect to the cyber recruitment pool, using the Graduate Outcomes Survey estimates, we assume that the following number of Higher Education graduates may be likely to enter IT and cyber security roles each year (Tables 9.4 and 9.5 below)
Table 9.4: Estimated number of graduates moving into IT-related roles
Table 9.5: Estimated number of graduates moving into cyber security professional roles ( SOC 2135)
This data suggests that the volume of graduates moving into IT roles has increased by c.7,000 (+31%) since last year’s report. Further, the volume of graduates in ‘SOC2135 Cyber Security Professional’ roles has increased by c.300 (+28%) since last year.
The number of graduates moving into ‘SOC2135 Cyber Security Professional’ roles has increased from 1,150 by 28% to 1,470 in the last year. The previous report estimated that up to 4,000 graduates were likely to enter the broader cyber security labour market each year. This is because the SOC 2135 code is likely to significantly underestimate the volume of cyber security professionals (e.g. individuals working in cyber security related roles in programming, networks, consultancy etc).
This means the response they provide for their current role in the Graduate Outcomes Survey may be coded into another area (such as programming or consultancy) even if their role is cyber security focused.
We note the increase in the number of IT and cyber security graduates and can therefore estimate that c.5,000 graduates from the Higher Education sector may enter the broader cyber security labour market.
Analysis of Graduate Outcomes data also indicates salary bands for those in full-time employment. Figure 9.11 suggests that cyber security and computer science graduates have similar earnings, with median earnings in the £25,001 - £30,000 range in the 15 months after graduating. This is consistent with the previous year.
Figure 9.11: Reported Salaries by those in full-time equivalent employment (2020/21 academic year)
Source: Analysis of Jisc / HESA data (2020/21). Base: Cyber courses, n =1,030 & Computer Science, n =8,280
Figure 9.12 also explores the reported salaries for graduates in cyber professional roles. The median salary for cyber and computer science graduates in cyber professional roles is within the £30,000-£35,000 salary band, highlighting a wage premium at graduate level. Further, there are a higher proportion of cyber graduates receiving higher salaries (e.g. over £70,000) when looking specifically at cyber professional roles.
Figure 9.12: Reported Salaries by those in full-time cyber professional roles (2020/21 academic year)
Source: Analysis of Jisc / HESA data (2020/21). Base: Cyber courses, n =320 & Computer Science, n=120
9.3 Estimating the size of the cyber security recruitment pool
The previous Cyber Skills in the UK Labour Market (2023) research drew an estimate of c.133,400 cyber security professionals working in the UK. This section revisits and updates the previous estimate, using updated data from the last 12 months. In order to create this estimate, we have reviewed various data sources, covered in this section.
We estimate that the current cyber security workforce has risen to c.136,800 FTEs in 2023. DSIT Cyber Security Sectoral Analysis (2024) workforce estimate
Since 2017, DSIT has tracked the size and scale of the UK’s cyber security sector within the Cyber Sectoral Analysis. Whilst this only covers full-time equivalent ( FTE ) employment related to cyber security roles, it provides a useful indicator of the scale of the number of jobs within private sector firms that trade in cyber security products and services. The relevant figures from all published sectoral analyses to date are shown in Table 9.6.
In the most recent year, employment growth in the cyber security sector has been slower than in previous years, with an estimated growth rate of 5%, compared to double-digit growth in previous years (outside 2020).
Whilst there is overall employment growth in the cyber security sector, we note that some of the largest cyber security firms (in line with the broader tech industry) have announced employee layoff rounds (typically in the range of 5-10% [footnote 17] ) in 2023.
Table 9.6: Number of FTEs in the UK Cyber Security Sector, 2017 to 2023
ISC2 Cybersecurity Workforce Study
The 2023 ISC2 Cybersecurity Workforce Study suggests there are c.367,300 (+8.3% from 2022) individuals in the UK cyber security workforce, with a shortage of c.73,400.
It is not possible for us to validate their estimate with our data, given the differences in methodologies between our two studies (outlined later in this section) and limited published technical information on the UK sample size and representativeness of the ISC2 data. The estimate may also be likely to have a margin of error around it.
Cyber Security Workforce Estimates
The ONS has recently updated the Standard Occupation Classification system to ‘SOC2020’, which includes job classifications for ‘Cyber Security Professionals’ under SOC Code 2135. The Annual Population Survey [footnote 19] (October 2022 – September 2023) provides an estimate of the number of employee jobs in the UK under SOC2135 (Cyber Security Professionals).
This estimates that there 58,200 employee jobs under SOC2135. However, this is within the context of 1,468,200 IT Professionals ( SOC 213), where many employees working in a cyber-related role may be alternatively coded until areas such as IT project managers, programmers and software developers, network engineers, and wider quality and testing staff.
As such, the employee jobs estimate of 58,200 provides a highly useful sample of cyber security professionals; however, may underestimate the true prevalence of cyber skills and cyber professionals across the UK economy.
This means that our research team seek to estimate the size of the UK’s cyber security workforce using the data from the Annual Population Survey, the DSIT Cyber Security Sectoral Analysis research, job vacancy analysis, and wider modelling.
Within the 2023 Cyber Skills in the UK Labour Market research, this estimated that “as a conservative estimate, we estimate there are c.133,400 in the cyber security workforce as of end of 2022.”
Updating this for 2023, we estimate:
- We maintain the 2022 workforce estimate of 133,400 individuals as of the end of 2022.
- We assume an inflow figure (new people to the industry) of 8,100 individuals in 2023.
- We assume an outflow figure of 4,700 people, based on up to 3.5% of cyber security employees leaving the sector in a given year due to retirement or exit.
- This suggests an estimated cyber security workforce of 136,800 individuals as of end of 2023.
Exploring all graduates within Cyber Security Roles in the UK
An additional bespoke data request was made for graduates who are employed in roles under the SOC213 (IT) code and SOC2135 (Cyber Security Professionals) across all degree pathways.
The purpose of this search is to identify graduates from any discipline (i.e. outside of cyber security or computer science courses) that are working in a cyber security role within fifteen months of graduating.
This data request covered a sample size of 765 graduates that completed the Graduate Outcomes Survey and identified their employment status under the SOC2135 code (cyber security professionals). This highlights that:
- 59% of these students studied a Cyber Security course
- 17% studied Computing or Computer Science course
- 17% studied a STEM related course (Science, Technology, Engineering and Maths)
- 4% studied Accounting, Business, Economics and/or Finance
- 3% studied Humanities and/or Social Sciences
**Figure 9.13: Graduate course of Cyber Security Professionals (2020/21 academic year)
Source: Analysis of Jisc / HESA 2 data (2020/21). Base: 765 Cyber Security Professionals; Cyber courses, n =449; Computer Science, n =130; STEM, n=132; Accounting, Business, Economics & Finance, n=33; Humanities & Social Sciences [footnote 20] , n=21.
As such, Figure 9.13 suggests that although a substantial proportion of cyber security professionals come from cyber security, computing and computer science backgrounds, graduates from other disciplines are contributing to the cyber sector. This highlights the potential in encouraging graduates from a wide range of pathways into the cyber security profession, as well as post-graduate reskilling bootcamps.
9.4 The role of further education
As set out within the DSIT Cyber Recruitment Pool research, Further Education (FE) is an increasingly important route for students as they progress into industry or further study. Within the UK, many students who go on to study Cyber Security (or broader IT or computing courses) may undertake FE courses in IT, Computing, or Programming – which may include elements of cyber security within the syllabus. This previous research highlighted that more than 50,000 students enrol each year on Level 3 class-based courses in the ICT subject area in England, of which approximately 60% study for a Diploma, c.25% for an A-Level qualification, and the remainder for Certificates or BTEC qualifications.
The subsequent sections explore the supply of talent into the cyber security labour market through routes such as apprenticeships, retraining and upskilling programmes, and wider inflows into the labour market (such as migration).
Apprenticeships
Further Education (FE) continues to provide an increasingly important route for cyber security students, introducing them to the basics behind cyber security, networking, and IT. Further Education routes can provide a stepping stone towards a career in cyber security.
Table 9.7 sets out the number of apprenticeship enrolments, starts and achievements in ICT based apprenticeships in the academic years 2021/22 and 2022/23. [footnote 21]
The number of apprenticeship enrolments [footnote 22] in ICT subject areas in England has increased significantly in recent years, rising by 9% from 42,150 in 2020/21 to 46,080 in 2021/22, and rising by a further 14% to 52,510 in 2022/23.
The number of apprenticeship starts [footnote 23] increased by 10% from 22,820 in 2021/22 to 25,100 in 2022/23, suggesting that there continues to be a strong increase in the number of students getting involved in ICT apprenticeships.
Table 9.7: Number of ICT apprenticeships (2020/21, 2021/22) in England
Source: Department for Education (Academic year 2022/23) Apprenticeships and traineeships data Apprenticeships and traineeships data.). [footnote 24]
Table 9.8: Number starts in ICT apprenticeships (2022/23) in England
Source: Department for Education (Academic year 2022/23) Apprenticeships and traineeships data . [footnote 25]
Role of Apprenticeships / Degree Apprenticeships
Table 9.9 sets out the number apprenticeship enrolments, starts and achievements [footnote 26] in England. In 2022/23 there were 580 new starts on cyber security apprenticeships. Therefore, the number of students starting cyber security apprenticeships has increased by 18% in the most recent year.
Table 9.9: Number of degree apprenticeships in England, 2020 to 2023
Source: Department for Education (Academic year 2022/23) Apprenticeships and traineeships data .
The increase in the number of students starting, enrolled in, and achieving qualifications in cyber security focused apprenticeships is highlighted further by Figure 9.14. This emphasises the steady increase in cyber security apprentices over time.
This data highlights that there are 580 new starts into the cyber recruitment pool in England in 2022/23, and this figure will be higher for across the United Kingdom.
Figure 9.14: Number of degree apprenticeships in England, 2020 to 2023
Source: Department of Education Base: 5,120 students who have started, been enrolled in, or achieved apprenticeships in England, 1,440 in 2020/21; 1,670 in 2021/22; 2,010 in 2022/23
Retraining and Upskilling
In addition to qualifications obtained through further and higher education, several employers will also look for potential employees with relevant skills often affirmed through certification and training providers. In recent years, there has been increased emphasis on how certifications and training models can rapidly upskill people to move into or increase knowledge of cyber security roles.
Further, the provision of innovative training models such as cyber security academies and bootcamps, and enhanced access to low-cost online training platforms has also driven interest in cyber security training.
As mentioned in Section 2.4, within the business survey of 180 cyber sector firms, among qualified staff:
- 42% of staff held a specialist higher education qualification (e.g. a degree) related to cyber security
- 38% of staff held a general computer science / IT degree
- 18% of firms had staff that held a cyber security apprenticeship
- 10% were qualified through another apprenticeship role
- 72% of staff held some form of other technical accreditation.
This highlights the importance of a wide range of technical accreditation and apprenticeships, in addition to higher education. The Cyber Recruitment Pool (2021) research explores these routes in depth. The following section sets out updated estimates and commentary where available.
- Certifications: In the UK, as of January 2023, there were approximately 8,500 (ISC)² members in the UK holding the CISSP certification (an increase of 8% since January 2021. CompTIA is also a prevalent certification provider, offering Network+, CySA+, Security+, PenTest+ and more. As of 2023, over 700,000 professionals have earned the CompTIA Security+ certification globally.
- Retraining and Upskilling Initiatives: The UK is home to a range of retraining and upskilling initiatives. This includes providers such as Immersive Labs, Capslock, QA, SANS and more, as well as online provision. Last year’s report noted that there is limited data available on the quantification of these routes; however, it is possible that up to 1,500 individuals may currently enter the recruitment pool through this route. This is based upon knowledge of a number of initiatives identified across the UK e.g. Assured Skills Academies, funded skills initiatives, Career Transition Partnership etc.
- Armed Forces: Over 14,000 individuals leave the Armed Forces each year. In 2021/22, over 10,000 service leavers used support from the Career Transition Partnership (a scheme to support leavers into employment). Of these, 477 entered Science, Research, Engineering and Technology Professional roles in 2021/22 , of which 74 reported a role as a ‘Cyber Security Professional’ under SOC2020. This is an increase of 32% (from 56 in 2020/21 to 74 in 2021/22).
- Attracting international talent: In addition to upskilling the population, the cyber security recruitment pool can also be increased through exploring the UK’s capacity to attract international talent and encourage global knowledge transfer. The Global Talent Visa programme has approved c.2,300 visas (between Jan 2020 – August 2021), and includes researchers and employees coming to the UK to engage in cyber security activity. However, we do not have a granular breakdown of these figures.
Last year’s report estimated these four routes could be generating in the region of c.2,500 individuals into the cyber recruitment pool each year. We retain this estimate as a conservative figure, given the limitations with respect to granular level data.
In summary, we estimate that the UK inflows into the cyber security recruitment pool have improved within the last twelve months, growing from 7,000 workforce entrants in 2022 to 8,100 in 2023. This consists of:
- Approximately 5,000 graduates from cyber security, computer science, or other HE courses (an increase from 4,000 in the previous report)
- Approximately 2,500 individuals through retraining, reskilling, career conversion, or international migration
- At least 600 new apprenticeship starts (in England).
In Section 6.1, we reported findings from the qualitative research on employers’ perceptions of the advantages and disadvantages of recruiting entry level roles and apprenticeships.
9.5 Estimating the Cyber Workforce Gap
The previous cyber recruitment pool research indicated a shortfall of c.11,200 individuals per year in the cyber security workforce – referred to as the annual ‘cyber workforce gap’. To note, this is different to the skills gaps and skills shortages discussed in Chapters 4 and 6.
This year, we revise this estimate based on the latest data to 3,500 individuals a year. The constituent parts of this calculation are as follows, bringing together the estimates from the rest of this chapter:
- For 2023, we estimate the current workforce to be in the region of 136,800 individuals.
- We estimate that a total of c.8,100 individuals entered the cyber security workforce in 2023. This encompasses the c.5,000 entering from Higher Education (Section 9.1), up to 2,500 undertaking career conversion, retraining, or entering the UK pool elsewhere, and up to 600 involved in apprenticeships in cyber security.
- As Chapter 9 shows, up to 3.5% of cyber security employees leave the sector in a given year. This provides an estimate of c.4,800 leavers each year.
- Employment in the cyber security sector has increased by 5% within the last year according to the DSIT Cyber Sectoral Analysis 2024. This suggests a need for c.6,800 new people in 2024 to meet demand, in addition to the c.4,800 to replace those exiting the sector, i.e. a total supply requirement of c.11,600 per year for the cyber security workforce.
- Taken together, these findings suggest a net annual shortfall of c.3,500 people (i.e. the UK market requires at least an additional 11,600 individuals, but only 8,100 are entering the workforce each year).
- This is smaller than the previous gap estimate of c.11,200 individuals; however, this is driven by both supply and demand factors. At the supply side, the UK has improved with respect to cyber security related graduate supply in the most recent year. However, as shown by the vacancy analysis and the sectoral analysis, demand for cyber security professionals remains high but was lower in 2023 than in previous years. We also note that this is an ‘annual estimate’ only. The overall skills gap remains persistent, and annually cumulative in effect.
Figure 9.15 provides a visual summary of this workforce gap for 2023.
Figure 9.15: Summary Diagram of the ‘Cyber Workforce Gap’
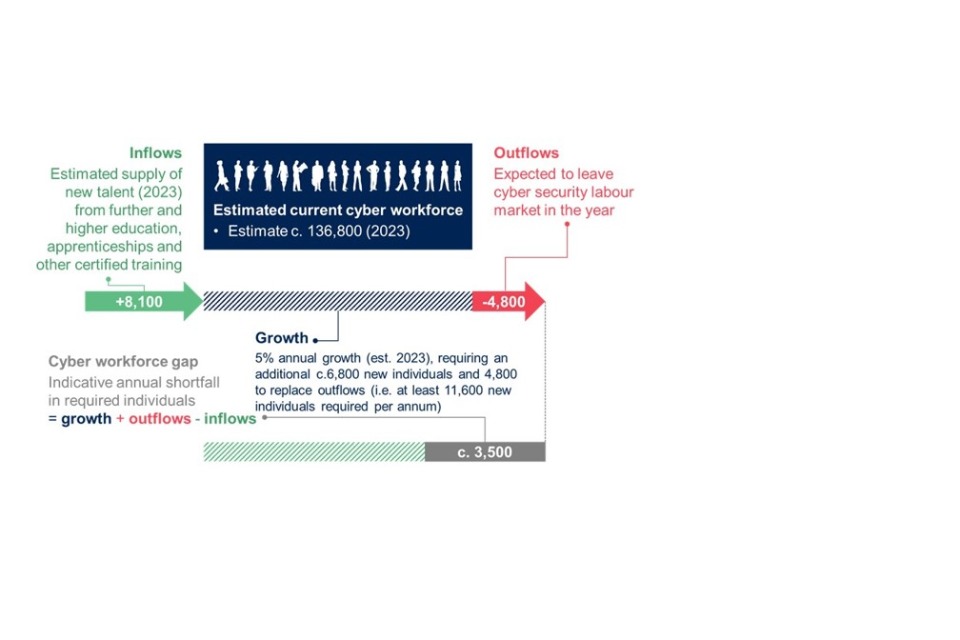
10. Conclusions and recommendations
Our study provides a comprehensive picture of the supply side and demand side of UK cyber skills gaps and shortages and how the cyber security labour market is evolving. The key insights from this 2024 report are as follows:
Demand for cyber security professionals has slowed, although the sector is more resilient than the wider digital sector. The slowing of demand observed in the second half of 2022 has continued through 2023. Core cyber job postings decreased by 32% and ‘all cyber roles’ by 39%. This decline in demand may be due to wider macroeconomic conditions, along with broader technology layoffs worldwide. In the qualitative research, recruiters attributed the softening market to budgetary constraints because of the economic outlook, as well as the market readjusting after a post-COVID spike in demand. Our estimate of the cyber workforce gap – the annual shortfall in cyber security personnel – has decreased to c.3,500 people compared to last year’s estimate of c.11,100. This is due to a smaller growth rate of the workforce, but also a welcome increase in the supply of cyber security graduates. However, the gap remains persistent and annually cumulative in effect. In other words, even though the workforce gap has decreased this year, the total shortage of cyber security professionals continues to grow each year as the unmet demand from previous years accumulates.
Basic and advanced skills gaps are consistent but the proportion of businesses lacking confidence in their incident management skills continues to rise. Over the six years this survey has run, we have consistently found that around half of businesses have a basic skills gap and around three in ten have an advanced skills gap. Among businesses that do not outsource incident management, almost half (48%) are not confident that they would be able to deal with a cyber security breach or attack. The proportion lacking confidence has steadily increased over time; in 2020 it stood at 27%. This may well be, in part, because of perceptions that the threat landscape is increasingly challenging to navigate. Cyber leads have consistently raised this in the qualitative research, and this year in relation to AI in particular, as it can enable attacks which are quicker, much greater in number and increasingly sophisticated. This highlights the importance of cyber leads making the case to boards and senior leaders for investing in cyber security skills and tools.
The workforce within the cyber sector continues to have a high prevalence of generalists. For the second year, the quantitative research estimates the proportion of the workforce within cyber sector firms that carry out each of the cyber security specialisms aligned to the UK Cyber Security Council’s Cyber Career Framework. A majority (62%) of the workforce are cyber security generalists. In a new question this year, we found that 83% of firms with employees in a generalist role thought their responsibilities involved advising staff on cyber security risks and controls, while half (51%) thought generalists were responsible for briefing and training non-cyber staff on cyber security awareness and safe practice. In the qualitative research, we heard two different understandings of what a ‘generalist’ is; a single person or team with a wide range of cyber security responsibilities or a senior person such as a chief security officer or consultant who has to work across the whole field. Beyond this, the distribution of cyber security roles in the sector is not skewed towards one specialism. In the non-cyber workforce, generalists predominate, as teams are often small and 84% of staff in the private sector with cyber responsibilities have absorbed these tasks into an existing role.
There is evidence of a shift away from remote working. We estimate that 22% of job postings for core cyber roles had no regional location listed (i.e. the roles were marked as ‘Remote’ or ‘UK-wide’), which is down from 28% in 2022, although still higher than 2020 (13%). In the qualitative research, we heard that employers are increasingly asking cyber staff to be office-based, which places geographical restrictions on the available talent pool. As demand for cyber professionals has slowed, the market has become less candidate-driven; recruitment agents felt there can be a mismatch between what employers and employees want in terms of in person working. Organisations which struggle to compete on salary could potentially attract candidates by offering remote working. This could be particularly relevant for public sector organisations; in the qualitative research, employers and recruiters consistently highlighted salary as a problem for recruitment and retention.
Lack of workforce diversity remains consistent – widening the talent pool continues to be a key challenge. The proportion of women and disabled people in the cyber workforce continues to be lower than both the UK workforce as a whole and the digital workforce. The percentage of the cyber workforce from ethnic minority backgrounds is in line with the UK workforce but there is evidence of a downward trend over time. In the qualitative research, we again heard that a lack of diverse candidates is a significant challenge. One continuing difficulty in diversifying the talent pool is that the gender gap for cyber security courses remains wide, with only 14% of female graduates at undergraduate level, and 24% at postgraduate level.
Entry level roles and apprenticeships can help fill skills gaps, diversify the workforce and build a skills pipeline for the future. In the qualitative research, we found that employers can see clear benefits to recruiting entry level staff and apprentices but the downsides can be significant, particularly for smaller organisations. This helps to explain the consistent finding in the survey and job postings analysis that staff with mid-level experience are more sought after. On entry level roles, employers would like to understand potential career pathways and what training resources and funding are available. For apprenticeships, employers would welcome financial help such as funding or tax incentives, as well as information on the benefits of cyber apprenticeships and practicalities such as finding training providers, putting apprentice programmes together and any available support.
The UK Cyber Security Council’s Cyber Career Framework has a positive role to play in addressing skills challenges. The Cyber Career Framework was well received in the qualitative research as a tool which can help both employers and individuals understand potential career pathways within cyber security. There are a range of retraining and upskilling initiatives available in the UK which can enable individuals with transferable skills to transition into cyber roles, and, as we have discussed above, the number of cyber security graduates and apprentices is rising. The Cyber Career Framework can be used to build a shared understanding between individuals, employers, and educational providers on the content of courses. Few employers or recruiters taking part in the qualitative research had come across the Cyber Career Framework, so its profile needs to be raised.
AI has the potential to transform the cyber skills landscape. The qualitative research highlighted the far-reaching impact AI could have on the labour market. Increasing automation could lead to some jobs disappearing, while skills need to evolve so that organisations can use AI cyber security tools effectively. There may be risks in relying on these tools if they are not adequately understood or managed. Other anticipated changes were existing roles becoming ‘ AI cyber’ rather than just ‘cyber’ and new niches and deep specialisms emerging. While there is uncertainty about how exactly AI will modify the skills landscape, it is clear that training and recruitment will need to adjust to reflect the changes it brings about.
Implications
In our 2021 report , we set out a series of recommendations which were developed with input from government and industry stakeholders. These recommendations focused on three broad areas:
- Influencing attitudes and behaviours among board members and wider staff in respect of cyber security.
- Mapping cyber security career pathways and enabling IT staff to gain cyber security skills or transition into cyber specialist roles.
- Increasing diversity in the talent pool, improving career progression into senior roles for diverse groups and encouraging more entry-level recruitment.
Our findings suggest that all these areas of focus remain important. We highlight the significant role the UK Cyber Security Council’s Cyber Career Framework has to play.
In this year’s study, we have seen some shifts in the cyber skills landscape. Supply has grown while demand has cooled because of macroeconomic factors and wider redundancies and recruitment freezes in the digital sector. However, there continues to be a ‘gap.’
Furthermore, the need for cyber security skills is likely to grow as the threat landscape continues to broaden. In the qualitative research, cyber leads and recruiters highlighted how AI could result in quicker, higher volume and increasingly sophisticated attacks. Further, business adoption of AI may result in new risk vectors e.g. increased need for API (Application Programming Interface) security, as businesses increase integration of third-party solutions and cloud infrastructure. We expect that the UK will need more cyber specialists across multiple domains to help identify and manage this risk.
This year’s study therefore highlights some further implications for government and industry:
- The entry-level pipeline needs to be developed if the market continues to cool. Retaining this talent makes it more of a priority to find ways to encourage prospective employers to take on entry-level cyber staff. There may also be opportunities for increasing entry level routes via the public sector and initiatives such as the Cyber Advisor scheme, to help widen adoption of cyber security across the economy, and provide opportunities for entry-level talent to work across industry
- Skills relating to AI in cyber security will be increasingly important for employees and organisations. This potentially has wide ranging repercussions for training and recruitment, as well as helping organisations understand how to buy and implement AI -related cyber security services.
- The placement and retention of relevant graduates needs careful consideration. Higher education institutions have responded positively to cyber security market demand in recent years and have increased supply. As well as providing a sufficient pipeline for industry and the public sector, there also needs to be resources in the public sector and academia to work on ‘bleeding-edge’ areas such as hardware security and address areas of cyber security under-provision across the economy (e.g. increasing adoption among charities, SMEs, and critical infrastructure).
- Pathways to industry employment could potentially be broadened. In order to address the changing threat landscape, it could be beneficial to find ways to support cyber start-ups from wider domains or which are addressing niche challenges. This may also include further supporting routes to encourage entrepreneurialism and start-ups in the cyber security sector.
Annex: Ipsos standards and accreditations
Ipsos’ standards and accreditations provide our clients with the peace of mind that they can always depend on us to deliver reliable, sustainable findings. Our focus on quality and continuous improvement means we have embedded a “right first time” approach throughout our organisation.
This is the international market research specific standard that supersedes BS 7911/MRQSA and incorporates IQCS (Interviewer Quality Control Scheme). It covers the 5 stages of a Market Research project. Ipsos MORI was the first company in the world to gain this accreditation.
This is the international standard for information security designed to ensure the selection of adequate and proportionate security controls. Ipsos MORI was the first research company in the UK to be awarded this in August 2008.
This is the international general company standard with a focus on continual improvement through quality management systems. In 1994, we became one of the early adopters of the ISO 9001 business standard.
Market Research Society ( MRS ) Company Partnership
By being an MRS Company Partner, Ipsos MORI endorses and supports the core MRS brand values of professionalism, research excellence and business effectiveness, and commits to comply with the MRS Code of Conduct throughout the organisation.
Data Protection Act 2018
Ipsos MORI is required to comply with the Data Protection Act 2018. It covers the processing of personal data and the protection of privacy.
HMG Cyber Essentials
This is a government-backed scheme and a key deliverable of the UK’s National Cyber Security Programme. Ipsos was assessment-validated for Cyber Essentials certification in 2016. Cyber Essentials defines a set of controls which, when properly implemented, provide organisations with basic protection from the most prevalent forms of threat coming from the internet.
Ipsos is signed up as a ‘Fair Data’ company, agreeing to adhere to 10 core principles. The principles support and complement other standards such as ISOs, and the requirements of Data Protection legislation.
This summary predominantly focuses on businesses. ↩
For this study (e.g. in question wording), we defined neurodiversity as the inclusion of people with conditions or learning disorders such as autism, Asperger syndrome, dyslexia, dyspraxia and attention deficit hyperactivity disorder (ADHD). ↩
Please note that the proportion of disabled people in the cyber workforce was introduced from 2021 onwards. ↩
Gender, ethnicity and disability comparison data comes from DCMS Sectors Economic Estimates . We use the July 2022 to June 2023 data. ↩
Please note that the question about the proportion of diverse workforce in senior roles was introduced from 2021 onwards. ↩
The survey focused on activity over the 18 month period prior to the interview. ↩
The business population data is taken from the BEIS Business population estimates in 2022 , which estimates 1,447,900 private sector businesses with employees, This is the latest estimate as of the publication of this report. For the extrapolated figures presented here and later in this chapter, we have rounded to 3 significant figures. These figures are of course subject to a margin of error, as with all the results from the survey. The margin of error for businesses on this result is ±2-4 percentage points. We have not made the same kind of extrapolation for charities or public sector organisations, given the relatively small sample sizes for these 2 groups. ↩
Section 2.3 explores what generalist roles involve. ↩
Of the 48,492 job postings, 10,480 (22%) did not have a known regional location. ↩
The Location Quotients are calculated using the total workforce jobs for a local authority region. The average demand is set at 1.0. A higher Location Quotient indicates that the demand for core cyber employees is higher than the UK average. Please note that the data within this year’s report is available for Local Authority level. ↩
We have categorised the top 50 job titles appearing in the data. This covers 17,560 of the total 48,492 core job postings for the latest 12-month period. We have categorised the top 50 into key cyber job titles, and wider review of the data suggests that Figure 7.5 is considered to be representative of wider job titles for cyber security roles. ↩
This is relatively consistent with the previous year, where 44% of core cyber job postings with sector data from January to December 2022 were posted by recruitment agencies. ↩
Human health activities typically refer to the health and social care sector – the NHS is the largest employer of cyber security roles within this sector. ↩
This is sourced from the Office for National Statistics (ONS, 2023 provisional data) Annual Survey of Hours and Earnings. ↩
Comparing the 2023 median for core cyber job postings (£55,000) with the 2023 median for all IT postings (defined as SIC 62, getting a provisional median of £44,100) ↩
https://www.hesa.ac.uk/news/31-05-2023/sb266-higher-education-graduate-outcomes-statistics ↩
https://techcrunch.com/2023/12/30/cybersecurity-not-immune-brutal-layoffs-2023/ ↩
Estimated by Perspective Economics in the UK Cyber Security Sectoral Analysis annual estimates using historic CAGR figures. ↩
https://www.nomisweb.co.uk/datasets/aps218/reports/employment-by-status-and-occupation?compare=K02000001 ↩
Humanities and Social Sciences include (but are not limited to) courses such as history, philosophy and religion, political sciences, art, and modern languages. ↩
In Tables 9.7, 9.8, 9.9 and Figure 9.14, numbers have been rounded to the nearest ten due to statistical disclosure control. ↩
Apprenticeship enrolments are the count of enrolments at programme level for each academic year – learners will be counted for each apprenticeship they take and therefore, learners may be counted more than once. ↩
Apprenticeship starts are the count of apprenticeship programmes that begin in an academic year, showing the take-up of programmes – it is important to note that an apprentice is counted for each apprenticeship they start at a provider. Therefore, there could be some duplication. ↩
Source: Department for Education (Academic year 2022/23) Apprenticeships and traineeships data. ↩
Note: low values (less than 10) have been rounded down to 0 due to statistical disclosure control. ↩
Apprenticeship achievements signify a learner reaching the end point of assessment; this is not necessarily the same as the end of their learning/apprenticeship. ↩
Is this page useful?
- Yes this page is useful
- No this page is not useful
Help us improve GOV.UK
Don’t include personal or financial information like your National Insurance number or credit card details.
To help us improve GOV.UK, we’d like to know more about your visit today. Please fill in this survey (opens in a new tab) .

Senior Pass
If you are of eligible age and live in South Yorkshire, you can apply for a Senior Pass.
- Live in South Yorkshire
- from your 66th birthday
You can apply for your pass online up to 2 weeks in advance of when you qualify.
Please visit gov.uk to check when you’re eligible for a Senior Pass.
Free travel on local bus services and trams within South Yorkshire between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays
Half fare on Northern train services ( does not apply to advance purchase tickets/fares, only applicable to single and day returns ) for travel between stations on the South Yorkshire rail network between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays
Free travel on buses in all other parts of England between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays. (This pass is not valid on tram services outside South Yorkshire.)
Free of charge (first issue)
Free travel on Stagecoach services to hospital appointments before 0930 - please visit the Stagecoach website for further details.
Please be aware that no pass means that you could pay full fare.
Passes will be renewed automatically and will arrive 4-6 weeks before your current pass expires.
If your pass hasn’t arrived 4 weeks before your current pass expires, please let us know by emailing [email protected] or by calling 01709 515151.
- If you have changed address since your last pass was issued, please complete the Change of address form
- Email at [email protected] stating your full name, post code and date of birth. The photograph must be sent as a JPEG or JPG file
If you need to update your photo and it is less than 8 weeks before your pass expires you will need to apply for a new pass.
Apply online
Set up a MyTSY account in your name (or log in if you already have an account)
Log in > Select Passes from the top menu > Concessions > Senior Pass
Complete all personal details and upload proof documents - visit our ‘What you need to apply’ guidelines page
Upload your photo – see the ‘Acceptable Photograph’ guidelines page as an unsuitable photo could delay your application
Check your order and go to checkout.
If all the details are correct your pass will be dispatched within 11 days of receiving your completed online application.
Apply now >>
Apply by post
Download an application form (PDF, 511Kb)
Complete all personal details and post to the address below together with a photograph and photocopies of proof documents - see 'What you need to apply' guidelines page Contact Centre Traveline 11 Broad Street West Sheffield S1 2BQ
If all the details are correct your pass will be dispatched within 25 days of receiving your completed application form.
Please note proof documents must be photocopies and not original documents as all documents are destroyed once the pass is ordered.
A completed application form can also be submitted by dropping it off at the Customer Service Desk at your local Travel South Yorkshire Interchange .
We can now block lost or stolen passes to prevent further use.
To replace a lost or damaged pass, there is a £7 replacement fee. Stolen passes can be replaced free of charge if you have a Crime Reference Number from the Police.
- Passes applied for through MyTSY can be replaced by logging into your MyTSY account
- Passes applied for by post can be replaced by calling Traveline on 0800 952 0002.
Your replacement pass will be posted to your home address and should be sent to you within 11 days.
Pass Protection can be taken out against Senior Citizen Passes for £5 for the duration of your pass, up to five years.
This will enable you to replace your old pass free of charge should you lose it during the time in which it is valid.
Please read the Pass Protection Terms and Conditions document (PDF, 406Kb) before applying.
- Change of address form
- Senior Pass leaflet (PDF, 264Kb)
- Conditions of use - concessionary pass (PDF, 411Kb)
- Pass Protection - terms and conditions (PDF, 80Kb)
Useful links
Other useful pages you may be interested in: Pass FAQs Contact us What you need to apply

- Smart Cards
- Concessions
- Report something
Loading, please wait...
Have You Considered
- Latest news
- Competitions and offers
- Service changes
- Accessible transport
- Park & Ride
- Walking and cycling
Travel Tools
- Journey planner
- Tickets and passes
- Timetable finder
- Live departures
- Disruptions
Useful Links
- MyTSY Account
- School travel
- Smartcard tickets
- South Yorkshire Mayoral Combined Authority (SYMCA)
Keeping In Touch
- Sign up for our newsletter
- Like us on Facebook
- Follow us on Twitter
- Subscribe to our YouTube channel
- Get timetable updates
- Terms of use |
- Privacy |
- Accessibility |
- Sitemap |

IMAGES
VIDEO
COMMENTS
Your Disabled Pass will entitle you to free travel at all times on: Local bus services, trams and trains* within South Yorkshire. Northern train services* between South Yorkshire and West Yorkshire. Note that your pass is not valid for train journeys wholly within West Yorkshire. Either your boarding or alighting station must be in South Yorkshire.
Tickets and passes Travel Pass FAQs What you need to apply Zoom Travel Passes Zoom Under 16 Travel Pass Zoom 16-18 Travel Pass Zoom Beyond 18-21 Travel Pass Zoom Zero Travel Pass Student tickets Senior Pass Disabled Pass Capped fares 1, 7 and 28 Day tickets Flexi5
Proof of identity documents we accept for all passes (see additional guidance for Disabled and Disabled + Carer further down this page): Birth certificate - scanned copy or photo of the certificate uploaded. Passport identifier - the 28 characters on the bottom line of your passport e.g. 1041211587GBR0205169F1604120. Driving licence number.
Apply for a Disabled Person's Travel Pass. Travel passes are issued free of charge by Travel South Yorkshire and entitle the holder to free travel within South Yorkshire on: local bus services, trams and trains. Northern Rail services between South Yorkshire and West Yorkshire. buses throughout England at off-peak times (these are between 9 ...
Within South Yorkshire your ENCTS Disabled Person's pass will entitle you to free travel at all times on: Northern train services between South Yorkshire and West Yorkshire. In all other parts of England, South Yorkshire passes can be used for free travel on bus services between 0930 and 2300 weekdays and all day weekends and Bank Holidays.
A disabled person's travel pass entitles people to free travel at all times within South Yorkshire on: local bus services, trams and trains. Northern Rail services between South Yorkshire and West Yorkshire. buses throughout England at off-peak times (between 9.30am and 11pm weekdays, all day at weekends and on bank holidays) You can't use your ...
The pass entitles the holder tofree travel on buses, trains and trams across South Yorkshire and other areas. You must meet the qualifying conditions outlined on the Disabled Person's Bus and Train Pass page.Please read these before submitting an application.If you want to help with parking accessibility, you need to apply to the Blue Badge Scheme.
under 16 year old. aged 16-18 years. need to use public transport to get to school. a disabled person. a senior citizen. All of these passes are issued by South Yorkshire Passenger Transport. To apply for the following passes you will need proof of entitlement from your local Council: disabled person's pass. disabled person plus carer pass.
South Yorkshire Mayoral Combined Authority (SYMCA) Keeping In Touch. Sign up for our newsletter. ... ENCTS Disabled Person + Carer £0.00 ENCTS Senior Citizen £0.00 ... £0.00 Zoom 16-18 Travel Pass £0.00 Zoom Beyond 18-21 Travel Pass £0.00 Zoom Under 16 Travel Pass ...
Application for a Disabled Person's national bus travel pass. Please complete using BLACK or BLUE INK and BLOCK CAPITALS. Please attach a recent passport size photo here. No hats, sunglasses or app filters please. Please Note: We aim to despatch your pass within 25 days of receiving your completed application form, 11 days if you apply online.
Including information about senior bus passes. With a Disabled Person's Bus and Train Pass you can travel for free: on buses, trains and trams in South Yorkshire at any time. on Northern Rail trains between South Yorkshire and West Yorkshire. on any off-peak (9.30am to 11pm) and all day at weekends and bank holidays on any local bus journey in ...
Your Disabled Person's Pass will entitle you to free travel at all times on: Note that your pass is not valid for train journeys wholly within West Yorkshire. Either your boarding or alighting station must be in South Yorkshire. Free travel on buses in all other parts of England between 0930 and 2300 on weekdays, and at any time during the ...
If you cannot apply online, contact Metroline to ask about other ways to apply for your pass. Call 0113 245 76 76. You might need to provide a passport style photograph of yourself. If you qualify for a pass it will be sent to your home. If you lose your pass you will have to pay £5 to get a new one.
Within South Yorkshire your ENCTS Disabled Person's pass will entitle you to free travel at all times on: Northern train services between South Yorkshire and West Yorkshire. In all other parts of England, South Yorkshire passes can be used for free travel on bus services between 0930 and 2300 weekdays and all day weekends and Bank Holidays.
Residents with some disabilities may be eligible for a free Disabled pass, which entitles them to free bus services within England and free tram services within South Yorkshire, along with free Northern train journeys between South Yorkshire and West Yorkshire. [3] There is also the +Carer pass, which allows a carer to travel with the pass holder, and the Visually Impaired pass, which allows ...
Can I use my Disabled Pass to travel outside South Yorkshire? A. You can travel for free on buses in all other parts of England between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays.
A Disabled Pass will entitle free travel on many buses, trains and trams. For all the information and how to apply please visit the Travel South Yorkshire website. If you don't automatically qualify for a disabled pass with Travel South Yorkshire, you can apply to Sheffield City Council. If you can prove you meet additional criteria they will ...
If you're aged 18 to 21 and live in South Yorkshire, either permanently or during term time, you can get a Zoom Beyond 18-21 Travel Pass. • Discounted single tickets on First and Stagecoach buses for £1.50, and on Supertram for £2. • Your Zoom Beyond 18-21 Travel Pass will be valid until the day before your 22nd Birthday.
Tel 0114 273 4567 (select option 5) DISABLED PERSON'S TRAVEL PASS. English National Concession Travel Scheme (ENCTS) entitles eligible people to travel as follows: Local to South Yorkshire - free travel on buses, trams and trains across South Yorkshire and on Northern Rail services between South Yorkshire and West Yorkshire.*.
You must live in South Yorkshire; From your 66th birthday; You can apply for your pass online up to 2 weeks in advance of when you qualify. Benefits. Free travel on local bus services and trams within South Yorkshire between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays.
If you use your Travel South Yorkshire account to apply for one of our passes, we will use the information you provide to contact you about your pass for the period it remains valid for. However, at times we may have other offers, events and travel information that we think you might be interested in which we'd like to let you know about.
People from ethnic minority backgrounds make up 15% of the sector workforce, and 9% of those in senior cyber roles (i.e. requiring 6 or more years of experience). 17% of the workforce are female ...
Free travel on buses in all other parts of England between 0930 and 2300 on weekdays, and at any time during the weekend and on Bank Holidays. (This pass is not valid on tram services outside South Yorkshire.) Free travel on Stagecoach services to hospital appointments before 0930 - please visit the. Please be aware that no pass means that you ...
Travel Tools. Journey planner. Tickets and passes. Maps. Timetable finder. Live departures. Disruptions. Useful Links. MyTSY Account. School travel. Smartcard tickets. South Yorkshire Mayoral Combined Authority (SYMCA) Keeping In Touch. Sign up for our newsletter. Like us on Facebook. Follow us on Twitter. Subscribe to our YouTube channel.